A remote code execution vulnerability was discovered in Apache Struts 2. The vulnerability in being tracked via CVE-2018-11776. Upon successful exploitation an attacker can gain remote execution on the target and ultimately take over the target machine. The issue affect all versions of Apache Struts 2, possibly even fixed versions where the settings are mis-configured. Apache has release advisory S2-057 to address CVE-2018-11776. The vulnerability is patched in versions 2.3.35 and 2.5.17.
Vulnerability
When the namespace parameter is not defined in ServletActionRedirectResult, the namespace defined in ActionProxy is used. Due improper checks during parsing, this value is evaluated as an OGNL expression by translateVariables() which may lead to code execution. Object-Graph Navigation Language (OGNL) is an expression language used to for setting and getting Java object values.
The attack is triggered by visiting a URL pointing to the target machine. For successful exploitation two conditions have to be satisfied. Please note the other attacker vectors maybe discovered in the future.
- In Struts config
alwaysSelectFullNamespaceflag is set to true. - The
<action ...>tag has no optional namespace or uses a wildcard to specify the namespace. A PoC is available online for this vulnerability.
To demonstrate the attack we use Apache Struts 2 server ver 2.5.16 on Windows OS. First we modify struts-actionchaining.xml to include the changes shown below.
<struts>
<package name="actionchaining" extends="struts-default">
<action name="actionChain1" class="org.apache.struts2.showcase.actionchaining.ActionChain1">
<result type="redirectAction">
<param name = "actionName">register2</param>
</result>
</action>
</package>
</struts>
And access the target at http://<targetserverIP>:8080/struts2-showcase/${(123+456)}/actionChain1.action.
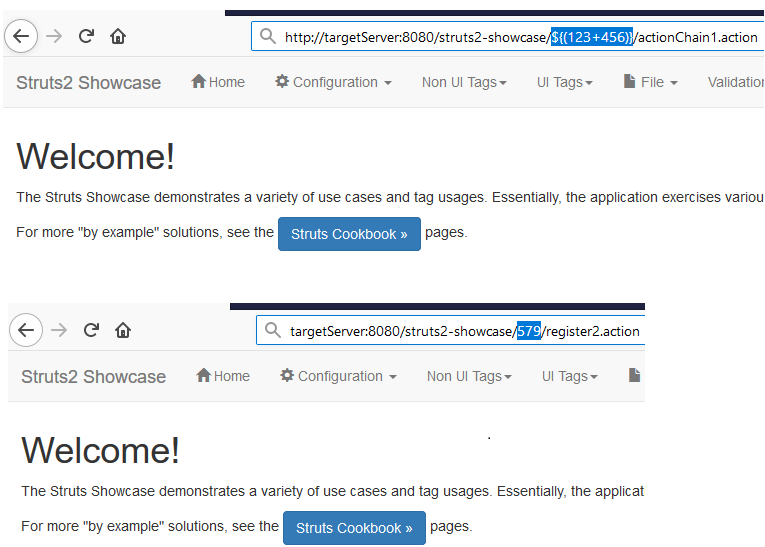
The image shows the HTTP get request and the corresponding response from the server. An attacker can use a proper payload to achieve code execution.
Mitigation
We request organizations to apply the latest patches for Apache Struts 2 as directed by S2-057. Qualys customers can use QID: 371151 and 13251 to detect vulnerable machines.
Qualys Detection
QID: 371151 is an authenticated check reads the tomcat location from tomcat server record. The QID extracts struts-core.x.jar to obtain the version information.
QID: 13251 sends a custom payload to the target machines and checks for command execution in .action, .go,.do,.jsp .xhtml files under common web directories. The authenticated check executes ‘ps -ef’ to check for tomcat process and locates struts2-core-x.jar, it extracts to find version information. QID 13251 will not flag on custom applications. Please QID 371151 for custom application.
Updates
– CVE-2018-11776 exploited in the wild to install CNRig miner
Please continue to follow Qualys Threat Protection for more information on various vulnerabilities.
Update:
– QIDs released.
– Remote detection added via QID: 13251
References
CVE-2018-11776
S2-057
CVE-2018-11776: How to find 5 RCEs in Apache Struts with Semmle QL
Code fixes