A remote code execution vulnerability exists because Windows Shell improperly handles URIs. Upon successful exploitation an attacker can achieve remote code execution via the Microsoft Edge browser. CVE-2018-8495 has been assigned to track this vulnerability. An attacker can leverage the vulnerability by abusing URI schemes and VBS script in Windows that can run with user-defined parameters. Microsoft has addressed this issue in the October 2018 patch release.
Vulnerability:
In Windows Registry, Windows Script Host (‘WScript.exe’) could execute scripts in multiple languages. Per Microsoft, “Windows Script Host provides an environment in which users can execute scripts in a variety of languages that use a variety of object models to perform tasks”.
A PoC has been released that exploits this vulnerability to launch calc.exe:
<a id="q" href='wshfile:test/../../WinSxS/AMD921~1.48_/SyncAppvPublishingServer.vbs" test test;calc;"'>test</a>
window.onkeydown=e=>{
window.onkeydown=z={};
q.click()
}
PoC shows that the SyncAppvPublishingServer.vbs file accepts a few arguments passed to it and these arguments can be crafted to trick the VBS script into executing arbitrary commands.
Proof of code is composed of HTML and JavaScript, so it could be be hosted on any website. Any seasoned attacker can modify this code to trigger more dangerous operations on the target system. An attacker could pass multiple arguments to ‘WScript.exe’ as Microsoft Edge did not sanitize quotation marks properly. Upon executing in Microsoft Edge, the operating system will ask the user for Windows Script Host (WSH) to handle the procedure, which has only the ‘OK’ button.
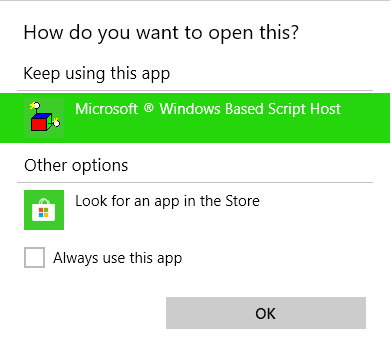
User interaction is required to exploit this vulnerability. In order to exploit this vulnerability, user must visit a malicious web page and tricked into accepting the prompt.
Mitigation:
We request customers to apply the latest patches provided by Microsoft to address CVE-2018-8495. Qualys customer can scan their network using QID: 91474 to detect vulnerable machines.
References & Sources:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8495
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/wscript
https://github.com/whereisr0da/CVE-2018-8495-POC
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8495