Atlassian Jira Server and Data Center is vulnerable to a server-side template injection in various resources. This vulnerability was introduced in version 4.4.x and affects versions as recent as 8.2.2 (released on 13 June 2019). CVE-2019–11581 has been assigned to track this vulnerability. Thousands of Jira Servers are potentially affected by this vulnerability and may be exploited in a wild by attackers in upcoming days.
Vulnerability Details:
The template injection vulnerability exists within the ContactAdministrators and SendBulkMail actions in Jira Server and Data Center. However, in order to exploit the vulnerability, an SMTP server needs to be configured, and either the Contact Administrators Form needs to be enabled (for unauthenticated attack), or the attacker has “JIRA Administrators” access (for authenticated attack). The exploitation of this vulnerability would grant an attacker the ability to remotely execute code on the vulnerable Jira system.
Proof of concept:
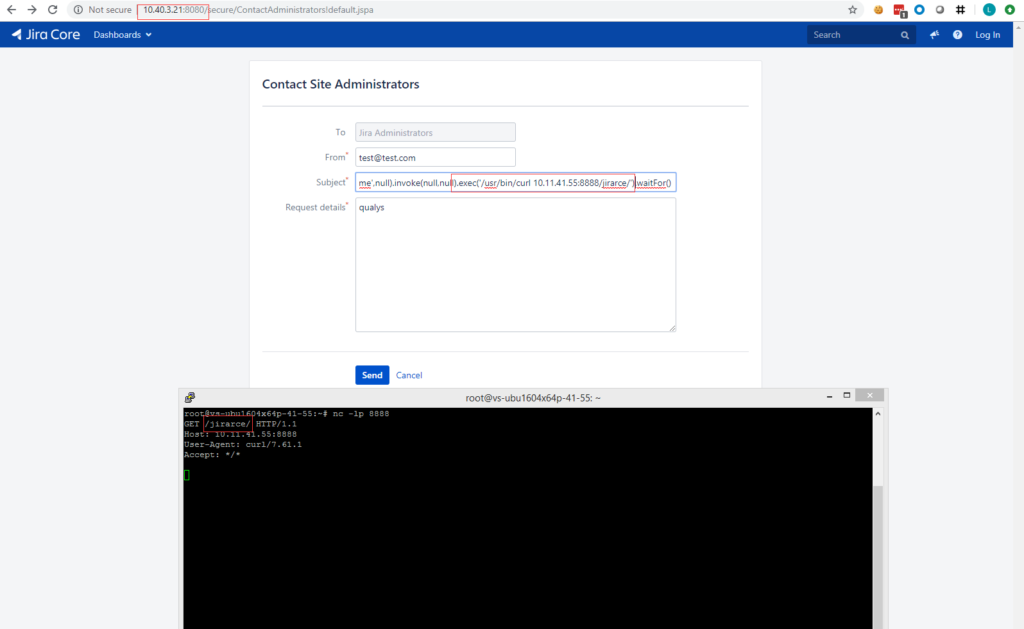
Mitigation:
Atlassian has addressed this issue in JIRA Security Advisory 2019-07-10.
Qualys has released a QID 13524 -Jira Server Template Injection Vulnerability (JIRA Security Advisory 2019-07-10) to detect the vulnerable machines.
Additionally, customers could disable the “Contact Administrators Form” as well as block access to the /secure/admin/SendBulkMail!default.jspa,to mitigate this issue if updating the current version is not feasible as of now.
Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.