Summary:
A remote code execution vulnerability has been reported in Atlassian Crowd and Crowd Data Center. The vulnerability is due to pdkinstall development plugin is incorrectly enabled in release builds.
Description:
Atlassian Crowd, a user management application for access control for Active Directory (AD), Lightweight Directory Access Protocol (LDAP)OpenLDAP and Microsoft Azure AD.
A remote, unauthenticated attacker could exploit this flaw to install arbitrary plugins by sending unauthenticated or authenticated requests to vulnerable Crowd or Crowd Data Center instances, which could grant them the ability to execute code. Successful exploitation results in the installation of arbitrary plugins on the target server, leading to remote code execution. This vulnerability leads to server compromise and can be defined under CWE-20.
At, Qualys labs we have tried to generate a presentation of how the RCE is gained , following a reference. According to the reference, CVE-2019-11580 can be exploited in a series of steps. Following steps will walk one through of how RCE is observed on Atlassian Crowd.
- Let’s start by setting up a vulnerable version of Atlassian Crowd.
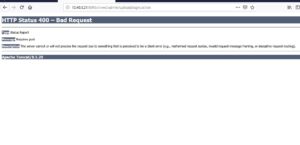
2. Ensuring that we can invoke the pdkinstall plugin by visiting http://localhost:8095/crowd/admin/uploadplugin.action. That should be 400 bad request from server.
3. Attempt to upload a standard plugin with the applinks-plugin from the atlassian-bundled-plugins. The servlet requires a POST request containing multipart data that contains a file that starts with the name file_. We can do this easily with cURL’s –form flag.
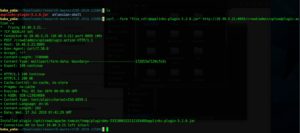
From the above result one can observe that the plugin has been successfully installed, henceforth, we can create as well as install our own plugin.
4. Thereby, compiling a malicious plugin
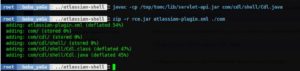
5. Uploading the malicious plugin using cURL and adding header Content-Type: multipart/mixed in order to get the execution.
curl -k -H “Content-Type: multipart/mixed” –form “file_cdl=@rce.jar” http://localhost:8095/crowd/admin/uploadplugin.action -v
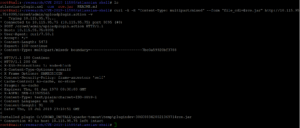
6. The malicious plugin was successfully installed as can be seen in the above image, and while trying to invoke it via browser, tadaaaaaaa., we have a pre-auth RCE on Atlassian Crowd!
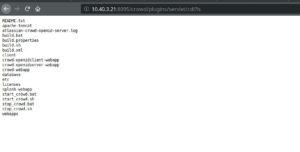
Affected Products:
Vulnerable software versions (2.1.0 – 3.0.4, 3.1.0 – 3.1.5, 3.2.0 – 3.2.7, 3.3.0 – 3.3.4, 3.4.0 – 3.4.3)
Release-notes:
https://confluence.atlassian.com/crowd/crowd-release-notes-199094.html
Mitigation:
Admins still running one of the vulnerable software versions should upgrade to Crowd and Crowd Data Center version 3.0.5, 3.1.6, 3.2.8, 3.3.5 or 3.4.4.
If that’s not possible, they can mitigate the issue by stopping Crowd, remove all instances of the pdkinstall plugin from the installation, and the starting Crowd again. Detailed steps on how to do that and a bash script that automates the mitigation steps on Linux systems can be found in Atlassian’s security advisory.
Atlassian recommends customers running a version of Crowd below version 3.3.0, upgrade to version 3.2.8 to avoid https://jira.atlassian.com/browse/CWD-5352, for customers running a version above or equal to 3.3.0 Atlassian recommends upgrading to the latest version.
Qualys customers can scan their network with QID#13525 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://www.corben.io/atlassian-crowd-rce/
- https://github.com/lc/research/tree/master/CVE-2019-11580/atlassian-shell