Cisco published an update for Cisco IOS XE operating system to patch a critical vulnerability that could allow a remote attacker to bypass authentication on devices running an outdated version of Cisco REST API virtual service container.
The security issue is tracked as CVE-2019-12643 and has received a maximum severity rating score of 10 based on CVSS v3 Scoring system.
The Vulnerability
This vulnerability exists in Cisco REST API virtual service container for Cisco IOS XE Software. Exploitation only requires malicious HTTP requests to the targeted device, that could allow an unauthenticated, remote attacker to bypass authentication on the managed Cisco IOS XE devices.
This vulnerability resides in the Cisco REST API virtual service container, however, it affects devices running Cisco IOS XE Software when exploited. A successful exploit could allow the attacker to obtain the token-id of an authenticated user. This token-id could be used to bypass authentication and execute privileged actions through the interface of the REST API virtual service container on the affected Cisco IOS XE device.
By default, Cisco REST API virtual service container is not enabled on Cisco IOS XE devices.
Detecting CVE-2019-12643
Qualys has issued QID 316494 for Qualys Vulnerability Management that covers CVE-2019-12643 for Cisco IOS XE. This QID is included in signature version VULNSIGS-2.4.689.
You can search for this new QID in AssetView or within the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.qid:316494
vulnerabilities.vulnerability.cveId:`CVE-2019-12643`
Qualys has also published an importable widget for tracking this vulnerability in the Qualys VM Dashboard Beta.
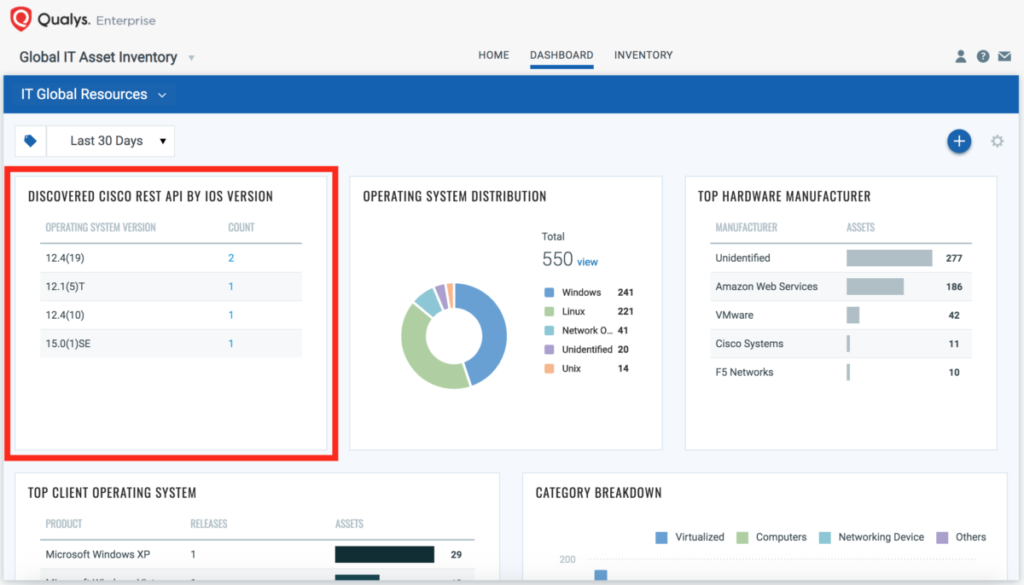
Using Qualys Global IT Asset Inventory to find IOS devices with Cisco REST API
If you are scanning all open ports, you can find any exposed Cisco Rest APIs by searching Qualys Global IT Asset Inventory with the following query:
operatingSystem.name:`Cisco IOS` and openPorts.port:55443
Or you could build a simple widget with the same query:
Remediation
To remediate this vulnerability, network admins should install latest Cisco REST API version 16.09.03 – “iosxe-remote-mgmt.16.09.03.ova”. Cisco has also released a hardened Cisco IOS XE Software release that prevents installation or activation of a vulnerable container on a device.
Detecting Cisco REST API Virtual Service Container is enabled on the Device –
router#show virtual-service detail | include Restful
Restful API Enabled, UP port: 55443
If this command does not exist, produces an empty output, or if the string Enabled, UP is absent, the device is not affected by the vulnerability described in this advisory.
Determine If the Device Is Using an Affected Cisco REST API Virtual Service Container Release –
router#show virtual-service version installed
Virtual service csr_mgmt installed version:
Name: csr_mgmt
Version: 16.09.
The “version:” number is used to identify the patched/unpatched release version.
If the output of this command shows a combination of virtual service name and version as unpatched release number, the device is using a vulnerable REST API virtual service container.