Summary:
A path traversal vulnerability has been reported in Grandnode. LetsEncryptController.cs in the Index action method is the vulnerable component., via which the server access the token validation URL, without authentication.
Description:
Grandnode is an open-source eCommerce solution powered by .NET Core 2.2, supporting Windows, Linux and Mac operating systems.
LetsEncryptController.cs method is used in the Let’s Encrypt HTTP challenge to validate domain ownership of the domain(s) in a certificate request. As part of the certification process, the ACME client will generate a token file on the webserver which will be publicly accessible from a URL. Grandnode exposes this URL by mapping this route to the LetsEncryptController.
Let’s Encrypt’s servers will attempt to retrieve this token file from the URL to perform validation and will issue a certificate if successful. This is accomplished via the [AllowAnonymous] attribute on the LetsEncryptController class., without the need to authenticate a user.
At, Qualys labs we have tried to generate a presentation. To retrieve the information from a Mac/Linux/Win machines, POC is publicly available. This vulnerability leads to client compromise and was considered under CVE-2019-12276.
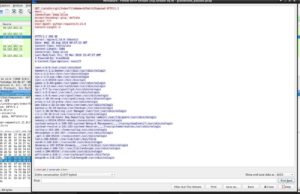
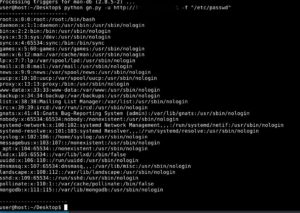
Affected Products:
Vulnerable GrandNode software versions prior to v4.40
Advisory:
https://github.com/grandnode/grandnode/releases
Mitigation:
A patch for this issue was made on GrandNode 4.40.
Qualys customers can scan their network with QID#13562 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://www.exploit-db.com/exploits/47027
- https://github.com/grandnode/grandnode/releases