Summary:
vBulletin 5.x are prone to remote code execution vulnerability. (CVE-2019-16759). It can be exploited without authentication and takes control of web hosts.
Description:
vBulletin is a proprietary Internet forum software package sold by MH Sub I, LLC doing business as vBulletin. It uses PHP and uses a MySQL database server.
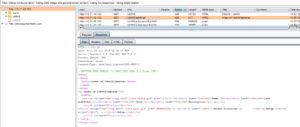
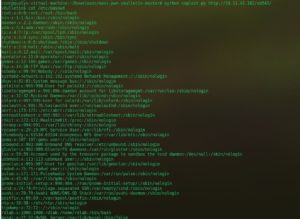
A pre-authentication remote code execution flaw (CVE-2019-16759) affecting vBulletin. A payload when generated and provided to vulnerable vbulletin, it response back to attacker and allows to command injection. On issuing a shell command as part of the injection by attacker, vBulletin will run Linux commands on its host with whatever user permissions vBulletins’ system-level user account has access to.
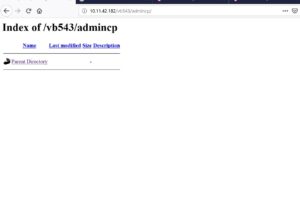
To find out if a site has been compromised, the researcher chybeta said to look for “ajax/render/widget_php” in the access logs. That’s because some of the parameters used in the attacks can be located on POST requests, which wouldn’t leave any traces in the logs.
At, Qualys labs we have tried to generate a presentation. To retrieve the information from vulnerable lab machines, POC is publicly available. This vulnerability leads to client compromise and was considered under CVE-2019-16759.
Affected Products:
Vbulletin versions , 5.0.0, 5.0.1, 5.0.2, 5.0.3, 5.0.4, 5.0.5, 5.1.0, 5.1.1, 5.1.2, 5.1.3, 5.2.0, 5.2.1, 5.2.2, 5.2.6, 5.4.3, 5.5.0, 5.5.1, 5.5.2, 5.5.3, 5.5.4
Advisory:
https://seclists.org/fulldisclosure/2019/Sep/31
Mitigation:
A patch for this issue was made on versions 5.5.2, 5.5.3 and 5.5.4
Qualys customers can scan their network with QID#13578 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://chybeta.github.io/2019/09/28/%E3%80%90CVE-2019-16759%E3%80%91-pre-auth-RCE-in-vBulletin-5-x/
- https://github.com/jas502n/CVE-2019-16759
- https://en.wikipedia.org/wiki/VBulletin