Summary:
A command-execution vulnerability is observed in a free open-source configuration management well-known as rconfig. It fails to filter the ‘rootUname‘ parameter passed to the ‘exec()‘ function of the ‘ajaxServerSettingsChk.php‘ file. It can be exploited by sending a crafted GET request to execute system commands.
Description:
The vulnerabilities (CVE-2019-16663, CVE-2019-16662) are both tied to rConfig version 3.9.2. CVE-2019-16662 allows an attacker to execute system commands on affected devices via GET requests, which can lead to command instructions.
It has been observed in the source code of rconfig 3.9.2 that all versions of it prior to that are also vulnerable.
Researchers have found that a botnet is used to scan for the vulnerability based on traffic of honeypots, and the origin hosts have been infected themselves. Active exploitation of the vulnerability was observed when the honeypot logs were analysed in detail. Over 300 different sources were observed in those logs, but only one exploit string was used. The exploit only verifies if a system is vulnerable.
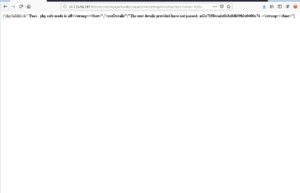
GET /install/lib/ajaxHandlers/ajaxServerSettingsChk.php?rootUname=%3Becho%20-n%20HellorConfig%7Cmd5sum%20%23
At, Qualys labs we have tried to generate a presentation. To retrieve the information from a lab environment machines, POC is publicly available. This vulnerability leads to client compromise and was considered under CVE-2019-16662 and classified as CWE-78.
Affected Products:
Rconfig version prior to 3.9.2
Advisory:
https://nvd.nist.gov/vuln/detail/CVE-2019-16662
Mitigation:
A patch for this issue was made on versions 3.9.3
It has been said by the rconfig researchers that in whichever versions prior to 3.9.2 the /install directory is mandatory, then and then only this vulnerability is likely to exploit, as the path to execute CVE-2019-16662 resides there.
Qualys customers can scan their network with QID#13602 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://shells.systems/rconfig-v3-9-2-authenticated-and-unauthenticated-rce-cve-2019-16663-and-cve-2019-16662/
- https://gist.github.com/mhaskar/ceb65fa4ca57c3cdccc1edfe2390902e
- https://nvd.nist.gov/vuln/detail/CVE-2019-16662
- https://isc.sans.edu/diary.html?date=2019-11-04