Today, Microsoft released patch for CVE-2020-0601, a vulnerability in windows “crypt32.dll” component that could allow attackers to perform spoofing attacks. This was discovered and reported by National Security Agency (NSA) Researchers. The vulnerability affects Windows 10 and Windows Server 2016/2019 systems.
This is a serious vulnerability and patches should be applied immediately. An attacker could exploit this vulnerability by using a spoofed code-signing certificate, meaning an attacker could let you download and install malware that pretended to be something legit, such as software updates, due to the spoofed digital signature.
Vulnerability Details:
The National Security Agency (NSA) discovered and reported this critical vulnerability (CVE-2020-0601) affecting Microsoft Windows cryptographic functionality.
The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution. The vulnerability affects Windows 10 and Windows Server 2016/2019 as well as applications that rely on Windows for trust functionality. Exploitation of the vulnerability allows attackers to defeat trusted network connections and deliver executable code while appearing as legitimately trusted entities. Examples where validation of trust may be impacted include:
- HTTPS connections
- Signed files and emails
- Signed executable code launched as user-mode processes
Exploits/PoC:
There are no reports of active exploitation or PoC available in public domain at this point of time. However, per NSA advisory “Remote exploitation tools will likely be made quickly and widely available.”
Detecting CVE-2020-0601 with Qualys VM
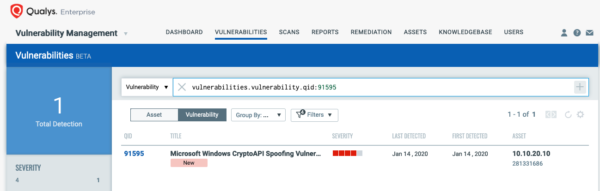
The best method for identifying vulnerable hosts is through the Qualys Cloud Agentor via Qualys authenticated scanning. Qualys has issued a special QID (91595) for Qualys Vulnerability Managementthat covers only CVE-2020-0601 across all impacted Operating Systems. This QID will be included in signature version VULNSIGS-2.4.791-3, and requires authenticated scanning or the Qualys Cloud Agent. Cloud Agents will automatically receive this new QID as part of manifest version 2.4.791-3-2.
You can search for this within AssetView or the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability:qid:91595
vulnerabilities.vulnerability.cveId:CVE-2020-0601
Mitigation
- Apply Windows OS Patches available for Windows 10, Windows Server 2016 and 2019 as soon as possible.
- Prioritize patching endpoints like – Web Servers, Domain Controllers, DNS Servers, proxies that perform TLS validation.
- Restrict external access to only trusted networks.
- Ensure that certificate validation is enabled for TLS proxies.
- See also DHS Emergency Directive 20-02: Mitigate Windows Vulnerabilities from January 2020 Patch Tuesday
Qualys customers can scan their network with QID#91595 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.