Summary:
In last week of February,2020, after MSPT, a serious vulnerability in Wi-Fi chips, formally known as CVE-2019-15126., very well known as Kr00K in the wild. Krook was hot topic to be discussed in RSA conference 2020.
Description:
What is Kr00k?
- Krook is a vulnerability of the wireless egress packet implementation and processing of certain Broadcom Wi-Fi chipsets. It affects unpatched devices with Wi-Fi chips by Broadcom and Cypress. A vulnerability that affects both WPA2-Personal and WPA2-Enterprise protocols, with AES-CCMP encryption, that causes vulnerable devices to use an all-zero encryption key to encrypt part of the user’s communication.
- Over a billion Wi-Fi-capable devices and access points, at a conservative estimate were affected.
An unauthenticated, attacker can decrypt Wi-Fi frames without the knowledge of the (WPA) or (WPA2) Pairwise Temporal Key (PTK) used to secure the Wi-Fi network.
To acquire Wi-Fi frames encrypted with the static PTK, there are two ways:
One, By injecting malicious packets disassociation event can be triggered into the wireless network and capturing the frames sent after the event. Second, listening to traffic in a passive manner from the wireless network and capturing the frames sent after a disassociation event.
The attack can be taken to a larger scale while a vulnerable AP is involved in the mix. For illustration, listening to a smart home hub or any IOT device can retrieve any information sent between AP and satellite devices and mobile devices.
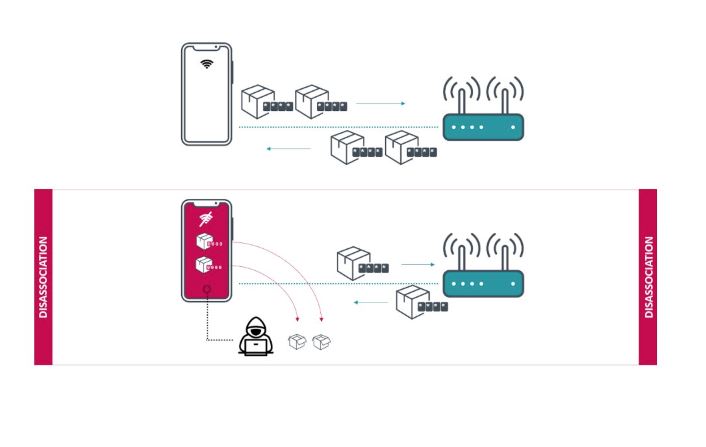
Image Source: GB Hackers
An attacker needs only to send a management frame to the access points AP and then can gain access to the whole environment. If an attack is successful, several kilobytes of potentially sensitive information can be exposed.
Kr00k is related to KRACK (Key Reinstallation Attacks), discovered in 2017 but is also fundamentally different.
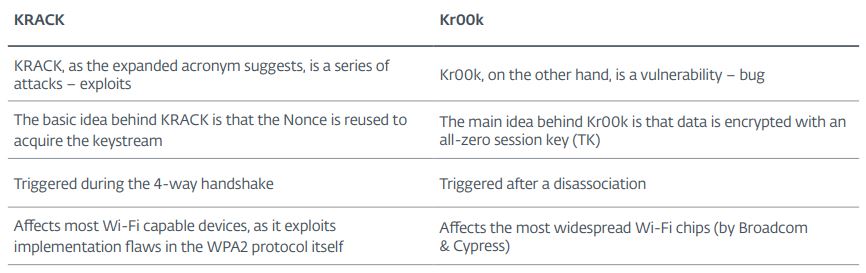
Image Source: GB Hackers
Affected Products:
The vulnerable chips are found in smartphones, tablets and laptops (using Broadcom silicon) and in IoT gadgets (Cypress chips) including several generations of products from:
- Amazon (Echo, Kindle)
- Apple (iPhone, iPad, MacBook)
- Google (Nexus)
- Samsung (Galaxy)
- Raspberry (Pi 3)
- Xiaomi (RedMi)
- Access points (APs) and routers by Asus and Huawei.
- Cisco multiple routers & other such devices.
Advisory:
https://support.apple.com/en-in/HT210722
Mitigation:
Qualys customers can scan their network with QID(s)# 372289, 13691, 610085 and 610065 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200226-wi-fi-info-disclosure
- https://threatpost.com/billions-of-devices-wifi-encryption-hack/153267/
- https://www.privateinternetaccess.com/blog/krook-wifi-vulnerability-affected-wifi-encryption-on-over-a-billion-devices/
- https://www.krackattacks.com/
- https://gbhackers.com/kr00k-vulnerability/