Summary:
During the past two weeks, we’ve seen a resurgence in attacks against WordPress plugins. Most of them have been briefed in below section.
Description:
Lets try to understand those 8 vulnerable plugins one by one.
Duplicator is one of the most popular plugins on the WordPress portal, with more than one million installs round the globe. A plugin that lets site administrators export the content of their sites.
The zero-day bug allows attackers to export a copy of the site, from where they can extract database credentials, and then hijack a WordPress site’s underlying MySQL server.
ThemeGrill Demo Importer plugin has been designed to allow WordPress site admins to import demo content, widgets, and settings from ThemeGrill, making it easier for them to quickly customize the theme.
There is a vulnerability that allows any unauthenticated user to wipe the entire database of targeted websites to its default state after which they are automatically logged in as an administrator. In the below screenshot, there is no authentication check, and only the do_reset_wordpress parameter needs to be present in the URL on any ‘admin’ based page of WordPress, including /wp-admin/admin-ajax.php. This vulnerability was classified under Broken Authentication and Session Management.
Easy to use profile plugin for creating front-end login, user registration and edit profile forms by using shortcodes. Profile Builder lets you customize your website by adding a front-end menu for all your users, giving them a more flexible way to modify their user profile or register.
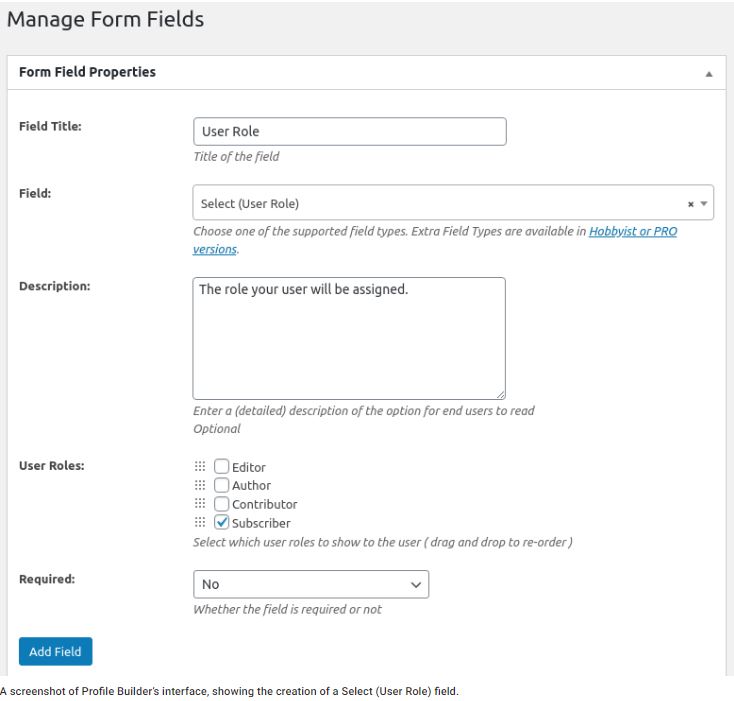
Image Source: WordPress
There’s also another major bug in the free and pro versions of the Profile Builder plugin. The bug can allow hackers to register unauthorized admin accounts on WordPress sites. Unfortunately, a bug in the form handler made it possible for a malicious user to submit input on form fields that didn’t exist in the actual form. Specifically, if the site’s administrator didn’t add the User Role field to the form, an attacker could still inject a user role value into their form submission.
To patch this bug, the developers created the validation function wppb_field_exists_in_form(). This validation is now used in the handler function of each possible form field, preventing the injection of unintended values.
Flexible Checkout Fields for WooCommerce
An e-commerce plugin for WordPress. With this plugin you can edit the default fields (change labels, hide, delete) or add your own. Flexible Checkout Fields beautifully integrates with the WordPress dashboard and it can be done as:
The site admin must visit the plugin configuration screen (WooCommerce → Checkout Fields) or the checkout page. Then the following admin accounts are being created:
—————————————————————-
wptest_dev1: wp*********@xy*.com
wptest_dev2: wp*********@xy*.com
woo_developdevacc: wo***************@xy*.com
developer_test_user: de*****************@ex*****.com
—————————————————————-
The Woo-Add-To-Carts.zip file is being downloaded thereafter, placed in /wp content/uploads/2020/02/ directory and then being installed using WordPress default mechanisms which in turn results in extracting its .php files to /wp-content/plugins/Woo-Add-To-Carts/. After that it is visible on the installed plugins list and is treated as a standard WordPress plugin called Woo-Add-To-Carts.
A zero-day exploit in this plugin allowed attackers to inject XSS payloads, which could then be triggered in the dashboard of a logged-in administrator. Attackers used the XSS payloads to create rogue admin accounts.
ThemeREX Addons is a plugin installed as a companion to many ThemeREX themes and provides several theme management features. One of the plugin’s functions registers a WordPress REST-API endpoint. When doing so, it does not verify that a request is coming from an administrative user.
A zero-day exploit in this plugin, that comes with all ThemeREX commercial themes, allowed attackers to create rogue admin accounts. This flaw allows attackers to remotely execute code on a site with the plugin installed, including the ability to execute code that can inject administrative user accounts.
Eliminate Render-blocking Javascript in above-the-fold content with Async Javascript. Async JavaScript gives you full control of which scripts to add an ‘async’ or ‘defer’ attribute to or to exclude to help increase the performance of your WordPress website.
10Web Map Builder for Google Maps
The plugin is distinguished for its feature-packed free version, offering what are usually premium features free, such as unlimited number of responsive maps, geolocation feature, store locator, layers, unlimited markers, and more.
Modern Events Calendar is a responsive, mobile-friendly, FREE, and comprehensive events management plugin which is extremely user-friendly and well-designed for displaying the events calendar on the websites, ever easier. Modern Events Calendar has been created according to trending design methods and latest technology with attractive design based on practical concept of design.
The above mentioned last three plugins have got zero-days that were all stored XSS bugs like the one described above. All three received patches, but attacks began before the patches were available, meaning some sites were most likely compromised.
Affected Products:
WordPress plugins:
Duplicator, ThemeGrill Demo Importer, Profile Builder Plugin, Flexible Checkout Fields for WooCommerce, ThemeREX Addons, Async JavaScript, 10Web Map Builder for Google Maps, Modern Events Calendar Lite.
Advisory:
https://wordpress.org/plugins/duplicator/
https://wpvulndb.com/vulnerabilities/10071
https://wordpress.org/plugins/profile-builder/
https://www.wpdesk.net/blog/flexible-checkout-fields-vulnerability/
https://wordpress.org/plugins/async-javascript/
Mitigation:
Duplicator – patched in version 1.3.28
ThemeGrill Demo Importer – patched in version 1.6.3
Profile Builder Plugin – patched in version 3.1.1
Flexible Checkout Fields for WooCommerce – patched in 2.3.4
ThemeREX Addons – No patch has been issued for this bug., Affected Versions greater than 1.6.50
Async JavaScript – update to 4.6 or higher
10Web Map Builder for Google Maps – update to version 1.0.64
Modern Events Calendar Lite – Update to version 5.1.7
Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- ar.wordpress.org/plugins/profile-builder/
- nl.wordpress.org/plugins/flexible-checkout-fields/
- https://wpvulndb.com/vulnerabilities/10071
- https://wordpress.org/plugins/duplicator/
- https://wordpress.org/plugins/themegrill-demo-importer/
- https://www.owasp.org/index.php/Top_10-2017_A2-Broken_Authentication
- https://www.wordfence.com/blog/2020/02/zero-day-vulnerability-in-themerex-addons-plugin-exploited-in-the-wild/
- https://www.wordfence.com/blog/2020/02/site-takeover-campaign-exploits-multiple-zero-day-vulnerabilities/