Update June 9, 2020:
As of June 2020, CVE 2020-0796 was highlighted once again and too hot in the wild as it gave “SMBGhost pre-auth RCE abusing Direct Memory Access structs”. A researcher published a presentation of the same in his/her tweet entailed below. CISA said “Although Microsoft disclosed and provided updates for this vulnerability in March 2020, malicious cyber-actors are targeting unpatched systems with the new PoC, according to recent open-source reports,”
Credits & Source: Chompie
————————————————————–
This Patch Tuesday, Microsoft disclosed a remote code execution vulnerability in SMB 3.1.1 (v3) protocol. Even though initial release of the Patch Tuesday did not mention this vulnerability, details of the issue (CVE-2020-0796) were published accidentally in another security vendor’s post. Microsoft published security advisory ADV200005 and technical guidance soon after accidental disclosure of vulnerability. The exploitation of this vulnerability opens systems up to a ‘wormable’ attack, which means it would be easy to move from victim to victim.
The Vulnerability
A critical remote code execution vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 protocol handles certain requests. An unauthenticated attacker could exploit the vulnerability to execute arbitrary code on SMB server by sending a specially crafted packet to a targeted SMBv3 Server. To exploit the vulnerability against an SMB Client, an unauthenticated attacker would need to configure a malicious SMBv3 Server and convince a user to connect to it.
Affected Operating System:-
- Windows 10 Version 1903 for 32-bit Systems
- Windows 10 Version 1903 for ARM64-based Systems
- Windows 10 Version 1903 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
Currently, there is no patch available for this vulnerability. However, Microsoft has provided workarounds in security advisory by disabling SMBv3 compression and blocking the 445 TCP port on client computers and firewalls to prevent attackers from exploiting the vulnerability.
Detecting CVE-2020-0796 with Qualys VM
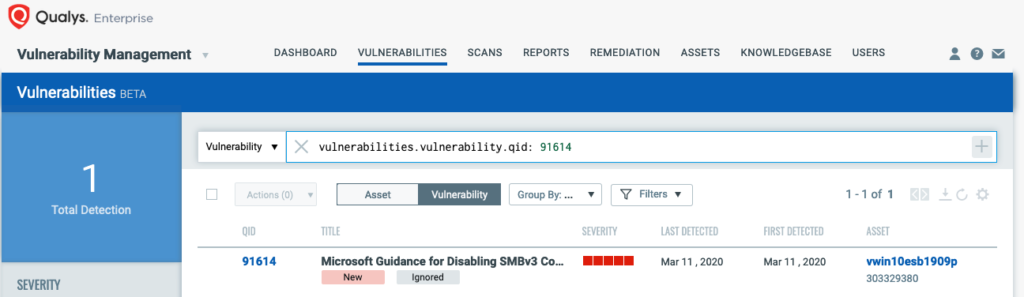
Qualys has issued QID -91614 for Qualys Vulnerability Management that covers CVE-2020-0796 across all impacted Operating Systems. This QID will be included in signature version VULNSIGS-2.4.837-4, and requires authenticated scanning or the Qualys Cloud Agent. Cloud Agents will automatically receive this new QID as part of manifest version 2.4.837.4-3.
QID 91614 : Microsoft Guidance for Disabling SMBv3 Compression Not Applied (ADV200005)
This QID checks if SMBv3 is enabled on the host and following workaround is applied –
“HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameter”;
DisableCompression -Type DWORD -Value 1
You can search for this within the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.cveIds:CVE-2020-0796
vulnerabilities.vulnerability.qid:91614
Workaround
- Disable SMBv3 compression
You can disable compression to block unauthenticated attackers from exploiting the vulnerability against an SMBv3 Server with the PowerShell command below –
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” DisableCompression -Type DWORD -Value 1 -Force
- Block TCP port 445 at the enterprise perimeter firewall
TCP port 445 is used to initiate a connection with the affected component. Blocking this port at the network perimeter firewall will help protect systems that are behind that firewall from attempts to exploit this vulnerability.
References & Sources:
- https://github.com/Dhoomralochana/Scanners-for-CVE-2020-0796-Testing
- https://twitter.com/chompie1337/status/1267327689213517825
- https://twitter.com/i/status/1249904222490918917
- https://ricercasecurity.blogspot.com/2020/04/ill-ask-your-body-smbghost-pre-auth-rce.html
- https://twitter.com/hugeh0ge
- https://www.us-cert.gov/ncas/current-activity/2020/06/05/unpatched-microsoft-systems-vulnerable-cve-2020-0796
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0796