Summary:
An arbitrary file move vulnerability is found in Windows Service Tracing. A privilege escalation vulnerability exists in the way that the Windows Kernel handles objects in memory. An attacker who successfully exploited the vulnerability could execute code with SYSTEM level permissions.
Description:
To exploit the vulnerability, developed by individual researcher Clément Labro, a locally authenticated attacker could run a specially crafted application. Service Tracing provides some basic debug information about running services and modules. It can be configured by any local user, simply by editing some registry keys and values under HKLM/SOFTWARE/Microsoft/Tracing.
A service or module is associated to a registry key. Each key contains 6 values (i.e. settings).
– EnableFileTracing
– FileDirectory
– MaxFileSize
Once EnableFileTracing is enabled, the target service will start writing to its log file in the directory of your choice. As soon as the size of the output file exceeds MaxFileSize, it will be moved (the .LOG extension is replaced by .OLD) and a new log file will be created.
Using AccessChk from the Windows Sysinternals tools suite, we can see that regular Users have Read/Write permissions on almost all the sub-keys.
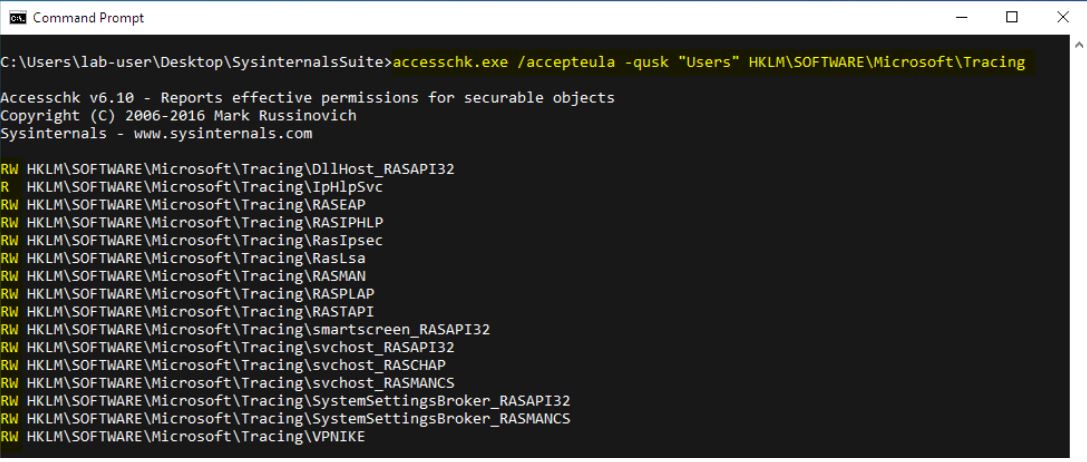
Image Source: itm4n.github.io
Firstly, Create a file with a size greater than 0x8000 (32,768) bytes. Create a new directory (C:/EXPLOIT/mountpoint/for example) and set it as a mountpoint to /RPC Control.
To enable tracing to the log file and give write permissions to it, an user must generate some events., that can be achieved by initiating a dummy VPN connection using the rasdial command and a PBK file.
Create the following symbolic links
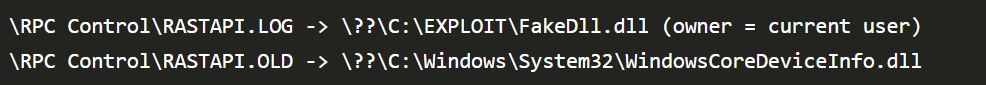
Image Source: itm4n.github.io
Configure the following values in the registry:
Image Source: itm4n.github.io
Trigger RASTAPI related events using the RasDial function from the Windows API.
Trigger the Update Session Orchestrator service to load the DLL in the context of NT AUTHORITY/SYSTEM.
Image Source: itm4n.github.io
There seems to be a copy operation, copied WindowsCoreDeviceInfo.dll, that checked printconfig.dll permissions.
Affected Products:
Windows Vista
Windows 10
Advisory:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0668
Mitigation:
The Microsoft advisory security update addresses the vulnerability by ensuring the Windows Kernel properly handles objects in memory.
Qualys customers can scan their network with QID(s)# 91605 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/Nan3r/CVE-2020-0668
- https://itm4n.github.io/cve-2020-0668-windows-service-tracing-eop/