Summary:
Oracle Coherence is a product in Oracle Fusion Middleware that enables organizations to scale mission critical application by providing them fast access to the frequently used data. Oracle Coherence is prone to Remote Code Execution vulnerability. This issue was assigned under CVE-2020-2555.
Description:
Oracle in their Advisory for January critical updates released patch for CVE-2020-2555 that affects Oracle Coherence that was vulnerable to Remote Code Execution through Insecure deserialization that allows unauthenticated attackers to attack through carefully constructed T3 network protocol requests. Successful exploitation of this vulnerability allows an attacker to execute arbitrary commands on the target host and compromise the server.
The vulnerability exploits two classes com.tangosol.util.extractor.ReflectionExtractor and com.tangosol.util.filter.LimitFilterexists in coherence.jar library. The chain details are as follows:
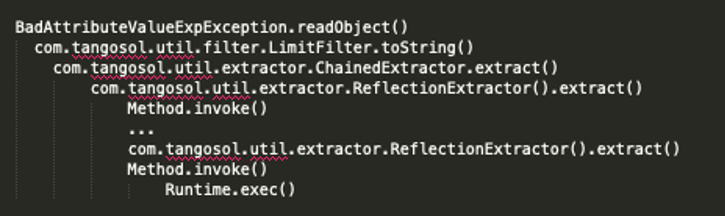
Image Source: thezdi
GadgetChain has source is BadAttributeValueExpException.readObject () -> toString (). Ideally, multiple method calls is required to achieve remote code execution. For example,in Apache Commons Collections gadgets rce is achieved by chaining arbitrary method invocation using ChainedTransformer. In same way, there is a class in the Coherence library that allowed to chain extract() calls, which is named as ChainedExtractor.
The patch released for CVE-2020-2555 had a change to the toString() method of the LimitFilter class.
Affected Products:
Oracle Coherence 3.7.1.17
Oracle Coherence & WebLogic 12.1.3.0.0
Oracle Coherence & WebLogic 12.2.1.3.0
Oracle Coherence & WebLogic 12.2.1.4.0
Exploitation:
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-2555 on Windows Server 2016 running vulnerable server. We’ve used a publicly available poc on github to exploit the target.
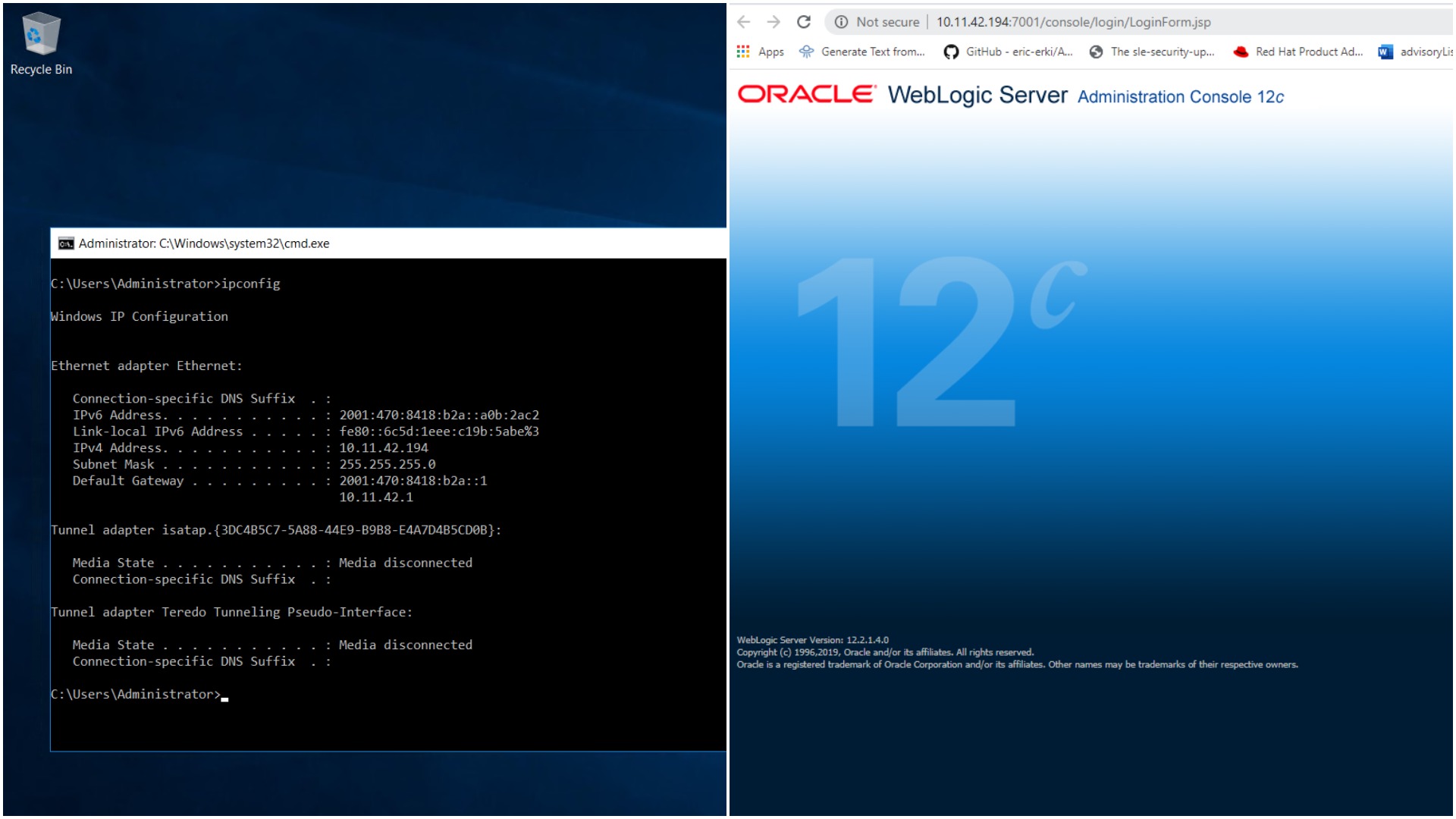
Server is up and running.

Run the python poc against the vulnerable server.
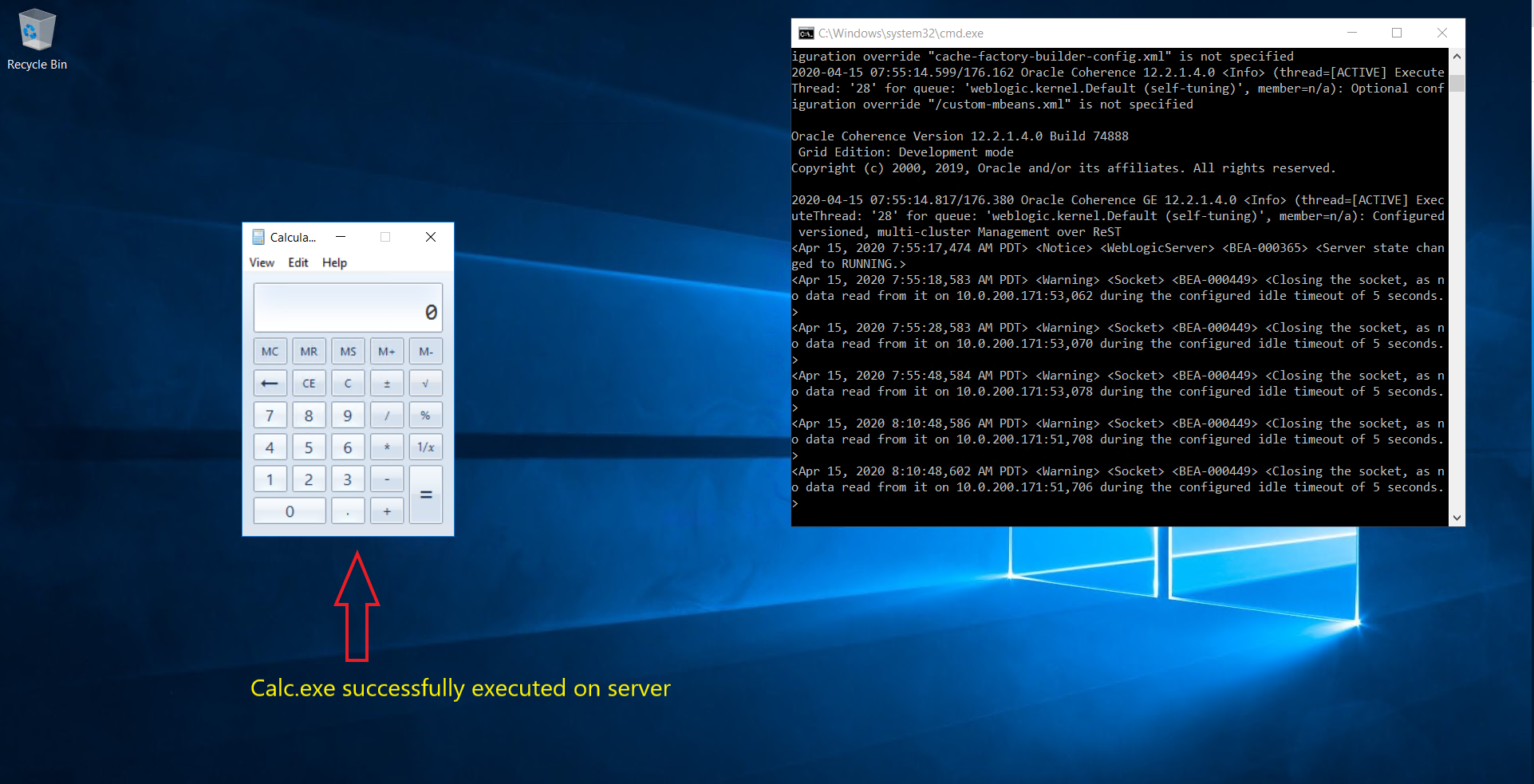
As we can see, the malicious code is executed successfully and calc.exe popped up on vulnerable the server.
Mitigation:
Oracle has officially released their official Advisory to patch the vulnerability. Customers are requested to update their Oracle Coherence & WebLogic versions.
Qualys customers can scan their network with QID(s)# 372345 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References:
- https://www.thezdi.com/blog/2020/3/5/cve-2020-2555-rce-through-a-deserialization-bug-in-oracles-weblogic-server
- https://github.com/wsfengfan/CVE-2020-2555
- https://www.oracle.com/security-alerts/cpujan2020.html