Summary:
An unusual buffer overflow vulnerability. that allows LPE was observed prior to April’s PT (patch-tuesday) in various Oracle Solaris platform. The researcher have published a POC publicly that was acclaimed by Oracle as well for CVE-2020-2944.
Description:
A buffer overflow in the _SanityCheck() function in the Common Desktop Environment version distributed with Oracle Solaris 10 1/13 (Update 11) and earlier allows local users to gain root privileges via a long calendar name or calendar owner passed to sdtcm_convert in a malicious calendar file.
As it does not ship the vulnerable binary, the open source version of CDE (based on the CDE 2.x codebase) is not affected.
A low privileged attacker with logon to the infrastructure where Oracle Solaris executes to compromise Oracle Solaris can result in takeover of Oracle Solaris servers.
The exploit of this RCE can be understood as:
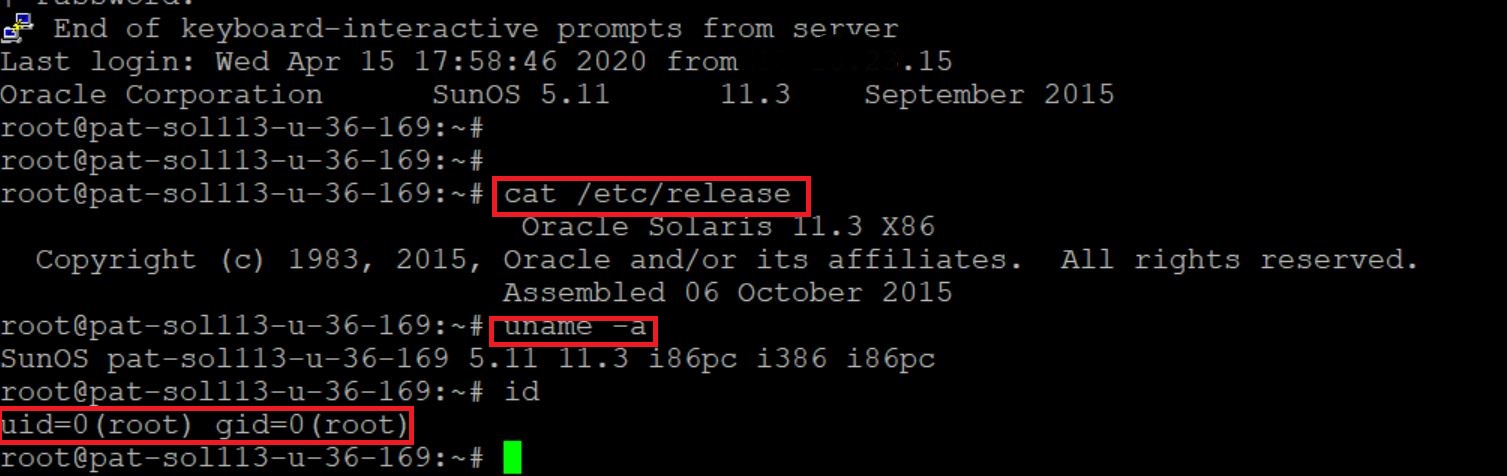
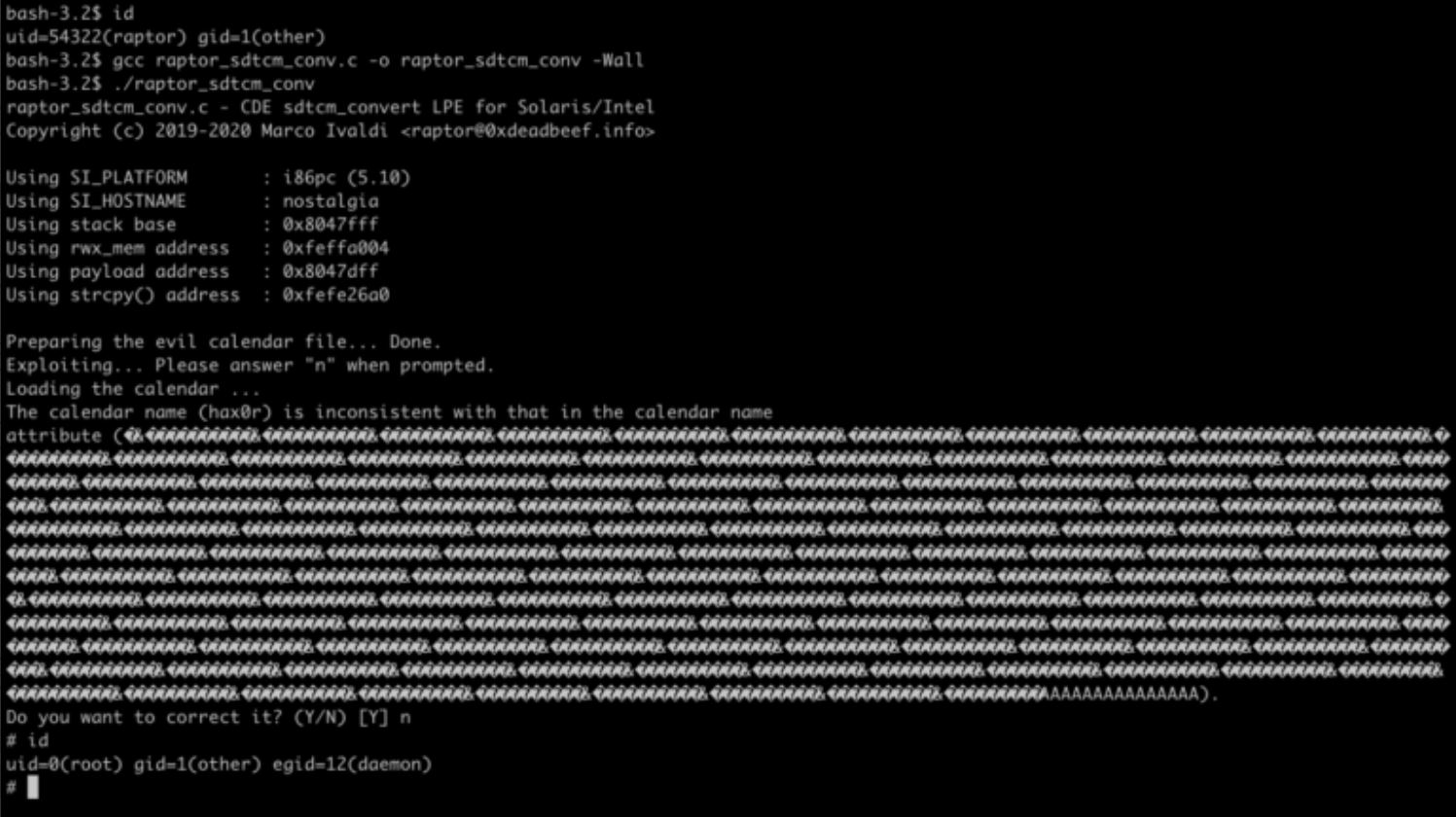
Image Source: techblog.mediaservice.net
Affected Products:
All platforms shipping the Common Desktop Environment based on the CDE 1.x codebase are potentially affected. This includes:
Oracle Solaris 10 1/13 (Update 11) and earlier [default installation]
Advisory:
https://www.oracle.com/security-alerts/cpuapr2020.html
Mitigation:
Oracle has assigned the tracking #S1239395 and has released a fix for all affected and supported versions of Solaris in the Critical Patch Update (CPU) of April 2020.
As a workaround, it is also possible to remove the setuid bit from the vulnerable executable as follows (note that this might prevent it from working properly):
bash-3.2# chmod -s /usr/dt/bin/sdtcm_convert
Removing the setuid bit from all CDE binaries is recommended, regardless of patches released by vendors.
Qualys customers can scan their network with QID(s)# 296042 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://cxsecurity.com/issue/WLB-2020040092
- https://github.com/0xdea/exploits/blob/master/solaris/raptor_sdtcm_conv.c
- https://www.oracle.com/security-alerts/cpuapr2020.html
- https://techblog.mediaservice.net/2020/04/cve-2020-2944-local-privilege-escalation-via-cde-sdtcm_convert/