Summary:
Recently, Apache ShardingSphereofficial release announcement of the 4.0.1 version. An authenticated attacker with default credentials can cause code execution when he/she submits a malicious yaml in the background management office. Classified as CWE-269, impacting confidentiality, integrity, and availability.
Description:
SnakeYAML library for parsing YAML inputs to load datasource configuration in ShardingSphere’s web console of Apache ShardingSphere(incubator) 4.0.0-RC3 and 4.0.0. SnakeYAML allows to unmarshal data to a Java type by using the YAML tag.
The manipulation as part of a YAML leads to a privilege escalation vulnerability resulting into Code Execution.
At Qualys Labs, we’ve tried to resolve the issue, reported for CVE-2020-1947.
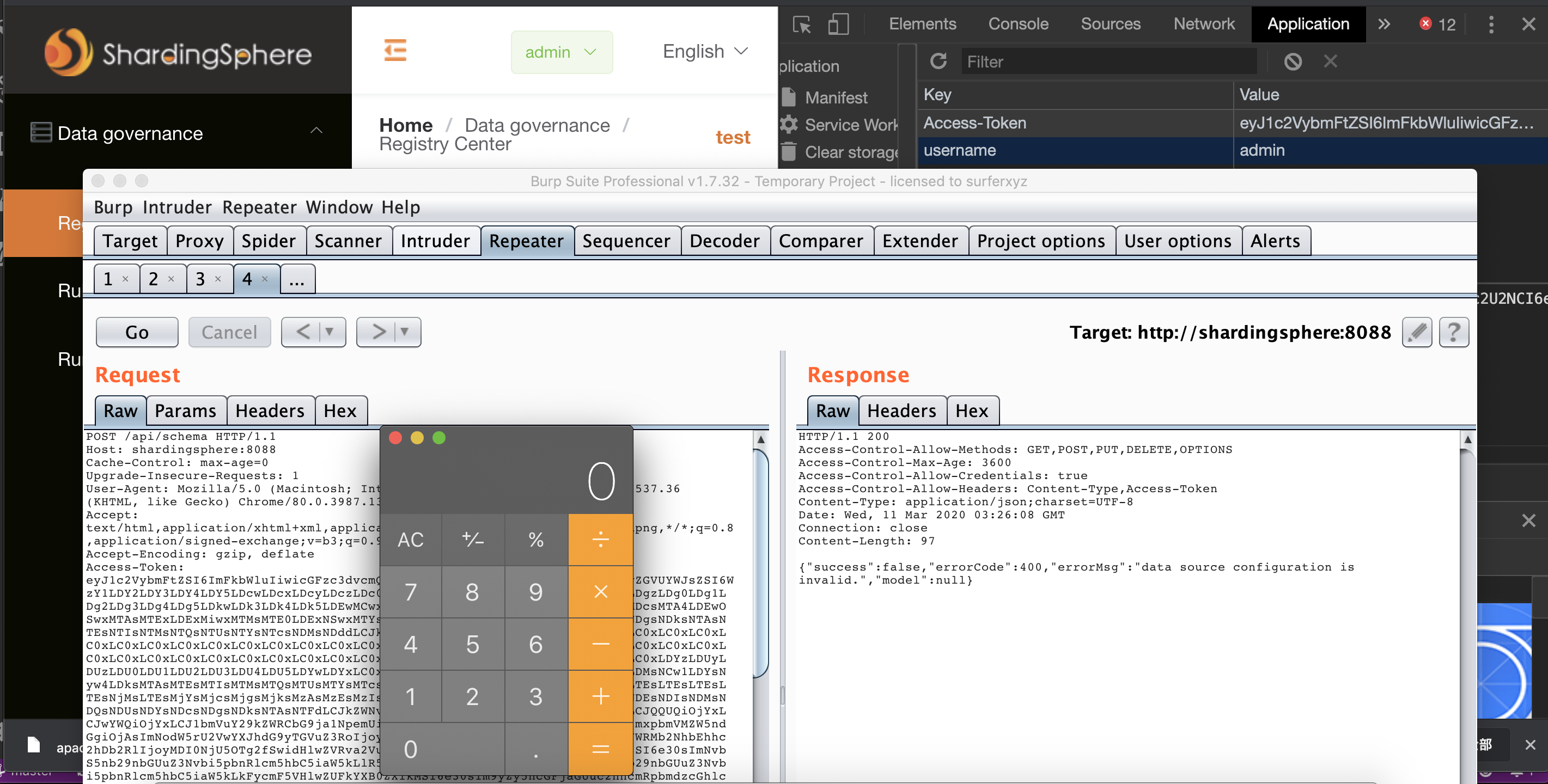
Login with default credentials : admin/admin

Sending a POST /api/schema request to ShardingSphere localhost with crafted Access-Token: resulting in code execution.
Affected Products:
Apache ShardingSphere & UI <= 4.0.0
Advisory:
Mitigation:
Manually, modifiy/conf/application.propertiesdefault credentials OR follow https://github.com/apache/incubator-shardingsphere/releases for the updates.
References & Sources:
- https://cwe.mitre.org/data/definitions/269.html
- https://nvd.nist.gov/vuln/detail/CVE-2020-1947
- https://github.com/Imanfeng/CVE-2020-1947
- https://github.com/wsfengfan/CVE-2020-1947
- https://github.com/apache/shardingsphere/releases