Summary:
Multiple vulnerabilities were observed in software development kit (SDK) of Autodesk products. Applications and Services that utilize the Autodesk FBX-SDK Ver. 2020.0 or earlier can be impacted by buffer overflow, type confusion, use-after-free, integer overflow, NULL pointer dereference, and heap overflow vulnerabilities.
Description:
This Autodesk vulnerabilities have a high severity, which if exploited, would directly impact the confidentiality, integrity or availability of user’s data or processing resources., resulting into either Code Execution or Denial of Service.
The details of the vulnerabilities are as follows:
- CVE-2020-7080: A user may be tricked into opening a malicious FBX file which may exploit a buffer overflow vulnerability in FBX’s SDK causing it to run arbitrary code on the system.
- CVE-2020-7081: A user may be tricked into opening a malicious FBX file which may exploit a type confusion vulnerability in FBX’s SDK causing it to read/write out-of-bounds memory location or run arbitrary code on the system or lead to denial-of-services.
- CVE-2020-7082: A user may be tricked into opening a malicious FBX file which may exploit a use-after-free vulnerability in FBX’s SDK causing the application to reference a memory location controlled by an unauthorized third party, thereby running arbitrary code on the system.
- CVE-2020-7083: The user may be tricked into opening a malicious FBX file which may exploit an integer overflow vulnerability in FBX’s SDK causing the application to crash leading to a denial of service.
- CVE-2020-7084: The user may be tricked into opening a malicious FBX file which may exploit a Null Pointer Dereference vulnerability in FBX’s SDK causing the application to crash leading to a denial of service.
- CVE-2020-7085: The user may be tricked into opening a malicious FBX file which would invoke the heap overflow vulnerable FBX parser to obtain a limited code execution by altering certain values in a FBX file, causing the application to run arbitrary code on the system.
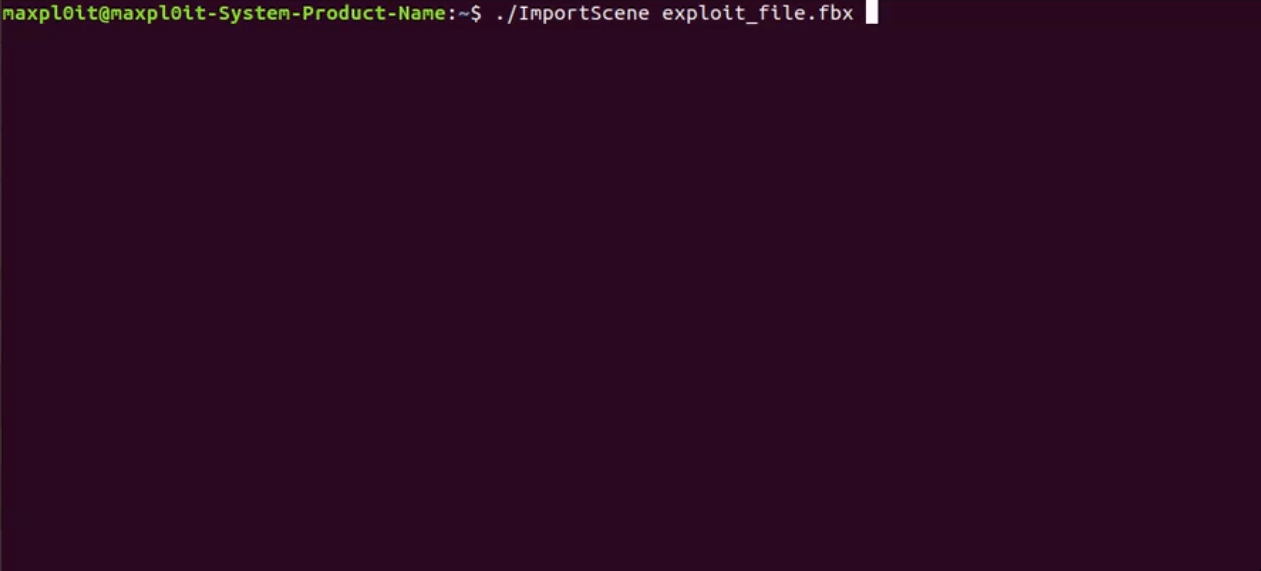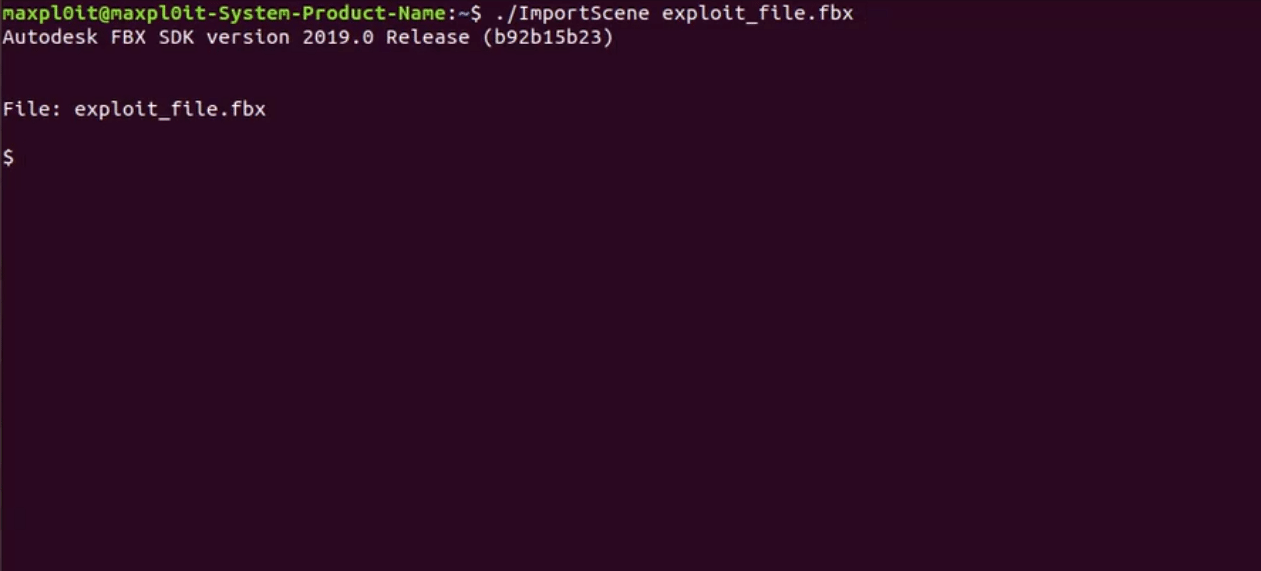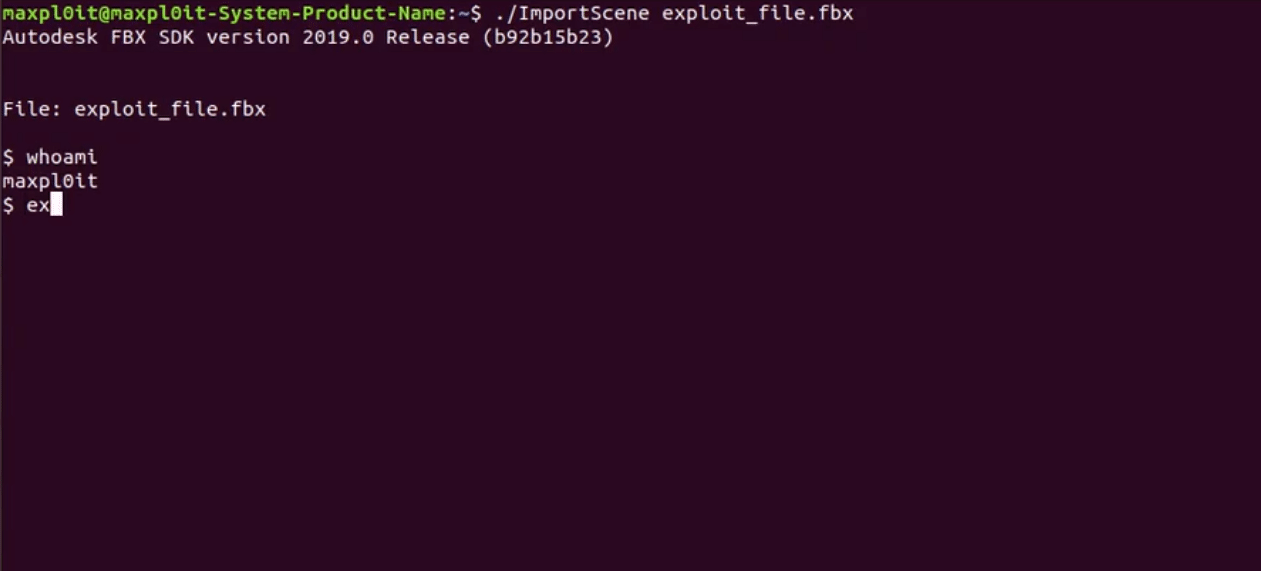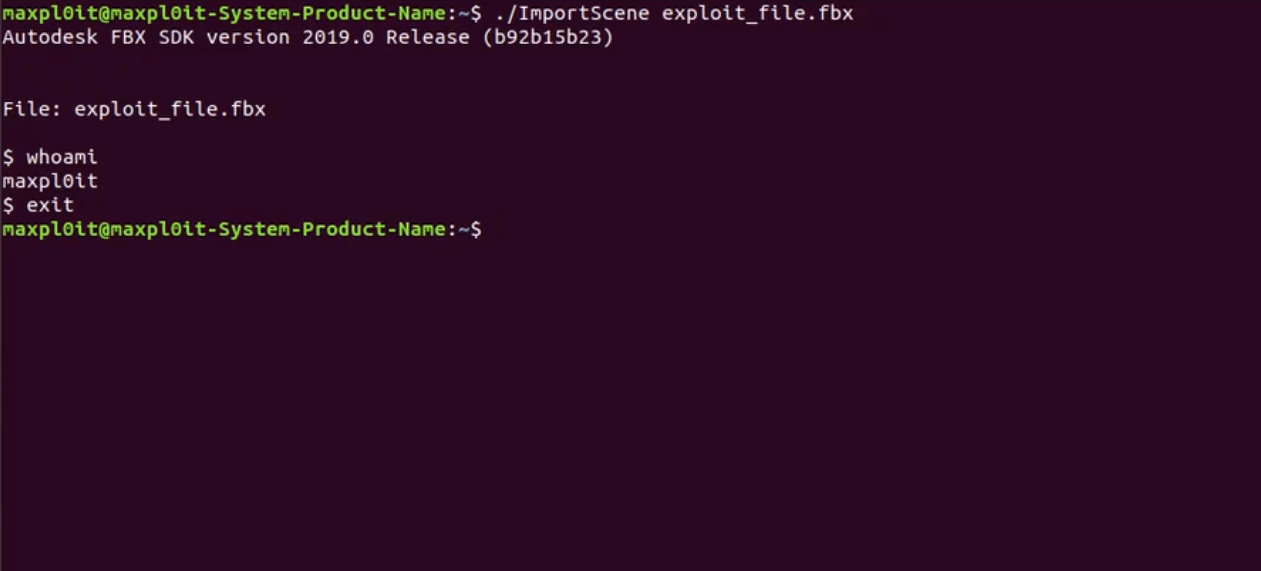
Image Source: maxpl0it https://twitter.com/maxpl0it/status/1251060962951659520
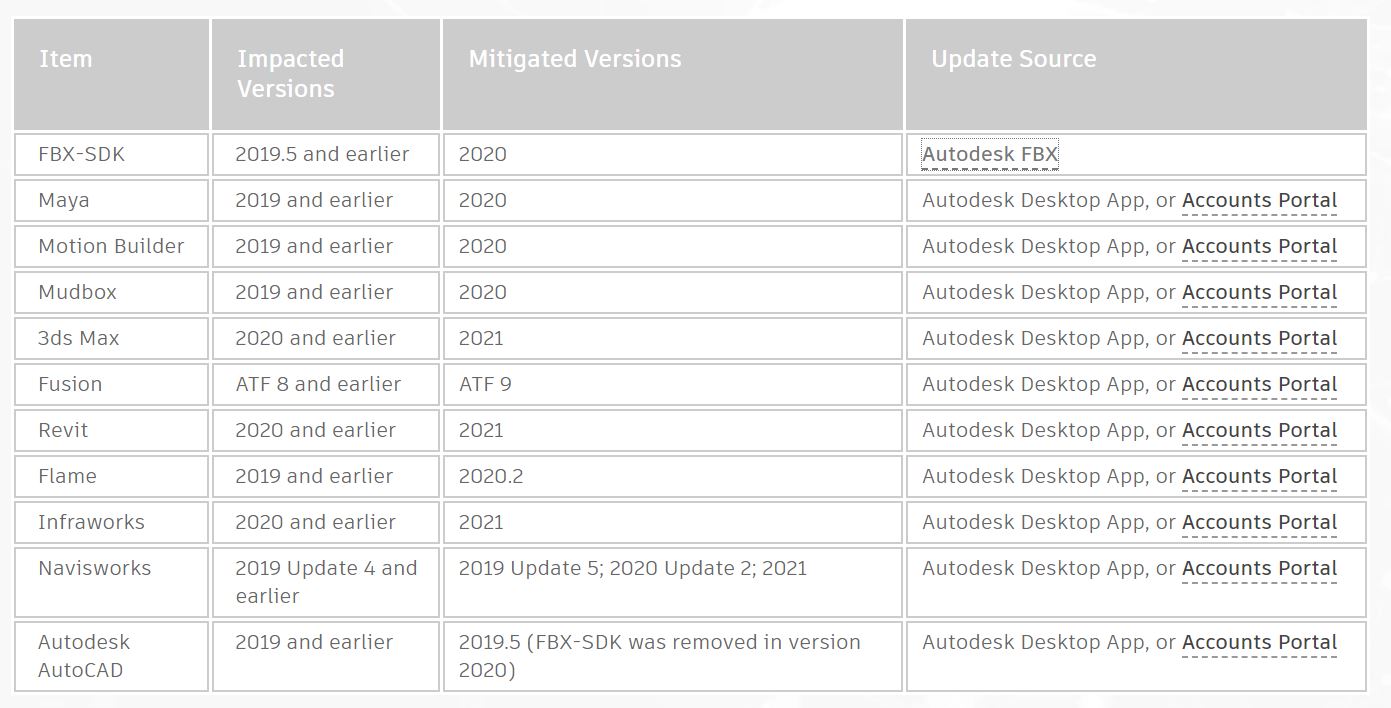
Affected Products:
Advisory:
https://www.autodesk.com/trust/security-advisories/adsk-sa-2020-0002
Mitigation:
Autodesk has updated the patch and released for above mentioned CVEs.
Customers of the affected products are advised to upgrade to the latest version via the Autodesk Desktop App or the Accounts Portal. For third party developers who use the FBX-SDK in their applications or services, Autodesk highly recommends they obtain and apply the latest version of the FBX-SDK from the update source listed above.
Qualys customers can scan their network with QID(s)# 372528 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://nvd.nist.gov/vuln/detail/CVE-2020-7080
- https://nvd.nist.gov/vuln/detail/CVE-2020-7081
- https://nvd.nist.gov/vuln/detail/CVE-2020-7082
- https://nvd.nist.gov/vuln/detail/CVE-2020-7083
- https://nvd.nist.gov/vuln/detail/CVE-2020-7084
- https://nvd.nist.gov/vuln/detail/CVE-2020-7085
- https://twitter.com/maxpl0it/status/1251060962951659520
- https://www.autodesk.com/trust/security-advisories/adsk-sa-2020-0002