Vulnerability Overview
Recently in the month of February 2020 Microsoft has released patches for 99 CVE’s. It was a large number of fixes in a single month. One of them being CVE-2020-0729 involving window LNK files, also known as shortcut files.
CVE-2020-0729 is a remote code execution vulnerability using windows shortcut files. What makes this vulnerability so interesting is that in past we have seen, exploits for vulnerabilities in LNK files have been used to spread malware such as the famed Stuxnet and, in most of the cases, simply browsing a folder containing a malicious LNK file, whether local or on a network share, is sufficient enough to trigger the vulnerability.
What are LNK files?
LNK file is a shortcut used by Windows as a reference to the original binary file, it also contains recent search items. Generally we search files using the “search-tool” tab, this search saves in the XML file having .search-ms extension.
LNK file structure
Image Source: thezdi
From the above image we can see the LNK file structure, for this vulnerability we will focus only on the “LeafCondition” structure which is vulnerable..
Vulnerability Description:
Let us now see how the “LeafCondition” structure is exploited. Leaf condition structure contains the attribute field PropertyVariant, used to define type and value of property. The parsing of PropertyVariant is handled by Function StructuredQuery1::ReadPROPVARIANT().
PropertyVariant starting 2 byte defines the type and followed by data. ReadPROPVARIANT Function checks if type is VT_ARRAY as its not supported in structuredQuery header.
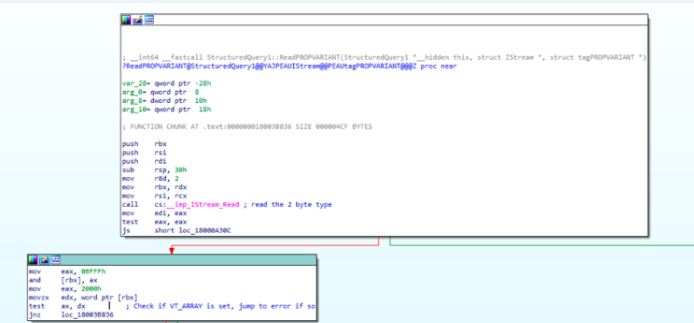
Image Source: thezdi
Then it checks if the type VT_UI4 is set, if not then enters a switch case to check different types.
The vulnerability occurs mainly due to the way PropertyVariant with type VT_VARIANT (0x000C) is handled.
The VT_VARIANT type is generally used in combination with VT_VECTOR which results in a series of PropertyVariant structures. When the type of the PropertyVariant is set to VT_VARIANT, the full type field is checked to see if VT_VECTOR is set.
Image Source: thezdi
If VT_VECTOR type is not set, a 24 byte buffer is allocated. Buffer is passed to a recursive function ReadPROPVARIANT(), the buffer will be filled with the property that immediately follows the VT_VARIANT field. Here is the main flaw, the buffer is not initialized before it is passed to ReadPROPVARIANT().
ReadPROPVARIANT() performs the same check for VT_VECTOR and if it is not set, attempts to write 4 byte in the previously allocated buffer. As the buffer is not initialized, the data will be written to an unexpected memory location. That can lead to an attacker’s ability to execute arbitrary code or command.
How this will Impact the users
If an attacker is successful to manipulate the memory layout and controls the uninitialized buffer, they can write any data 4 bytes at a time to a memory address of their choosing.
Affected version
- Windows 7, 8.1, and 10
- Windows Server 2008, 2012, 2016, and 2019
Solution:
To protect your system from attack, patch with recent update from Microsoft web page
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0729
Mitigation
Qualys Threat Research Lab provides protection with the QID(s)# 91605. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://www.thezdi.com/blog/2020/3/25/cve-2020-0729-remote-code-execution-through-lnk-files