Vulnerability overview
The Microsoft Windows Background Intelligent Transfer Service(BITS) is vulnerable to Elevation of Privilege. Vulnerability occurs due to incorrect handling of symbolic links.
Background Intelligent Transfer Service(BITS) is a Microsoft component used to transfer files using idle bandwidth.
Vulnerability Description
To check where vulnerability actually exists, we will first analyse the behaviour of Legacy BIT control class using the procmon.
While file transfer, BITS e takes two input parameters. First is target file \\127.0.0.1\C$\Windows\System32\drivers\etc\hosts and second one is local path C:\Temp\test.txt.
After taking the input parameters, it does the following activity –
- Creates a .TMP file with random name, in the destination folder and opens a local file.
- When Resume() function is called, service starts the reading data from the target file and writes it into tmp file C:\Temp\BITF046.tmp.
Operation performed in the first and second step, while impersonating the current user.
Image Source: itm4n.github - Finally, the function MoveFileEx() is called and the TMP file is renamed as test.txt. This operation performs under the NT AUTHORITY\SYSTEM account.
This is the main vulnerable part, where the actual vulnerability exists.
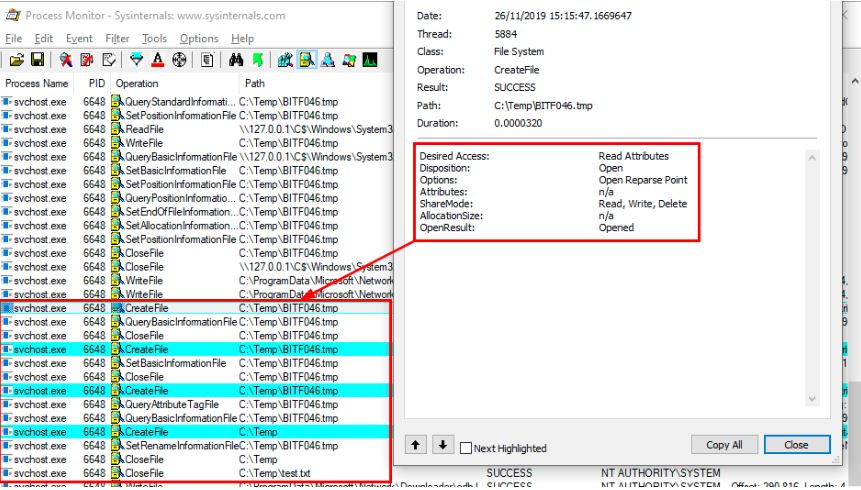
Image Source: itm4n.github
This results in Local Privilege Escalation. Attackers can now move malicious files to the System32 folder. A normal user may execute arbitrary code in the context of NT AUTHORITY\SYSTEM. We will see this in the final “Exploit” part.
Exploitation
This vulnerability is exploited by using junction and symbolic links.
A junction is an object that maps a directory into a different directory. Junction can be created by unprivileged users. They work across volumes, so you can redirect C:\Dir to D:\OtherDirectory as well.
Symbolic link is a file system object that points to other file system object. A non-admin user can create a symlink at the /RPC Control object directory.
Attack vector:
- First we will create the directory junction. We will use CreateMountPoint to create a junction from C:\workspace\mountpoint to C:\workspace\bait. So program which accessing mountpoint folder is actually opening bait folder. FakeDll.dll file will be move to the %system32% folder.

- Create a new job, with the following parameter.
 As we have created a junction, actual local file will be C:\workspace\bait\test.txt
As we have created a junction, actual local file will be C:\workspace\bait\test.txt - When adding a file to the job queue, the TMP file is immediately created in the bait folder. Put an oplock on the TMP file.
- As soon as the job is resumed, service will open a TMP file for writing data into it. Oplock will be triggered and block access to a file until we press enter to release the lock. This technique allows us to pause the operation, now we can create symbolic link.
- Create the symbolic link,
 After this step,
After this step,
- After releasing the lock, service starts writing to the TMP file C:\workspace\bait\BIT1337.tmp. After that the final MoveFileEx() call will be redirected because of the symbolic links. Therefore, our DLL will be moved to the System32 folder.With a simple command, we are able to have the BIT service run arbitrary code as NT AUTHORITY\System
Affected version:
- Microsoft Windows 8.1
- Microsoft Windows 10
- Microsoft Windows Server 2016
- Microsoft Windows Server 2019
Solution:
To protect your system from attack, patch with recent update from Microsoft web page
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0787
Mitigation:
Qualys Threat Research Lab provides protection with the QID(s)# 91609 . Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://itm4n.github.io/cve-2020-0787-windows-bits-eop/