Summary:
In the first week of May 2020,certain vulnerabilities have been observed that allows command injection in DrayTek devices. DrayTek manufactures firewalls, VPN devices, routers and wireless LAN devices. Successful exploitation could allow an attacker to manipulate and play on network traffic, escalated privileges or accounts even, operate SSH ans as such.
Description:
DrayTek Vigor enterprise switches as well as VPN gateway devices (affected versions mentioned below) have critical remote command injection vulnerabilities (CVE-2020-8515) and may lead to install backdoors.
keyPath and rtick are the two separate command injection points, located in the /www/cgi-bin/mainfunction.cgi, and the corresponding Web Server program is /usr/sbin/lighttpd. Due to lack of sufficient input control in either keyPath of rtick allowed command injection via formLogin() function & formCaptcha() function respectively.
The nefarious actor would prepend the payload with special characters like %27%0A to bypass the check and achieve pre-authentication command execution.
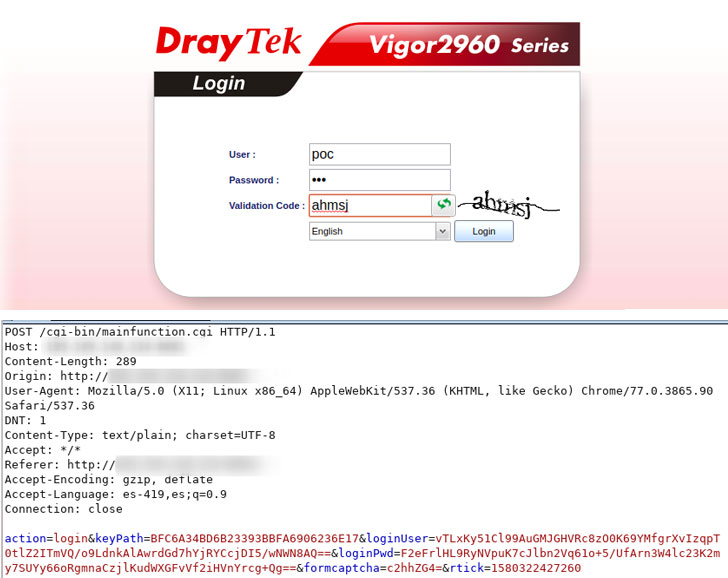
Image Source: SkullArmy
This issue has been fixed in Vigor3900/2960/300B v1.5.1.
Affected Products:
Vigor2960 < v1.5.1
Vigor300B < v1.5.1
Vigor3900 < v1.5.1
VigorSwitch20P2121 <= v2.3.2
VigorSwitch20G1280 <= v2.3.2
VigorSwitch20P1280 <= v2.3.2
VigorSwitch20G2280 <= v2.3.2
VigorSwitch20P2280 <= v2.3.2
Advisory:
Mitigation:
Draytek has updated the patch and released for CVE-2020-8515.
Qualys customers can scan their network with QID(s)# 13730 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/imjdl/CVE-2020-8515-PoC
- https://www.exploit-db.com/exploits/48268
- https://www.skullarmy.net/2020/01/draytek-unauthenticated-rce-in-draytek.html
- https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-draytek-products-could-allow-for-arbitrary-code-execution_2020-043/