Overview
On May 2020 Microsoft has released the patch for privilege escalation vulnerability present in Windows Print Spooler service.
The Print Spooler Service helps your Windows computer interact with the printer, and orders the print jobs in your queue.
To exploit this vulnerability attacker must have access to target system. The vulnerability is not remotely exploitable.
POC for this vulnerability is available on github
Description
For exploitation, we require just one single line of PowerShell command. Before looking into it, first understand how Printer is added and what happened internally.
To add any printer in your system basically require two things, printer port and driver. You can do this either using PowerShell command or through coding. We will use PowerShell commands to setup a printer.
To add Printer driver following command is used,
![]()
Check the list of drivers,
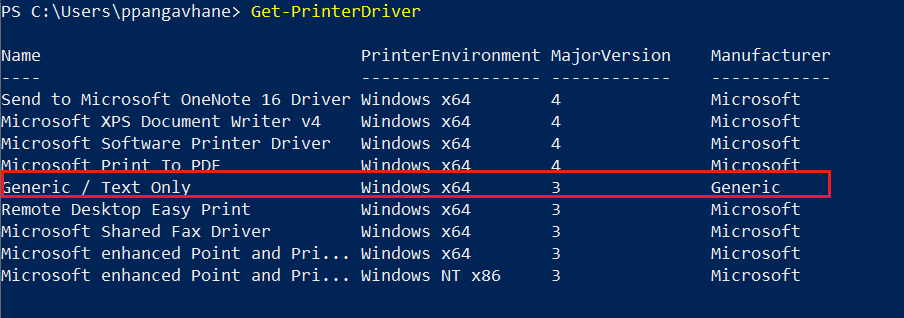
Add printer port using following command,
![]()
We have added driver and ports, now add printer using below command,
![]()
Let’s check Process monitor activity, to know how the port is internally added,
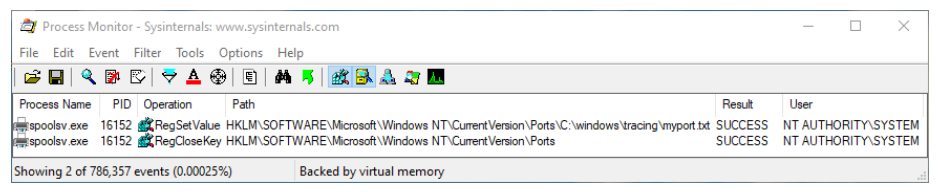
Image Source: windows-internals
From above image, port is added just by setting registry key to HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Ports.
We can add printer port in C using XcvData and AddPortW API.
Exploitation:
To Exploit this vulnerability use following single line powershell command,
![]()
As we discussed before, internally this command set registry key HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Ports value to “C:\windows\system32\ualapi.dll”. It will add persistent backdoor on your system. Now “print” any file having MZ header, it will install backdoor on system.
Exploitation doesn’t occurs due to powershell command. The code in github PoC, which uses XcvData with the AddPort command, directly gets the Spooler to add a port with zero checking.
Microsoft has fixed this vulnerability by adding PortIsValid check inside LcmXcvDataPort.
Affected Products:
- Windows 7, 8.1, and 10
- Windows Server 2008, 2012, 2016, and 2019
Advisory
To protect your system from attack, patch with recent update from Microsoft web page
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1048
Mitigation
Qualys Threat Research Lab provides protection with the QID(s)# 91636. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources: