Summary:
In February 2020, researchers reached out to Intel with a report on Thunderbolt, which they refer to as “Thunderspy”. The so-called Thunderspy attack takes less than five minutes to pull off with physical access to a device, and it affects any PC manufactured before 2019.
Description:
This Vulnerability is in fact new, and their attack uses only off-the-shelf components. The attack, called “Thunderspy,” specifically targets Thunderbolt technology, which is a hardware interface developed by Intel (in collaboration with Apple) that allows users to consolidate data transfer, charging and video peripherals into a single connector. While Apple first introduced Thunderbolt ports on its MacBook Pro in 2011, the technology has also been widely adopted with varying PCs such as Dell, HP and Lenovo. Researchers say all Thunderbolt-equipped devices manufactured before 2019 are vulnerable — meaning that there are millions of devices at risk.
The researcher, who came up with Thunderspy, have technique that can bypass the login screen of a sleeping or locked computer—and even its hard disk encryption—to gain full access to the computer’s data. And while his attack in many cases requires opening a target laptop’s case with a screwdriver, it leaves no trace of intrusion and can be pulled off in just a few minutes. That opens a new avenue to what the security industry calls an “evil maid attack,” the threat of any hacker who can get alone time with a computer in, say, a hotel room.
In 2019, major operating systems implemented Kernel Direct Memory Access (DMA) protection to mitigate against attacks such as these. This includes Windows (Windows 10 1803 RS4 and later), Linux (kernel 5.x and later), and MacOS (MacOS 10.12.4 and later). The SECURITY PARANOIACS did not demonstrate successful DMA attacks against systems with these mitigations enabled.
In Windows 10 version 1803, Microsoft introduced a new feature called Kernel DMA Protection to protect PCs against drive-by Direct Memory Access (DMA) attacks using PCI hot plug devices connected to Thunderbolt 3 ports. Drive-by DMA attacks can lead to disclosure of sensitive information residing on a PC, or even injection of malware that allows attackers to bypass the lock screen or control PCs remotely.
Apple’s Macs have offered Thunderbolt connectivity since 2011, but researchers say that they’re only “partially affected” by Thunderspy if they’re running macOS. The result, the report claims, is that macOS systems are vulnerable to attacks like BadUSB. This is a security flaw that emerged back in 2014 which can allow an infected USB device to take control of a computer, steal data, or spy on a user. The Thunderbolt flaw still leaves macOS devices vulnerable to some security workarounds, such as cloning the identity of a device on Apple’s peripheral whitelist to an attacker device. That could open the door to other types of exploits like BadUSB, which describes a series of port-based attacks delivered by malicious USB devices.
Unlike Thunderclap, the Thunderspy attacks break both Thunderbolt hardware and protocol security. Using the “evil maid” threat model, in which the attacker has physical access, as well as varying Security Levels, researchers created arbitrary Thunderbolt device identities, cloned user-authorized Thunderbolt devices, and obtained PCIe connectivity to conduct DMA attacks. They were able to disable Thunderbolt security entirely, he notes. The Thunderspy attacks reportedly break all primary security claims for Thunderbolt 1, 2, and 3.
All Thunderbolt-equipped systems shipped between 2011-2020 are exposed; however, some systems are only partially vulnerable. The flaws can’t be fixed with software, he adds. They will affect future standards such as the Thunderbolt 4 and USB 4, and they require silicon redesign.
Researcher Bj¨orn Ruytenberg who found this flaw, is also releasing a tool to determine if your computer is vulnerable to the Thunderspy attack, and whether it’s possible to enable Kernel DMA Protection on your machine.
Analysis of that claims that the firmware contains the security state of the controller, there are methods to change that security state to ‘none.’ So basically disabling all security. An attacker can then plug a device into the Thunderbolt port that alters its operating system to disable its lock screen, even if it’s using full disk encryption.
Those whose devices are lost or stolen, however, may have greater cause for concern. Thunderspy can crack password-protected laptops, which could put a great deal of sensitive data at risk if they fall into the wrong hands.
Affected Products:
Thunderbolt-enabled Windows or Linux PCs manufactured before 2019
Advisory:
https://blogs.intel.com/technology/2020/05/more-information-on-thunderspy/#gs.6gz632
Mitigation:
There is still no complete fix for this vulnerability, so specialists recommended that users disable Thunderbolt in BIOS/UEFI. Another viable option to mitigate the risks is to be careful with the peripheral hardware that connects to the ports of our machines, because these vulnerabilities require physical access to the equipment for its exploitation.
Devices that are at least partially protected include those manufactured with Kernel DMA protections, a security measure created by Intel after the Thunderclap flaws were disclosed.
- Beginning with Windows 10 version 1809, you can use Security Center to check if Kernel DMA Protection is enabled. Click Start > Settings > Update & Security > Windows Security > Open Windows Security > Device security > Core isolation details > Memory access protection.
- Using Sysinfo, Launch MSINFO32.exe in a command prompt, or in the Windows search bar.
- Check the value of Kernel DMA Protection.
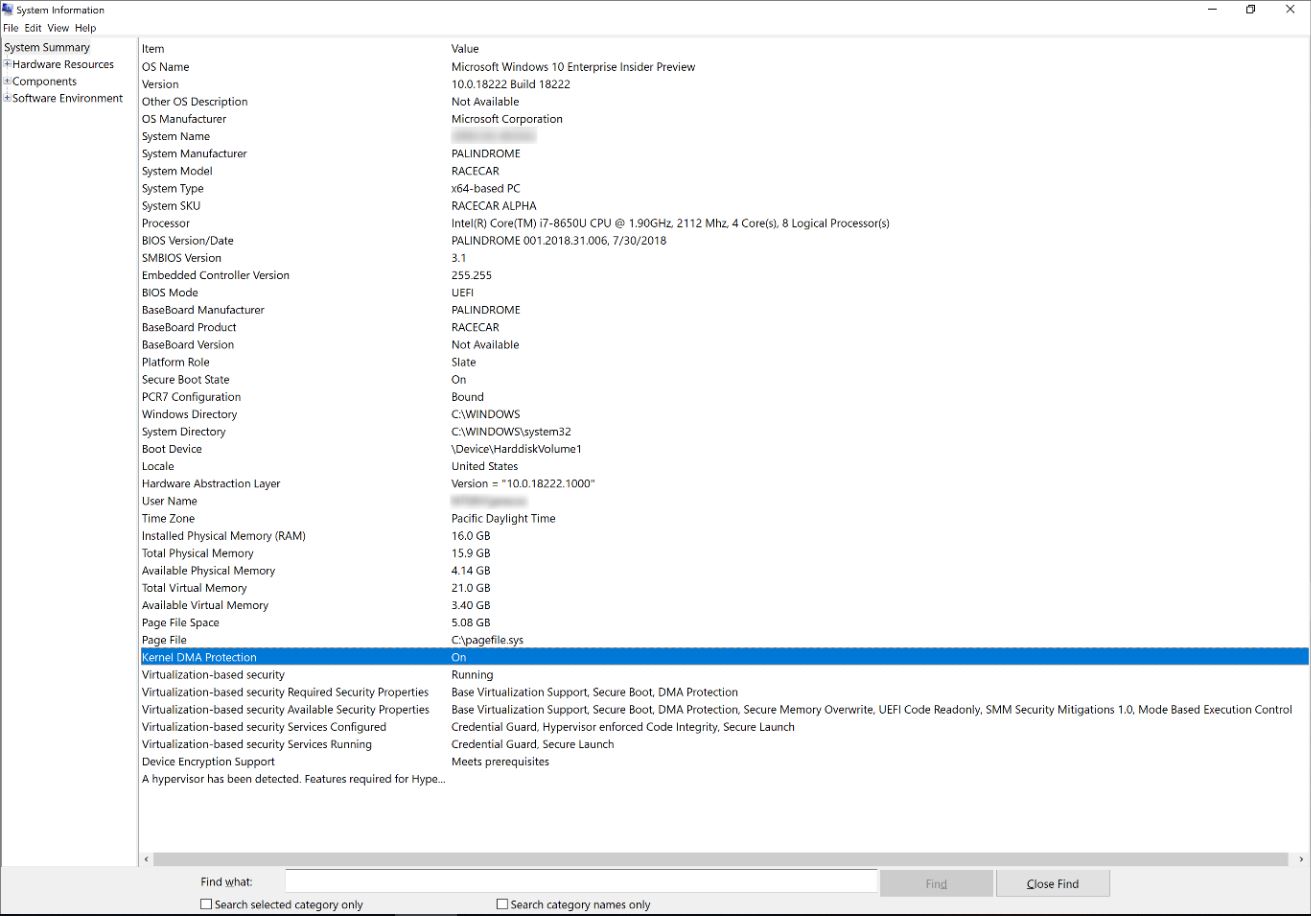
Image Source: Microsoft
- If the current state of Kernel DMA Protection is OFF and Virtualization Technology in Firmware is NO:
Reboot into BIOS settings
Turn on Intel Virtualization Technology.
- Turn on Intel Virtualization Technology for I/O (VT-d). In Windows 10 version 1803, only Intel VT-d is supported. Other platforms can use DMA attack mitigations described in BitLocker countermeasures.
- Reboot system into Windows 10.
NOTE: If the state of Kernel DMA Protection remains Off, then the system does not support this feature.
References and Sources:
- thunderspy.io/assets/reports/breaking-thunderbolt-security-bjorn-ruytenberg-20200417.pdf
- www.youtube.com/watch?v=loBX_vEXxVA
- www.blackhat.com/us-14/briefings.html#badusb-on-accessories-that-turn-evil
- https://www.darkreading.com/endpoint/thunderbolt-vulnerabilities-could-threaten-millions-of-pcs/d/d-id/1337789